Hi all
The way it is supposed to work is a phone with a specific app is local to a device. The device is put into AP mode via a button - the phone connects to the devices network and then looks for a specific IP address of the device (172.30.1.1). At that point the App becomes functional and configures the device. Great.
I want to be able to do this remotely by NAT and a VPN. Now I don't have any real control over the App or the Device - but I can put it in AP mode remotely. But I'm not sure yet if that is necessary. If I can establish a vpn to the onsite OpenWRT router and give the client an ip in the network of the device's AP range such as 172.30.1.2 it should be good. The tricky part is the following - I want to make it transparent to the App, translate 172.* traffic to the device sitting on the normal LAN of the router.
So essentially All traffic on wg0 meant for 172.30.1.1 gets rewritten or NAT'd to 10.10.x.2 (devices LAN address). I'm trying to spoof that the App is local to the device, saving time and resources from driving all the way out to the site. Does this seem feasible, or is there a better way to accomplish what I'm doing here?
Seems simple enough right? I'll also need to figure out how to trigger the route on VPN connect as well. but that is step 2.
This might be possible, but there are a bunch of unknowns here...
Does the app only attempt to connect if it sees a wifi address on the 172.30.1.0/24 network?
Does the app actually use an IP address to connect, or does it use mdns or similar auto-discovery techniques?
Does the app use a data method that can be routed (similar to the above question, but with some subtle differences).
I'd recommend starting simple -- don't use WG or any VPN for the initial test.
In theory, you could use a wifi radio in client mode to connect to the device in question. That radio would be tied to an interface which would then hold an address in the 172.30.1.0/24 network. From there, you'd assign that network to a firewall zone, and allow forwarding from the other relevant zone(s).
So, if you do the above and have another normal network on the same router with a different address (say 192.168.1.0/24 which is the default OpenWrt LAN), you can enable wifi on that network (in AP mode) and connect your phone to that normal LAN. Launch the app and see if you can communicate with the device. If you can, it means the connection can be routed and therefore it would be possible to use WG to remotely access the device.
funny, that's where I landed too with this. It's more in the spirit of what the device and app expects anyhow.
So I'm a bit stuck - this is 101 stuff. I created LAN2 with a static 172.30.1.254 and connected up to the devices AP. No problem - the device can ping the router's client .254 interface fine. I just can't seem to figure out how to go reverse. Router to Device at 172.30.1.1
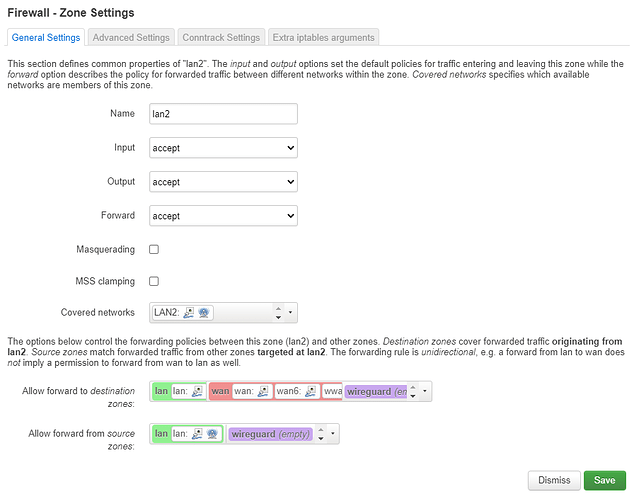
Here's my firewall:
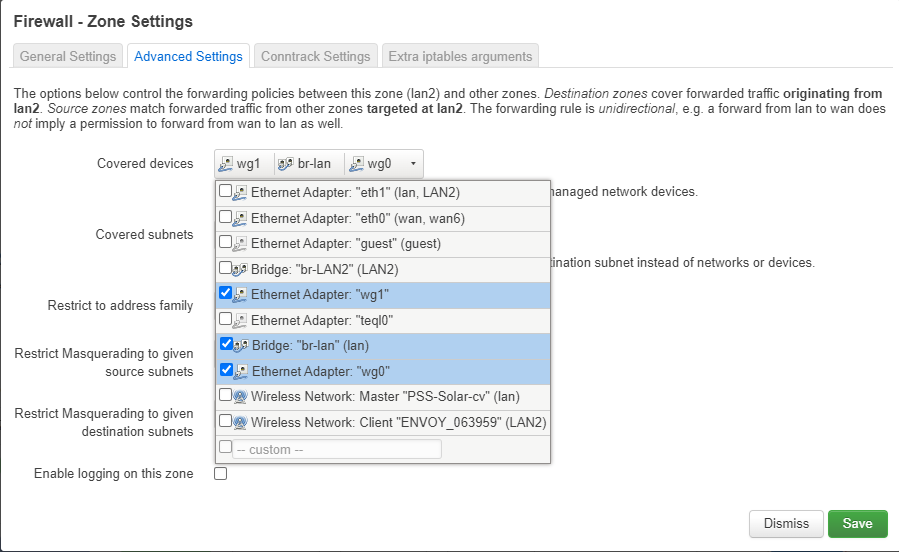
and the Advanced firewall (because I can only post one photo)
Best option is to post you configuration in text form:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd06:7f39:3f69::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option hostname 'GL-AR300M-54b'
option ipaddr '10.10.3.1'
config interface 'wan'
option ifname 'eth0'
option proto 'dhcp'
option hostname 'GL-AR300M-54b'
option ipv6 '0'
option metric '10'
config interface 'wan6'
option ifname 'eth0'
option proto 'dhcpv6'
option disabled '1'
config interface 'guest'
option ifname 'guest'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '172.30.1.254'
config interface 'wwan'
option proto 'dhcp'
option metric '20'
config interface 'LAN2'
option type 'bridge'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '172.30.1.254'
root@PSS-Cory:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option txpower '20'
option txpower_max '20'
option band '2G'
option country 'US'
option htmode 'HT20'
option channel 'auto'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option encryption 'psk2'
option wds '1'
option disassoc_low_ack '0'
option ifname 'wlan0'
option key 'zzzzzzzz'
option ssid 'PSS-Solar-cv'
config wifi-iface 'guest2g'
option device 'radio0'
option guest '1'
option key 'zzzzzzzzzz'
option ifname 'wlan3'
option ssid 'ENVOY_063959'
option encryption 'none'
option bssid '64:33:DB:C7:03:E9'
option network 'LAN2'
option mode 'sta'
option wds '1'
root@PSS-Cory:~# cat /etc/config/dhcp
config dnsmasq
option localise_queries '1'
option rebind_protection '1'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '0'
option local '/lan/'
option domain 'lan'
list interface 'lan'
list interface 'wg1'
list interface 'wwan'
list interface 'wg0'
list interface 'guest'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
option dhcpv6 'disabled'
option ra 'disabled'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option leasetime '12h'
option dhcpv6 'disabled'
option ra 'disabled'
option start '3'
option limit '247'
config domain 'localhost'
option name 'console.gl-inet.com'
option ip '10.10.3.1'
config host '001dc075604b'
option mac '00:1d:c0:75:60:4b'
option ip '10.10.3.2'
option name 'envoy'
config domain
option name 'envoy.local'
option ip '172.30.1.1'
config host '6433dbc703e8'
option mac '64:33:db:c7:03:e8'
option ip '172.30.1.1'
option name 'envoy'
root@PSS-Cory:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'LAN2'
list device 'eth1'
list device 'wg1'
list device 'wg0'
config zone
option name 'lan2'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
list device 'wg1'
list device 'br-lan'
list device 'wg0'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option input 'DROP'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
option reload '1'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config zone 'guestzone'
option name 'guestzone'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
list network 'guest'
config forwarding 'guestzone_fwd'
option src 'guestzone'
option dest 'wan'
config rule 'guestzone_dhcp'
option name 'guestzone_DHCP'
option src 'guestzone'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule 'guestzone_dns'
option name 'guestzone_DNS'
option src 'guestzone'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config rule 'sambasharewan'
option src 'wan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'DROP'
config rule 'sambasharelan'
option src 'lan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'ACCEPT'
config rule 's2s_rule_udp'
option name 'Allow S2S UDP'
option proto 'udp'
option src 'wan'
option target 'ACCEPT'
option dest_port '51840'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config rule 'glservice_rule'
option name 'glservice'
option dest_port '80'
option proto 'tcp udp'
option src 'wan'
option target 'ACCEPT'
option enabled '1'
config rule 'glssh_rule'
option name 'glssh'
option dest_port '22'
option proto 'tcp udp'
option src 'wan'
option target 'ACCEPT'
option enabled '1'
config rule 'AllowWireguard'
option name 'Allow-Wireguard'
option target 'ACCEPT'
option src 'wan'
option proto 'udp tcp'
option family 'ipv4'
option dest_port '51820'
config zone 'wireguard'
option name 'wireguard'
option input 'ACCEPT'
option forward 'DROP'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option masq6 '1'
list device 'eth1'
list device 'br-LAN2'
list device 'br-lan'
config forwarding 'wireguard_wan'
option src 'wireguard'
option dest 'wan'
config forwarding 'wireguard_lan'
option src 'wireguard'
option dest 'lan'
config forwarding 'lan_wireguard'
option src 'lan'
option dest 'wireguard'
config forwarding 'guest_wireguard'
option src 'guestzone'
option dest 'wireguard'
config forwarding 'wireguard_guest'
option src 'wireguard'
option dest 'guestzone'
config forwarding
option dest 'lan'
option src 'lan2'
config forwarding
option dest 'wan'
option src 'lan2'
config forwarding
option dest 'wireguard'
option src 'lan2'
config forwarding
option dest 'lan2'
option src 'wireguard'
config forwarding
option dest 'lan2'
option src 'lan'
There are a bunch of things wrong here... but also a potential sticking point.
It appears you are using the GL-Inet firmware rather than official OpenWrt. This means that any advice I give you might steer you in the wrong direction due to changes that GL-Inet may have made.
So... my recommendation is the following: Install an official version of OpenWrt and start with a default config. It will be much easier than cleaning up the myriad of issues, and it will be more likely to succeed because I don't know what GL-inet has changed and how that might impact your goal.
hmm, that's unfortunate. I'm attempting to deploy a large fleet of these. One at the main office connected to many dozens of clients. I wonder if I would only need my main router to be an official distro
How about this... use any router that can be loaded with OpenWrt (21.02, preferably). It could be the GL-Inet one you're using, or any other you have available or can get quickly/cheaply. The idea is that you want a dev box to use as a proof of concept. Start with a fresh/default install and setup the second network and try routing. If it works, you can layer on the WG interface and try setting up remote access capabilities.
If it doesn't work, you know you've either got more to figure out/fix, or you've hit a dead end (possibly based on how the device and app work).
Anyway, if it works with your dev box, you'll then know it is possible and the general topology/configuration necessary for it to work as desired. At that point, you can try to implement the whole thing on the GL-Inet device with stock firmware.
As of right now, I think that's the best path. There is so much going on (both incorrect/problematic and general complexity) in your existing config and additional uncertainty about the effect of the GL-Inet firmware, making it a major chore to even prove if the concept will work or not.
I hear you - I've got a stack of these things sitting beside my desk. working on it now
1 Like
Here it is - just the basics
root@pss-dev:~# cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdda:68ff:ef69::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.10.100.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'LAN2'
option proto 'static'
option device 'br-lan'
option ipaddr '172.30.1.254'
option netmask '255.255.255.0'
root@pss-dev:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option band '2g'
option htmode 'HT20'
option channel 'auto'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'PSS-Dev'
option encryption 'psk2'
option key 'zzzzzzzz'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'sta'
option ssid 'ENVOY_063959'
option encryption 'none'
option bssid '64:33:DB:C7:03:E9'
option ifname 'envoy_link'
option network 'LAN2'
option wds '1'
root@pss-dev:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@pss-dev:~# cat /etc/config/firewall
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://dev.openwrt.org/ticket/10381
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
# allow interoperability with traceroute classic
# note that traceroute uses a fixed port range, and depends on getting
# back ICMP Unreachables. if we're operating in DROP mode, it won't
# work so we explicitly REJECT packets on these ports.
config rule
option name Support-UDP-Traceroute
option src wan
option dest_port 33434:33689
option proto udp
option family ipv4
option target REJECT
option enabled false
# include a file with users custom iptables rules
config include
option path /etc/firewall.user
### EXAMPLE CONFIG SECTIONS
# do not allow a specific ip to access wan
#config rule
# option src lan
# option src_ip 192.168.45.2
# option dest wan
# option proto tcp
# option target REJECT
# block a specific mac on wan
#config rule
# option dest wan
# option src_mac 00:11:22:33:44:66
# option target REJECT
# block incoming ICMP traffic on a zone
#config rule
# option src lan
# option proto ICMP
# option target DROP
# port redirect port coming in on wan to lan
#config redirect
# option src wan
# option src_dport 80
# option dest lan
# option dest_ip 192.168.16.235
# option dest_port 80
# option proto tcp
# port redirect of remapped ssh port (22001) on wan
#config redirect
# option src wan
# option src_dport 22001
# option dest lan
# option dest_port 22
# option proto tcp
### FULL CONFIG SECTIONS
#config rule
# option src lan
# option src_ip 192.168.45.2
# option src_mac 00:11:22:33:44:55
# option src_port 80
# option dest wan
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
# option target REJECT
#config redirect
# option src lan
# option src_ip 192.168.45.2
# option src_mac 00:11:22:33:44:55
# option src_port 1024
# option src_dport 80
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
This won't work because you're now assigning both lan and LAN2 to br-lan.
Do it this way, instead:
config device
option name 'br-lan2'
option type 'bridge'
list ports 'eth0.3'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '1t 6t'
config interface 'lan2'
option proto 'static'
option device 'br-lan2'
option ipaddr '172.30.1.254'
option netmask '255.255.255.0'
Does your device actually expect a WDS type connection? I would expect WDS should be disabled, but I can't speak to your specific device.
Also, if you follow my exact suggestion above, note that I have made "lan2" all lowercase (which is generally recommended, but not required) -- all references to this network must match case (wireless, firewall, DHCP).
You also need to associate lan2 with a firewall zone and enable forwarding. I'm not sure if you need bidirectional fowarding enabled, but I'll include that for now.
config zone
option name lan2
list network 'lan2'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config forwarding
option src lan
option dest lan2
config forwarding
option src lan2
option dest lan
got it - still no ping though - what did we miss/I screw up?
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdda:68ff:ef69::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config device
option name 'br-lan2'
option type 'bridge'
list ports 'eth0.3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.10.100.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '1t 6t'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'lan2'
option proto 'static'
option device 'br-lan2'
option ipaddr '172.30.1.254'
option netmask '255.255.255.0'
root@pss-dev:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option band '2g'
option htmode 'HT20'
option channel 'auto'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'PSS-Dev'
option encryption 'psk2'
option key 'zzzzzzz'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'sta'
option ssid 'ENVOY_063959'
option encryption 'none'
option bssid '64:33:DB:C7:03:E9'
option ifname 'envoy_link'
option network 'lan2'
option wds '1'
root@pss-dev:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@pss-dev:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'LAN2'
list device 'br-lan'
list device 'envoy_link'
config zone
option name lan2
list network 'lan2'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src lan
option dest lan2
config forwarding
option src lan2
option dest lan
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
and oddly, yes i couldn't get it connected in just Client mode. Needed WDS
this looks a bit messed up in terms of formatting (my fault)
Try this:
config forwarding
option src 'lan2'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'lan2'
also fix the lan2 zone:
config zone
option name 'lan2'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan2'
And in the lan zone, remove these:
still missing something! The device can ping it fine still
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdda:68ff:ef69::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config device
option name 'br-lan2'
option type 'bridge'
list ports 'eth0.3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.10.100.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '1t 6t'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'lan2'
option proto 'static'
option device 'br-lan2'
option ipaddr '172.30.1.254'
option netmask '255.255.255.0'
root@pss-dev:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option band '2g'
option htmode 'HT20'
option channel 'auto'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'PSS-Dev'
option encryption 'psk2'
option key 'zzzzz'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'sta'
option ssid 'ENVOY_063959'
option encryption 'none'
option bssid '64:33:DB:C7:03:E9'
option ifname 'envoy_link'
option network 'lan2'
option wds '1'
root@pss-dev:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@pss-dev:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'LAN2'
list device 'br-lan'
list device 'envoy_link'
config zone
option name 'lan2'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan2'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan2'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'lan2'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
What is pinging what? What works and what fails?
Try pinging the Envoy device from the router itself
if the Envoy device supports it, ping the router from Envoy.
use a computer connected to the lan to ping the Envoy device
ping that same computer from the envoy device (if supported)
Post the results.
Ok - i had left the old router up and connected! the envoy was actually pinging the old one.
Try pinging the Envoy device from the router itself - Doesn't work
if the Envoy device supports it, ping the router from Envoy. Doesn't work but there is a ping interface
use a computer connected to the lan to ping the Envoy device Doesn't work
ping that same computer from the envoy device (if supported) hmm, nope
butter_fry:
Try pinging the Envoy device from the router itself - Doesn't work
If this doesn't work, you need to fix this first.
1 Like