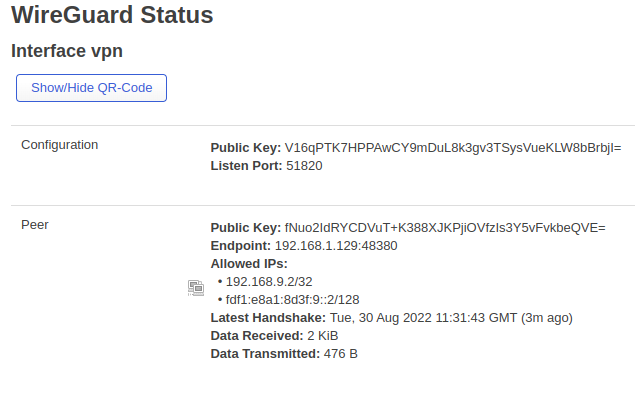
Appreciate the quick response ..
I started from scratch with a new openwrt 21.02.3 image. Checked the time config and made sure it was updating. Loaded wireguard-tools, kmod, luci-app and luci-proto.
I used the following reference for creating the openwrt server config
I rebooted my openwrt host
I'm going to put the complete configs out here as they are meaningless ...
keys
client
private key
+Ed8UYcjWxeEAG0Svb/JdQLaPQFgx5jfrIKFNZYtmlk=
public key
fNuo2IdRYCDVuT+K388XJKPjiOVfzIs3Y5vFvkbeQVE=
server
priavte key
WIJu2sEK5CKZheYbXtYdBlxlLsmHX2+CRNc85WAf+mI=
public key
V16qPTK7HPPAwCY9mDuL8k3gv3TSysVueKLW8bBrbjI=
Ubuntu laptop acting as client
[Interface]
PrivateKey = +Ed8UYcjWxeEAG0Svb/JdQLaPQFgx5jfrIKFNZYtmlk=
Address = 192.168.9.2/32
#DNS = 1.1.1.1
[Peer]
PublicKey = V16qPTK7HPPAwCY9mDuL8k3gv3TSysVueKLW8bBrbjI=
Endpoint = 192.168.1.1:51820
AllowedIPs = 0.0.0.0/0, ::/0
type or paste code here
openwrt
network config
NETWORK
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdea:14f3:e265::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config interface 'vpn'
option proto 'wireguard'
option private_key 'WIJu2sEK5CKZheYbXtYdBlxlLsmHX2+CRNc85WAf+mI='
option listen_port '51820'
list addresses '192.168.9.1/24'
list addresses 'fdf1:e8a1:8d3f:9::1/64'
config wireguard_vpn 'wgclient'
option public_key 'fNuo2IdRYCDVuT+K388XJKPjiOVfzIs3Y5vFvkbeQVE='
list allowed_ips '192.168.9.2/32'
list allowed_ips 'fdf1:e8a1:8d3f:9::2/128'
FIREWALL
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone 'lan'
option name 'lan'
list network 'lan'
list network 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone 'wan'
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'