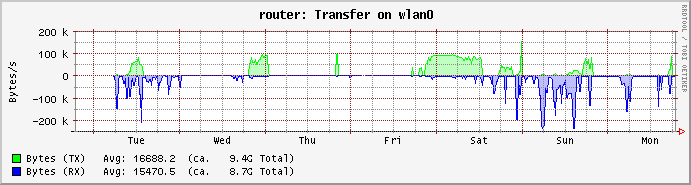
So apparently when this issue happens I am getting spammed by invalid packets from multiple IPs, which showed up when I made conntrack log invalid packets to the log. I did a packet capture with tcpdump and waited for the log to show a message that an invalid packet from said IP was found. I then stopped the capture, and pasted the capture below. I am not entirely sure which of these packets are invalid and why (I am not even sure if they'd even show up in TCPDump?), but maybe this is useful?
root@OpenWrt:~# tcpdump -i any -xx -n -vvv src 197.253.66.127
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
22:25:50.068032 IP (tos 0x48, ttl 117, id 21000, offset 0, flags [DF], proto TCP (6), length 60)
197.253.66.127.2257 > myExternalP.60781: Flags [S.], cksum 0xb5dd (correct), seq 4069701044, ack 2884318623, win 0, options [mss 1460,sackOK,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop], length 0
0x0000: 0000 0200 0000 8038 bc0b cd2e 0000 0800
0x0010: 4548 003c 5208 4000 7506 9c5d c5fd 427f
0x0020: 5658 b839 08d1 ed6d f292 b5b4 abeb 359f
0x0030: a012 0000 b5dd 0000 0204 05b4 0402 0101
0x0040: 0101 0101 0101 0101 0101 0101
22:25:50.068128 IP (tos 0x48, ttl 116, id 21000, offset 0, flags [DF], proto TCP (6), length 60)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0x022e (correct), seq 4069701044, ack 2884318623, win 0, options [mss 1460,sackOK,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 003c 5208 4000 7406 e9ad c5fd 427f
0x0020: c0a8 0199 08d1 ed6d f292 b5b4 abeb 359f
0x0030: a012 0000 022e 0000 0204 05b4 0402 0101
0x0040: 0101 0101 0101 0101 0101 0101
22:25:50.068150 IP (tos 0x48, ttl 116, id 21000, offset 0, flags [DF], proto TCP (6), length 60)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0x022e (correct), seq 4069701044, ack 2884318623, win 0, options [mss 1460,sackOK,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 003c 5208 4000 7406 e9ad c5fd 427f
0x0020: c0a8 0199 08d1 ed6d f292 b5b4 abeb 359f
0x0030: a012 0000 022e 0000 0204 05b4 0402 0101
0x0040: 0101 0101 0101 0101 0101 0101
22:25:50.068159 ethertype IPv4, IP (tos 0x48, ttl 116, id 21000, offset 0, flags [DF], proto TCP (6), length 60)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0x022e (correct), seq 4069701044, ack 2884318623, win 0, options [mss 1460,sackOK,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 8100
0x0010: 000b 0800 4548 003c 5208 4000 7406 e9ad
0x0020: c5fd 427f c0a8 0199 08d1 ed6d f292 b5b4
0x0030: abeb 359f a012 0000 022e 0000 0204 05b4
0x0040: 0402 0101 0101 0101 0101 0101 0101 0101
22:25:50.175442 IP (tos 0x48, ttl 117, id 21001, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > myExternalIP.60781: Flags [S.], cksum 0xa0f7 (correct), seq 1385346484, ack 2884318623, win 0, options [mss 1460], length 0
0x0000: 0000 0200 0000 0000 0000 0000 0000 0800
0x0010: 4548 002c 5209 4000 7506 9c6c c5fd 427f
0x0020: 5658 b839 08d1 ed6d 5292 b5b4 abeb 359f
0x0030: 6012 0000 a0f7 0000 0204 05b4
22:25:50.222372 IP (tos 0x48, ttl 116, id 21001, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0xed47 (correct), seq 1385346484, ack 2884318623, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 002c 5209 4000 7406 e9bc c5fd 427f
0x0020: c0a8 0199 08d1 ed6d 5292 b5b4 abeb 359f
0x0030: 6012 0000 ed47 0000 0204 05b4
22:25:50.222412 IP (tos 0x48, ttl 116, id 21001, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0xed47 (correct), seq 1385346484, ack 2884318623, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 002c 5209 4000 7406 e9bc c5fd 427f
0x0020: c0a8 0199 08d1 ed6d 5292 b5b4 abeb 359f
0x0030: 6012 0000 ed47 0000 0204 05b4
22:25:50.222422 ethertype IPv4, IP (tos 0x48, ttl 116, id 21001, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0xed47 (correct), seq 1385346484, ack 2884318623, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 8100
0x0010: 000b 0800 4548 002c 5209 4000 7406 e9bc
0x0020: c5fd 427f c0a8 0199 08d1 ed6d 5292 b5b4
0x0030: abeb 359f 6012 0000 ed47 0000 0204 05b4
22:26:00.320946 IP (tos 0x48, ttl 117, id 2062, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > myExternalIP.48593: Flags [S.], cksum 0xb8e8 (correct), seq 1625666996, ack 1419875905, win 0, options [mss 1460], length 0
0x0000: 0000 0200 0000 8038 bc0b cd2e 0000 0800
0x0010: 4548 002c 080e 4000 7506 e667 c5fd 427f
0x0020: 5658 b839 08d1 bdd1 60e5 b5b4 54a1 9641
0x0030: 6012 0000 b8e8 0000 0204 05b4
22:26:00.367723 IP (tos 0x48, ttl 116, id 2062, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.48593: Flags [S.], cksum 0x0539 (correct), seq 1625666996, ack 1419875905, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 002c 080e 4000 7406 33b8 c5fd 427f
0x0020: c0a8 0199 08d1 bdd1 60e5 b5b4 54a1 9641
0x0030: 6012 0000 0539 0000 0204 05b4
22:26:00.367772 IP (tos 0x48, ttl 116, id 2062, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.48593: Flags [S.], cksum 0x0539 (correct), seq 1625666996, ack 1419875905, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 002c 080e 4000 7406 33b8 c5fd 427f
0x0020: c0a8 0199 08d1 bdd1 60e5 b5b4 54a1 9641
0x0030: 6012 0000 0539 0000 0204 05b4
22:26:00.367788 ethertype IPv4, IP (tos 0x48, ttl 116, id 2062, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.48593: Flags [S.], cksum 0x0539 (correct), seq 1625666996, ack 1419875905, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 8100
0x0010: 000b 0800 4548 002c 080e 4000 7406 33b8
0x0020: c5fd 427f c0a8 0199 08d1 bdd1 60e5 b5b4
0x0030: 54a1 9641 6012 0000 0539 0000 0204 05b4
22:26:00.582190 IP (tos 0x48, ttl 117, id 21007, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > myExternalIP.60781: Flags [S.], cksum 0xc0f8 (correct), seq 848475572, ack 2884318622, win 0, options [mss 1460], length 0
0x0000: 0000 0200 0000 0000 0000 0000 0000 0800
0x0010: 4548 002c 520f 4000 7506 9c66 c5fd 427f
0x0020: 5658 b839 08d1 ed6d 3292 b5b4 abeb 359e
0x0030: 6012 0000 c0f8 0000 0204 05b4
22:26:00.634011 IP (tos 0x48, ttl 116, id 21007, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0x0d49 (correct), seq 848475572, ack 2884318622, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 002c 520f 4000 7406 e9b6 c5fd 427f
0x0020: c0a8 0199 08d1 ed6d 3292 b5b4 abeb 359e
0x0030: 6012 0000 0d49 0000 0204 05b4
22:26:00.634054 IP (tos 0x48, ttl 116, id 21007, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0x0d49 (correct), seq 848475572, ack 2884318622, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 0800
0x0010: 4548 002c 520f 4000 7406 e9b6 c5fd 427f
0x0020: c0a8 0199 08d1 ed6d 3292 b5b4 abeb 359e
0x0030: 6012 0000 0d49 0000 0204 05b4
22:26:00.634065 ethertype IPv4, IP (tos 0x48, ttl 116, id 21007, offset 0, flags [DF], proto TCP (6), length 44)
197.253.66.127.2257 > 192.168.1.153.60781: Flags [S.], cksum 0x0d49 (correct), seq 848475572, ack 2884318622, win 0, options [mss 1460], length 0
0x0000: 0004 0001 0006 66be b77d 32e4 0000 8100
0x0010: 000b 0800 4548 002c 520f 4000 7406 e9b6
0x0020: c5fd 427f c0a8 0199 08d1 ed6d 3292 b5b4
0x0030: abeb 359e 6012 0000 0d49 0000 0204 05b4
This was in the log showing I was getting invalid packets:
root@OpenWrt:~# logread -f | grep -i 197.253.66.127
Wed Nov 4 22:24:35 2020 kern.notice kernel: [96393.775968] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=2050 DF PROTO=TCP SPT=2257 DPT=48593 SEQ=283489716 ACK=1419875906 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:24:45 2020 kern.notice kernel: [96404.069522] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=2056 DF PROTO=TCP SPT=2257 DPT=48593 SEQ=2699408820 ACK=1419875905 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:24:55 2020 kern.notice kernel: [96414.511083] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=2058 DF PROTO=TCP SPT=2257 DPT=48593 SEQ=3504715188 ACK=1419875905 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:25:17 2020 kern.notice kernel: [96436.310428] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=2060 DF PROTO=TCP SPT=2257 DPT=48593 SEQ=2430973364 ACK=1419875905 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:25:50 2020 kern.notice kernel: [96468.781560] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=21001 DF PROTO=TCP SPT=2257 DPT=60781 SEQ=1385346484 ACK=2884318623 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:26:00 2020 kern.notice kernel: [96478.927027] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=2062 DF PROTO=TCP SPT=2257 DPT=48593 SEQ=1625666996 ACK=1419875905 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:26:00 2020 kern.notice kernel: [96479.193313] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=21007 DF PROTO=TCP SPT=2257 DPT=60781 SEQ=848475572 ACK=2884318622 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:26:11 2020 kern.notice kernel: [96489.597619] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=21009 DF PROTO=TCP SPT=2257 DPT=60781 SEQ=1653781940 ACK=2884318622 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:26:32 2020 kern.notice kernel: [96511.359737] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=21011 DF PROTO=TCP SPT=2257 DPT=60781 SEQ=4069701044 ACK=2884318622 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Wed Nov 4 22:27:15 2020 kern.notice kernel: [96554.033940] nf_ct_tcp: invalid packet ignored in state ESTABLISHED IN= OUT= SRC=197.253.66.127 DST=myExternalIP LEN=44 TOS=0x08 PREC=0x40 TTL=117 ID=21013 DF PROTO=TCP SPT=2257 DPT=60781 SEQ=43169204 ACK=2884318622 WINDOW=0 RES=0x00 ACK SYN URGP=0 OPT (020405B4)
Interestingly, I closed the torrent client and and lo and behold: Connections from said IP were part of connections still lingering around in the conntrack table:
root@OpenWrt:~# cat /proc/net/nf_conntrack | grep -i 197.253.66.127 | wc -l
11
While just 11 connections isn't a whole lot, I was getting invalid packets from a ton of different IPs, so they will add up. Seeing as how the exact same IP was generating invalid packets AND showed up with lingering connections in my conntrack table make me believe that these issues are related. I am not sure where to go from here though.
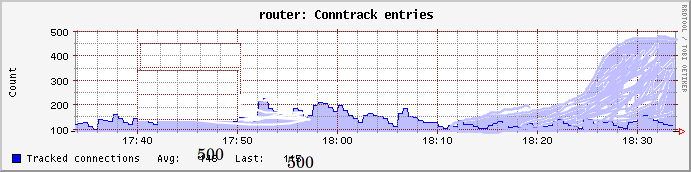

 : all of the timers were under 7440, none above it, and many near it, exactly the value of the setting that Akamai's long-suffering network engineer suggested to look at.
: all of the timers were under 7440, none above it, and many near it, exactly the value of the setting that Akamai's long-suffering network engineer suggested to look at.
 )
)