Run
ping6 ipv6.google.comRun
ping6 ipv6.google.comuci show firewall
Ran ```
ping6 ipv6.google.com
C:\>ping6 ipv6.google.com
'ping6' is not recognized as an internal or external command,
operable program or batch file.uci show firewall
uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable ' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-so licitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertise ment'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable ' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
Reconnect/reboot your PC, make sure it obtains an IPv6 address from the tunnel broker prefix range.
ping -6 example.org
tracert -6 example.org
Rebooted router and PC, how can tell if I am getting the right ipv6?
also, my wifi access point is not getting a ipv4 address from router, so devices connecting to wifi are not connecting to internet.
Mikrotik hEX Lite OpenWrt 18.06.4 => Tenda AC18 Wifi Access point mode; if the access point does not receive an ipv4 from the router, it automatically enables its own DHCP to clients, but no internet connectivity.
C:\WINDOWS\system32>ping -6 openwrt.org
Pinging openwrt.org [2a03:b0c0:3:d0::1af1:1] with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 2a03:b0c0:3:d0::1af1:1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
C:\WINDOWS\system32>tracert -6 openwrt.org
Tracing route to openwrt.org [2a03:b0c0:3:d0::1af1:1]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms 2600:70ff:e8e3::1
2 170 ms 170 ms 169 ms tunnel541932.tunnel.tserv1.jnb1.ipv6.he.net [2001:470:1f22:1e0::1]
3 169 ms 169 ms 169 ms 10ge11-15.core1.jnb1.he.net [2001:470:0:303::1]
4 351 ms 327 ms 326 ms 10ge2-11.core1.lon2.he.net [2001:470:0:191::1]
5 333 ms 345 ms 343 ms 100ge6-2.core1.ams1.he.net [2001:470:0:2d0::2]
6 * * * Request timed out.
7 * * * Request timed out.
8 * * * Request timed out.
9 * * * Request timed out.
10 * * * Request timed out.
11 * * * Request timed out.
12 * * * Request timed out.
13 * * * Request timed out.
14 * * * Request timed out.
15 * * * Request timed out.
16 * * * Request timed out.
17 * * * Request timed out.
18 * * * Request timed out.
19 * * * Request timed out.
20 * * * Request timed out.
21 * * * Request timed out.
22 * * * Request timed out.
23 * * * Request timed out.
24 * * * Request timed out.
25 * * * Request timed out.
26 * * * Request timed out.
27 * * * Request timed out.
28 * * * Request timed out.
29 * * * Request timed out.
30 * * * Request timed out.
Trace complete.
Haven't been able find a solution yet...
While playing around with settings, the router stopped issuing ipv4 addresses and I could not access some websites until I set a static ipv4 address. Wifi AP stopped working also.
ipv6 internet access was working but still could not ping from LAN.
https://ipv6-test.com/ - Showed that ipv4 connectivity was not supported.
came across this, but not sure if it is safe to use...
https://oldwiki.archive.openwrt.org/ipv6_brouter
https://openwrt.org/docs/guide-user/network/ipv6/ipv6.nat6
You haven't shown us your LAN network config, nor your HE interface configs yet.
The LAN config was default settings, I did not change anything.
Router was setup from factory defaults.
Only thing I configured was PPPoE for WAN and the HE WAN 6 as per the guide https://openwrt.org/docs/guide-user/network/ipv6/ipv6tunnel-luci
I have reset back to defaults, I will try configure again and post setup when I get chance,
Thanks
Then that means you never assigned a routed prefix and IPv6 address to the LAN interface.
I guess, I just followed the guide. I did not see any mention of that. Do you have a link to configure it?
A link of what?
It's simple assignment of an IP, just like the IPv4 address. Perhaps this should be noted on various Wikis across the web (not just here). I have noticed many instructions skip this obvious step (well, for pro network admins - it's obvious, maybe not for laypersons).
You just:
BTW, you need a /48 to do this (it seems you have that already), the default issued subnet is only a single /64 (won't work for a router).
Now, for the LAN IP assignment (DHCPv6/RA) settings:
This should work for all IPv6-capable devices, including Androids (which do not use DHCPv6).
Thank you, I will test this tomorrow and report back. 
I have tried this, but still cannot ping ipv6 from laptop/ PC.
Ping works from router diagnostics.
The routed ipv6 prefix from HE, 2600:70ff:XXXX::/48
So, in the LAN interface I put, (XXXX are the same value as above and below, not sure if correct)
IPv6 address: 2600:70ff:XXXX:XXXX::1/64
IPv6 routed prefix: 2600:70ff:XXXX:XXXX::/64
https://ipv6-test.com/ - shows score of 17/20
LAN IP assignment (DHCPv6/RA) settings: Are all set to Hybrid. With the settings you recommended, WAN & WAN6 does not connect. Also had to check Force DHCP to get IP addresses.
I don't think the lan interface page have any setting called "ipv6 routed prefix" when you enable ipv6 assignment length. Only the wan interface should need the setting IPv6 routed prefix.
It's fine, missing RDNS or ping is not critical unless you plan to host a mail server.
The tracert output indicates that routing is fine as well.
If the tunnel broker filters ICMP for your prefix, try to delete and create a new tunnel with another prefix.
But he is complaining that LAN clients can't ping to the outside, not that he is not able to receive pings. Weird is, that he can access IPv6 websites, but can't ping. Leads me to believe that it has something to do with the firewall settings.
But to clarify some things: the /64 is enough! You can distribute this to your LAN downstream from the router. The tunnel will have it's own prefix. Also, "IPv6 routed prefix" is available and must be set both for WAN6 and for LAN:
WAN6:
Common configuration/General Setup:
-Local IPv6 address: the one from your tunnel which ends with :2/64 (it's listed as "Client IPv6 address" on HE's homepage). Make sure to put the /64 at the end.
-IPv6 routed prefix: the one listed as "Routed /64", e.g. 2001:470:xy:zzzz::/64
LAN:
Common configuration/General Setup:
-IPv6 assignment length: disabled
-IPv6 address: chose address from your /64. E.g. 2001:470:xy:zzzz::1/64
-IPv6 gateway: leave empty
-IPv6 routed prefix: again your routed /64, e.g. 2001:470:xy:zzzz::/64
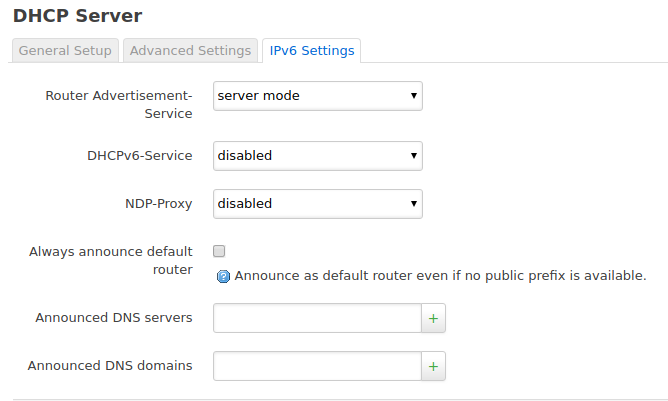
DHCP server/IPv6 settings:
-Router Advertisement-Service: server mode
-DHCPv6-Service: disabled (but all my clients are fine with SLAAC and RDNSS)
-Always announce default router: check
Now, to rule out misconfigured firewall, you could try to delete all routes (DANGEROUS, only for testing!). Or try to create a new rule that is permissive for all ICMP:
Network->Firewall->Traffic Rules:
New forward rule:
Enter name: e.g. ICMP-Test, leave the rest, click "Add and edit..."
-Restrict to address family: IPv4 and IPv6
-Protocol: ICMP
-Match ICMP type: any
-Source zone: Any zone
-Destination zone: Any zone
-Action: accept
Click "Save & Apply"
PS: I find it weird that the tracert seems to work in the beginning. It should also use ICMP. Anyway, I can tracert to openwrt.org.
PPS: Sometimes there really are issues in HE's end. In those cases it's useful to ask on HE's forums. The admins read the requests and have solved many similar problems.
Let us know if you need any clarifications!
Yep, that's why I asked for firewall configuration and here it is:
The tracert output looks like the tunnel broker filters ICMPv6 from that prefix.
Well, since incoming ICMP is explicitly allowed, it's probably logical that outgoing is blocked by default. However, I don't see a rule (or default) that would reject ICMP with src=lan and dest=wan.
However, I would add the following rule:
firewall.@rule[9]=rule
firewall.@rule[9].name='Allow-ICMPv6-Output'
firewall.@rule[9].src='lan'
firewall.@rule[9].dest='*'
firewall.@rule[9].proto='icmp'
firewall.@rule[9].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[9].limit='1000/sec'
firewall.@rule[9].family='ipv6'
firewall.@rule[9].target='ACCEPT'
No, the LAN to WAN forwarding is in place:
And according to the tracert output, ICMPv6 can traverse the tunnel endpoint but can't go outside of the tunnel broker network.