Yes I think this would work too. Anything less basic, perhaps with a GUI ?
Not that I'm shy of using the CLI: a few well give grep/sed/awk will produce quite detailed stats if need be.
Yes, but only for private use (Parental Control) ![]()
Another option is the installation of squid-proxy on the router. Plus one of many free tools to analyze the access_log.
Yes, that would be for parental control purposes indeed, it's my home network and have kids around.
Oh, I didn't know squid could run on this device. Does it ? How about resource consumption ?
Never used it, didn't know it had a GUI (but I strongly suspect it can do much more than requested).
Dunno, which device you have. 128MB is min to run squid as proxy only.
The GUI is only available for the log analyzer.
Sorry, forgot to mention: I got a Linksys WRT3200ACM with the purpose of investigating adoption of OpenWRT, so it's 512MB. Though, I should say, I'm trying to fit Snort in it too (which I see, with the lowmem search algorithm reduced the load quite a lot. Will have check mem during a meaningful time span). The GUI would anyway run (for the squid case) on another linux box, just accessing the router so to keep this doing the minimum job it has to do by itself.
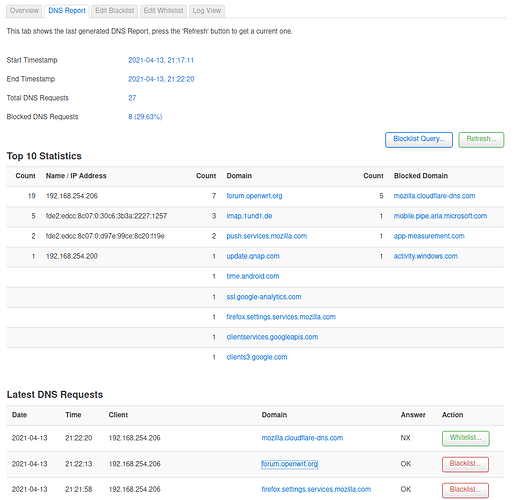
This looks interesting, I will definitely explore it (and it's history time frame settings). Thanks!
Using squid gives you the most precise info. As it counts all real web accesses, whereas DNS queries to be counted is badly influenced by the browsers DNS cache.
Unfortunately, using squid for the intended purpose is much more difficult.
Don't underestimate the efforts and the little rewards attainable. Not only are browsers pushing for DoH (which sidesteps the DNS based observation altogether), but opening a single modern web page easily hits 100-150 different (external-) domains these days (and CDN backed content won't make this easier either) - so expect to be buried in results.
What slh said.
My pihole tells me our home network generates roughly 65k DNS request in 24hrs.
And that's just the primary, there's another 3-5k or so queries to the backup pihole.
Well, this could be seen as a good step ahead in terms of learning and exploration (which accounts for a good amount of the rationale in considering the switch from AsusWRT). Though I understand that the learning curve to get the first meaningful results might quite steep (if only because this is all interspersed within a currently tight work schedule).
That's correct, and it will open a new topic whether between dnsmasq and something like squid, in a coming future, one might be able to cover the requirement anyway within a home network.
And that's correct too, of course. My main purpose is to be able to observe which client tried to access a specific web resource once I see that flagged by some security tool (be it currently Suricata or Skynet in AsusWRT or next Snort with some ip-blocking tool in OpenWRT). Specially useful is to keep an history of such data to understand whether that was a once-in-a-lifetime access or a something going on regularly. Of course keeping an eye to the general browsing patterns would be good as well, if time allowed for it.
That's interesting. You raised the curiosity to check the counters in my home network, which I never did. A quick grep on yesterday's dnsmasq log (a log accounting only for DNS requests) shows that:
# grep query dnsmasq.log1 | wc -l
27569
Oh, here' s different then. How do I install packages from this repo ?
it is already in the main repositories...
Just install frop opkg or from luci.
This is now in place and working fine, thanks !
This is now in place and working fine too, thanks !