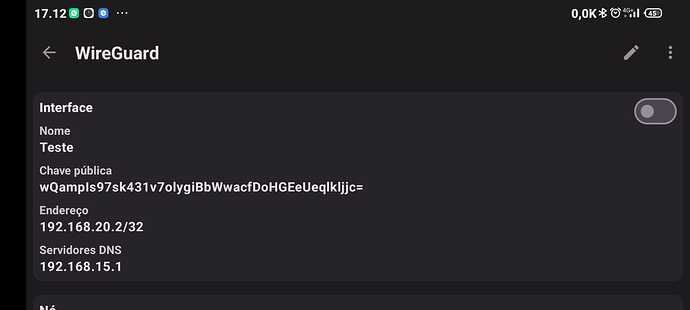
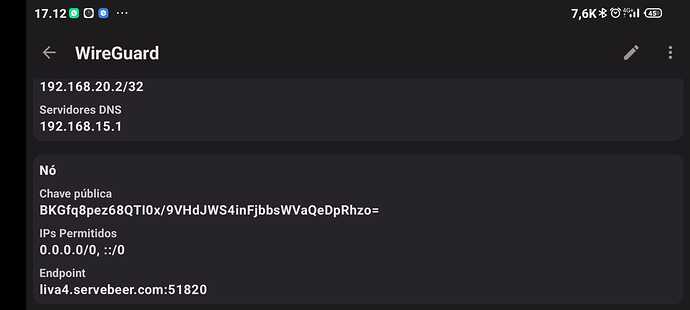
Hello all...
Exercising and improving my knowledge, I set out to learn how to configure wireguard on my router...
Initially, I based myself on the Openwrt Wiki, official tutorial and installed the packages, but I can't connect my clients to the router...
I have a problem that I don't know/can't solve in any way, although I'm searching on the internet...
Come on, the clients send packets, I see that the router receives them, but they cannot connect.
Here are my settings:
/etc/config/network
root@horus:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda2:fbc6:8a20::/48'
config interface 'lan'
option device 'eth1'
option proto 'static'
list ipaddr '192.168.15.1/26'
option ip6assign '64'
config interface 'wan'
option proto 'pppoe'
option device 'eth0'
option username 'cliente@cliente'
option password 'cliente'
option ipv6 'auto'
option metric '1024'
config interface 'onu_vsol'
option proto 'static'
option device 'eth0'
list ipaddr '192.168.1.2/30'
config interface 'wireguard_vpn'
option proto 'wireguard'
option private_key 'REMOVED'
list addresses '192.168.20.1/24'
option listen_port '51820'
config wireguard_wireguard_vpn
option description 'CEL_POCOX3PRO_RR'
option public_key 'f7q2yL2Xv6EEh5PLYCRoQ+U2krjrc/aSxDpOOpuXl2A='
option private_key 'REMOVED'
list allowed_ips '192.168.20.2/32'
option route_allowed_ips '1'
root@horus:~#
etc/config/firewall:
root@horus:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda2:fbc6:8a20::/48'
config interface 'lan'
option device 'eth1'
option proto 'static'
list ipaddr '192.168.15.1/26'
root@horus:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'tun+'
list network 'lan'
list network 'wireguard_vpn'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'onu_vsol'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'NintendoSwitch-NAT_A'
list proto 'udp'
option src 'wan'
option src_dport '45000-65535'
option dest_ip '192.168.15.30'
option dest_port '45000-65535'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DDNS-8181'
option src 'wan'
option src_dport '80'
option dest_ip '192.168.15.1'
option dest_port '8181'
list proto 'tcp'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option src 'wan'
option dest_port '1194'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'WireGuard_VPN'
list proto 'udp'
option src 'wan'
option src_dport '51820'
option dest_ip '192.168.20.1'
option dest_port '51820'
root@horus:~#
I have openvpn running on this router perfectly!
Using the comand "tcpdump -evni any udp port 51820", I have...
root@horus:~# tcpdump -evni any udp port 51820
tcpdump: data link type LINUX_SLL2
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
13:31:06.852410 pppoe-wan In ifindex 5 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 57, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 177.102.51.128.51820: UDP, length 148
13:31:06.852619 eth1 Out ifindex 3 b8:ae:ed:86:c5:06 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 56, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 192.168.15.30.51820: UDP, length 148
13:31:11.963208 pppoe-wan In ifindex 5 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 57, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 177.102.51.128.51820: UDP, length 148
13:31:11.963376 eth1 Out ifindex 3 b8:ae:ed:86:c5:06 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 56, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 192.168.15.30.51820: UDP, length 148
13:31:16.988861 pppoe-wan In ifindex 5 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 57, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 177.102.51.128.51820: UDP, length 148
13:31:16.988989 eth1 Out ifindex 3 b8:ae:ed:86:c5:06 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 56, id 0, offset 0,
ags [none], proto UDP (17), length 176)
13:31:22.043045 pppoe-wan In ifindex 5 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 57, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 177.102.51.128.51820: UDP, length 148
13:31:22.043177 eth1 Out ifindex 3 b8:ae:ed:86:c5:06 ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 56, id 0, offset 0, flags [none], proto UDP (17), length 176)
189.98.248.59.63689 > 192.168.15.30.51820: UDP, length 148
13:31:27.123093 pppoe-wan In ifindex 5 ethertype IPv4 (0x0800), l
Where is my problem?
I've already tried reconfiguring, but it didn't have the desired effect.
Thanks one more time, friends!