That was a cool 15 min video! We're still waiting for SurfShark to provide conf file like Mullvad.
Maybe you can use this tool to generate your own config file from your SuftShark private key:
Sad Face... That requires python and a different kernel for my case. Cool development tho. Thanks for the linkage!
You can do it in any computer, no need to run it in your router. You can even clone the repo and run it as a Github action.
In any case, wireguard basically only requires the tunnel and peer info, that basically is a pair of keys and a couple of IP addresses. What kind of info provides SuftShark for wireguard?
I followed this prior to posting in the forums for Torguard.
Did not work for me, also certain config elements TorGuard has that were not done for mulvad.
Great video though, also onemarcfifty has a great channel
TorGuard Config format.
# TorGuard WireGuard Config
[Interface]
PrivateKey = 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
ListenPort = '12345'
MTU = 1292
DNS = x.x.x.x
Address = 'xxxxxxxxxxxxxxxxxx'
[Peer]
PublicKey ='xxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
AllowedIPs = 0.0.0.0/0
Endpoint = 'xxxxxxxxxxxxxxxxxx'
PersistentKeepalive = 25
Thanks, generate config on https://torguard.net/tgconf.php?action=vpn-openvpnconfig , then on openwrt:
1) click System drop-down menu, choose Software and install the package "luci-proto-wireguard"
2) On main menu select Network > Interfaces. Click "Add new interface". Give it a name like TGInterface and select Protocol WireGuard VPN and press submit.
3) Fill in fields using the values seen in the downloaded config.
4) On Advanced Settings tab check the box "Force link".
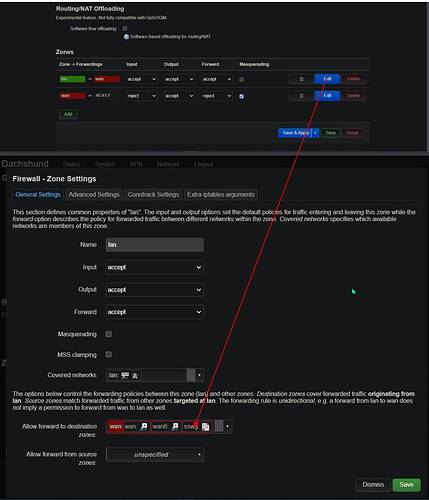
5) Click Network drop-down menu > Firewall. Add a new zone name it TGWireguard and set it to go from and to LAN and apply on TGInterface and set all to Accept and check box for masquerade then save
6) Click Network > DHCP and DNS settings, set DNS forwarding to: 8.8.8.8
apply and reboot router and check if IP changes.
Any comp w/ python.. < yeah or you could just use the confs from your router's shell.sh dwl to use WireGuard desktop app.
EDIT
Nothing yet! Just a wish list
https://surfshark.featureupvote.com/
It is impossible to help you if you do not explain what is the new elements you don't have. Usually you place here the config file after modifying, keys, passwords, IPs, and then we could see how to use that in OpenWrt.
With vague details you will only get vague answers.
With the data you share in your OP I see the problem probably is the lack of metric for each WAN interface. just assign a metric to each wan interface, the lower metric will route all the traffic if the interface is up. That way you don't have to worry about the firewall.
By the way, my VPNs, WAN and WAN6 are all in the same wan zone in the firewall. for a simple routing like that one you are describing, you don't need to create additional zones.
Grab a local installer for your brand of PC and test the conf file from your desktop.
It is a good way to test the data in the config file. But be aware that sometimes the files are not compatible with the app and you have to add the data manually.
Exactly. The only problem is that someone outside your wan could send packets to be routed through your VPN. It is a risk, but very unlikely. To be 100% safe, creating a different zone for each wan adapter would be the safest, but not necessary.
Likely for fail since TorGuard did not supply him with second peer.
Example SurfShark
[Interface]
PrivateKey=KLVVJCdgouxxxxxxxx7XFs0AIlnZ0ZlXMxXwThrcH0=
Address=10.14.0.2/8
MTU=1350
[Peer]
PublicKey=o07k/2dsaQkLLSR0dCI/FUd3FLik/F/HBBcOGUkNQGo=
AllowedIPs=172.16.0.36/32
Endpoint=wgs.prod.surfshark.com:51820
PersistentKeepalive=25
[Peer]
PublicKey=PDALU3lNKMUngtLtfCAcfxrHq3C8AFzI/OVwlQd7WBQ=
AllowedIPs=0.0.0.0/0
Endpoint=us-tpa.prod.surfshark.com:51820
PersistentKeepalive=25
Maybe you can test this solution with Surfshark:
I am going to start from scratch with the steps provided to me from TORGuard support.
In the video that is configured using Mulvad, he doesn't have to configure any VPN routing policies or download the software in his explanation and yet is able to at least show his network tunneled through VPN.
If there is any more information that I can provide un-redacted that is not public IPs on configuration let me know.
Otherwise, going to just hit the VPN Policy document on routing.
I learn by doing ![]()
Uh .. yeah but what is the log look like.. don have to show me.. just see if it's handshaking...
DM'd you, 10-4
10-4... Getting the wireguard tunnel up is first.. then vpn policy routing..
Here comes the Sensei Paul....
All the things we appreciate via single pain of glass in an app yet chose to go down rabbit holes or "tunnels" in this case. ![]()