just keep it CS0, this will set incoming dscp marks from internet to CS0(we don't trust isp dscp marks)
Thank you!
Now i'm facing something weird..this is my current firewall.user and i only set up youtube in the dnsmask.conf..
IPT="iptables"
#Clear interface dscp marks, we don't trust ISP marks(also to use our own marks).
$IPT -t mangle -A PREROUTING -i pppoe-wan -j DSCP --set-dscp 0
#Ping
$IPT -t mangle -A PREROUTING -p icmp -j DSCP --set-dscp-class CS6 ##dscp tag for ping packets
#Gaming
$IPT -t mangle -A PREROUTING -p tcp -m multiport --port 9339 -j DSCP --set-dscp-class CS6 #Brawl Stars
$IPT -t mangle -A PREROUTING -p udp -m multiport --port 9339 -j DSCP --set-dscp-class CS6 #Brawl Stars
$IPT -t mangle -A PREROUTING -p udp -m multiport --ports 49003:49006 -j DSCP --set-dscp-class CS6 #GeForceNow
$IPT -t mangle -A PREROUTING -p tcp -m multiport --port 49006 -j DSCP --set-dscp-class CS6 #GeForceNow
#Prova Youtube
$IPT -t mangle -A PREROUTING -m set --match-set vidstream src -j DSCP --set-dscp-class AF41
$IPT -t mangle -A PREROUTING -p tcp -m multiport --dport 1935 -j DSCP --set-dscp-class AF41
Why if i try to do a speedtest using fast.com, it tells me that it is AF41? 
When i try to download an app wireshark correctly shows me CS0
make ping CS5, and replace all PREROUTING to POSTROUTING !
who is told you about AF41? (fast.com)???
just trust wireshark!, you can use tcpdump (run it on br-lan after that run it on pppoe0)on router then open the generated pcap with wire shark and check marks!
Sorry i mean in Wireshark when i do a download test from that site, i see the inbound packets marked as AF41, only for that site, dslreports is CS0 as it should be ![]() From what i set only youtube videos should be AF41 am i right?
From what i set only youtube videos should be AF41 am i right?
Also why do i have to change to POSTROUTING?
first you have to flush the PREROUTING or POSTROUTING table before reapplying rules(so it won't duplicate).
Right, i think fast.com send packets marked as AF41 or it's your isp!
that's better cause it's have the packet processed and you will see right tags on inbound, so prerouting is not needed at all!
But it should be CS0 from this rule
$IPT -t mangle -A POSTROUTING -i pppoe-wan -j DSCP --set-dscp-class CS0
I've an headache ![]()
Btw again thank you so much for helping !
EDIT: The problem is in the youtube rule, if i change that to CS4 instead of AF41, fast.com traffic is marked CS4
$IPT -t mangle -A POSTROUTING -m set --match-set vidstream src -j DSCP --set-dscp-class CS4
Is it possible that fast.com uses the same domain googlevideo of youtube to deliver its speetest?
I did what dlakelan suggested and added 2 cake layers and installed the iptables script with the dscp markings on the ports. I just want to clean up firewall for gaming using iptables marking packets and controlling them.
example:
## game traffic
iptables -t mangle -A dscp_mark -p udp --sport 1119:1120 -j DSCP --set-dscp-class CS5
ip6tables -t mangle -A dscp_mark -p udp --sport 1119:1120 -j DSCP --set-dscp-class CS5
iptables -t mangle -A dscp_mark -p udp --dport 1119:1120 -j DSCP --set-dscp-class CS5
ip6tables -t mangle -A dscp_mark -p udp --dport 1119:1120 -j DSCP --set-dscp-class CS5
I would like these rules to be MAC source marked for the egress and ip destination marked for the ingress.
and I would also like to prioritize a single machine over all other network traffic using iptables
example:
gaming machine class CS5
all other network traffic CS0
I think you can just mark all packets from the given Mac or to the given IP. iptables has a -m mac match, and a dst match, see iptables manual
## icmp for egress mac and ingress IP gets CS5
iptables -t mangle -A dscp_mark -p icmp -m mac --mac-source 00:00:00:00:00:00 -j DSCP --set-dscp-class CS5
iptables -t mangle -A dscp_mark -p icmpv6 -m mac --mac-source 00:00:00:00:00:00 -j DSCP --set-dscp-class CS5
iptables -t mangle -A dscp_mark -p icmp -d 192.0.0.0 -j DSCP --set-dscp-class CS5
iptables -t mangle -A dscp_mark -p icmpv6 -d 192.0.0.0 -j DSCP --set-dscp-class CS5
## game traffic egress mac and ingress IP
iptables -t mangle -A dscp_mark -p udp --sport 1119:1120 -m mac --mac-source 00:00:00:00:00:00 -j DSCP --set-dscp-class CS5
ip6tables -t mangle -A dscp_mark -p udp --sport 1119:1120 -m mac --mac-source 00:00:00:00:00:00 -j DSCP --set-dscp-class CS5
iptables -t mangle -A dscp_mark -p udp --dport 1119:1120 -d 192.0.0.0 -j DSCP --set-dscp-class CS5
ip6tables -t mangle -A dscp_mark -p udp --dport 1119:1120 -d 192.0.0.0 -j DSCP --set-dscp-class CS5
If this is correct how do I set all other traffic on the WAN and/or LAN to CS0 or does that even matter now that the packets are prioritized?
its already CS0, if not:
iptables -t mangle -A dscp_mark -i pppoe0 -j DSCP --set-dscp-class CS0
use the same rule but change pppoe0 to br-lan
hisham2630 Thank you for the feedback
I'm sorry I asked the wrong question. Obviously the traffic is already tagged as normal traffic and shaped on the wan, lan through layer_cake and again through piece of cake on the lan on the ingress for wifi.
What I meant to ask was how would I assign 1 MAC address priority over all other WAN traffic through iptables? Maybe it does not matter as long as the UDP and ICMP is prioritized in iptables.
no problem, its all about what do you want to achieve, if you already prioritied ping and udp thats enough.
Why do i have "iptables v1.6.2: Couldn't load match `hashlimit':No such file or directory" while setting this rule in the script? Am i missing some packages?
$IPT -t mangle -A POSTROUTING -p udp -m hashlimit --hashlimit-name udp_high_prio --hashlimit-above 120/sec --hashlimit-burst 50 --hashlimit-mode srcip,srcport,dstip,dstport -j CONNMARK --set-mark 0x55 -m comment --comment "connmark for udp"
not in front of a router at the moment but just search packages for kmod related to Hashlimit. probably kmod-ipt-hashlimit or something similar
I will follow the second set of instructions setting up a veth pair. The first set I almost bricked my router lol.....
EDIT:
When layer_cake is enabled on pppoe-wan egress, eth0.1(lan) ingress my bufferbloat on both links stays under 10
When I:
add veth1 to br-lan
layer_cake egress veth0, layer_cake ingress veth1
apply these rules
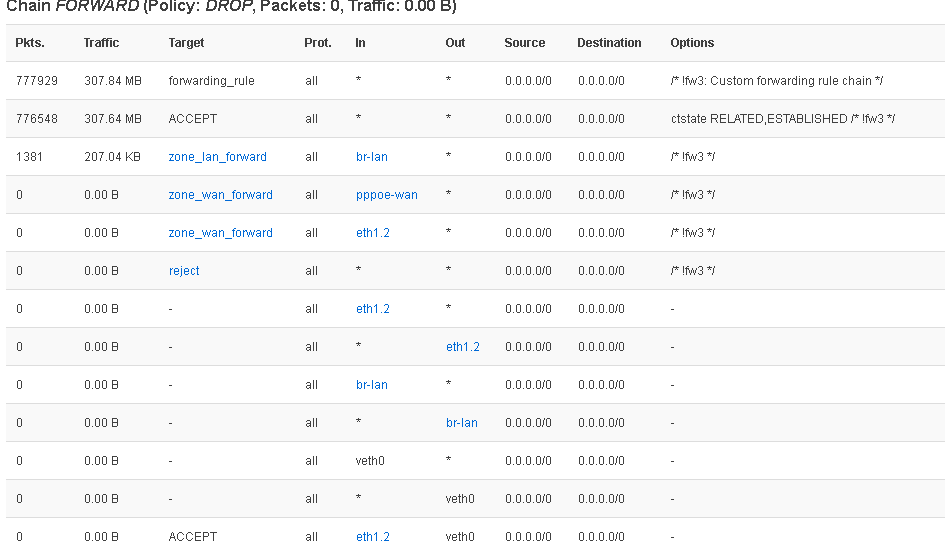
iptables -A FORWARD -i eth1.2 -o veth0 -j ACCEPT
iptables -A FORWARD -s -i eth1.2 -d br-lan -o veth0 -j ACCEPT
my bufferbloat stays above 25 for download
my bufferbloat stays at 15 for upload
Have I done the setup correctly?
those iptables rules bypass your firewall entirely, get rid of them. what you need is changes to the routing table, not iptables
Ok to set up veth pair I do not use any iptables rules.
I will be putting the script to change the openwrt routingtable in network >firewall>custom scripts correct? Forgive me, but I do not know how to construct this script. Would you provide a step by step guide through this process for OpenWrt?
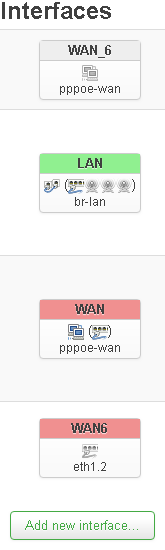
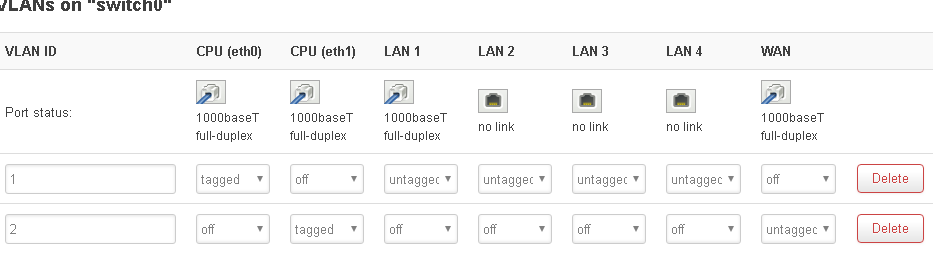
I managed to figure out how to follow these steps in OpenWrt.
I created veth-pair.
I created interface prewan and set protocol: unmanaged, cover the following interface: veth0
I bridged prewan(veth0) and Switch VLAN "eth0.1" (lan)
I set WAN(pppoe-wan) interface physical settings: veth1
With the first set of instructions this is not functional for me. My pppoe will not connect.
With the second set of instructions I am not successful setting this bit properly in OpenWrt Network>Firewall>Firewall - Zone Settings.
I also attempted to edit this script to work with my OpenWrt and I am not able successfully sqm.
the prewan idea requires namespaces and they are not included in openwrt kernels afaik. it works on Debian for example.