@cwbsw
Hello again!
Sorry for necropostiong.
I've read a lot of articles and figured out how routing works! I've even managed to setup eltex commutator.
Thank you for all the articles and help.
I just have one last question.
Everything we've discussed above works, I've automated everything with scripts, its working fine.
Except i accidentaly broke site-to-site tunnel, and i can't understand where.
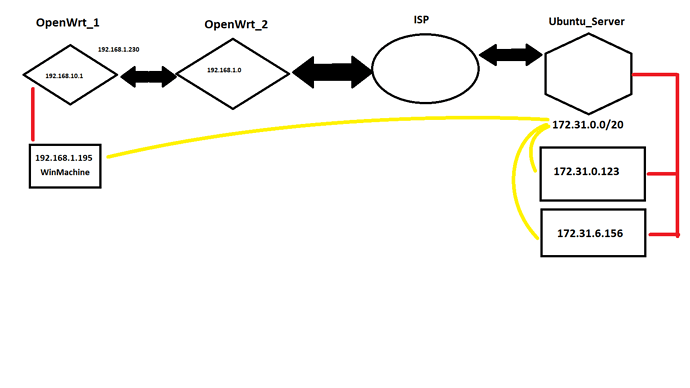
I have two vti tunnels with 10.10.10.N (for accessing restricted sites. Will call it 'VPN') and 10.11.10.N (For site-to-site tunnel to another server. Will call it 'WinTunnel'), where N - is specific to OpenWrt device on different locations. N = 1 for my dev environment at office.
VPN is connected to AWS loadbalancer with fleet of servers behind.
WinTunnel is connected to specific server, which acts as Firewall\AccessPoint to my dev WinServer with ActiveDirectory(hence, WinTunnel).
Schema is as follows:
OpenWrt_1 has subnet 192.168.10.0/24
OpenWrt_2 has subnet 192.168.1.0/24
I have route on OpenWrt_2 to 192.168.10.0/24 subnet and can reach every machine behind OpenWrt_1 from it.
My VPN-Services are installed on OpenWrt_1.
Both tunnels are up and established, no error logs on router\servers.
I can ping my WinServer from OpenWrt_1, but cant reach it from my PC.( 192.168.10.1 node unavailable )
I don't have to setup specific routes on my PC, beacuse route to 172.31.0.0/20 is set on OpenWrt_1, which is my default gateway anyways.
OpenWrt_1
ipsec.conf
config setup
strictcrlpolicy=no
uniqueids=never
cachecrls=no
conn swanvpn
type=tunnel
auto=start
keyexchange=ikev2
authby=secret
leftsubnet=10.10.10.1/32
leftid=OfficeVPN
left=192.168.1.230
right=****
rightid=vpn.***.com
rightsubnet=0.0.0.0/0
ike=aes256-sha1-modp1024!
esp=aes256-sha1!
aggressive=no
keyingtries=%forever
ikelifetime=28800s
lifetime=86400s
dpddelay=10s
dpdtimeout=30s
dpdaction=restart
mark_in=32
mark_out=42
forceencaps=yes
mobike=yes
conn wintunnel
type=tunnel
auto=start
keyexchange=ikev2
authby=secret
leftsubnet=10.11.10.1/32
left=192.168.1.230
leftid=OfficeVPN
right=****
rightsubnet=172.31.0.0/20
ike=aes256-sha1-modp1024!
esp=aes256-sha1!
aggressive=no
keyingtries=%forever
ikelifetime=28800s
lifetime=86400s
dpddelay=10s
dpdtimeout=30s
dpdaction=restart
mark_in=33
mark_out=43
forceencaps=yes
mobike=yes
ip r show
default via 192.168.1.1 dev eth0.2 proto static src 192.168.1.230
172.31.0.0/20 dev vti2 scope link
192.168.1.0/24 dev eth0.2 proto kernel scope link src 192.168.1.230
192.168.10.0/24 dev br-lan proto kernel scope link src 192.168.10.1
ipsec statusall
Status of IKE charon daemon (strongSwan 5.9.2, Linux 5.4.188, mips):
uptime: 4 minutes, since Aug 16 09:27:31 2022
worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 10
loaded plugins: charon aes sha1 random nonce x509 pubkey gmp xcbc hmac kernel-netlink socket-default stroke updown
Listening IP addresses:
10.11.10.1
192.168.10.1
fd12:b857:5201:4::1
fd24:28f8:e06c::1
192.168.1.230
fd12:b857:5201:0:da07:b6ff:fed3:9e50
fd12:b857:5201::230
Connections:
swanvpn: 192.168.1.230...16.170.**.** IKEv2, dpddelay=10s
swanvpn: local: [OfficeVPN] uses pre-shared key authentication
swanvpn: remote: [vpn.cloudcrmweb.com] uses pre-shared key authentication
swanvpn: child: 10.10.10.1/32 === 0.0.0.0/0 TUNNEL, dpdaction=restart
wintunnel: 192.168.1.230...3.8.**.** IKEv2, dpddelay=10s
wintunnel: local: [OfficeVPN] uses pre-shared key authentication
wintunnel: remote: [3.8.**.**] uses pre-shared key authentication
wintunnel: child: 10.11.10.1/32 === 172.31.0.0/20 TUNNEL, dpdaction=restart
Security Associations (2 up, 0 connecting):
wintunnel[2]: ESTABLISHED 4 minutes ago, 192.168.1.230[OfficeVPN]...3.8.**.**[3.8.**.**]
wintunnel[2]: IKEv2 SPIs: 7b2a9c03564034da_i* 180f927c6d1dd22e_r, pre-shared key reauthentication in 7 hours
wintunnel[2]: IKE proposal: AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
wintunnel{2}: INSTALLED, TUNNEL, reqid 2, ESP in UDP SPIs: c012c6a3_i c825b56e_o
wintunnel{2}: AES_CBC_256/HMAC_SHA1_96, 168 bytes_i (2 pkts, 228s ago), 320 bytes_o (6 pkts, 109s ago), rekeying in 23 hours
wintunnel{2}: 10.11.10.1/32 === 172.31.0.0/20
swanvpn[1]: ESTABLISHED 4 minutes ago, 192.168.1.230[OfficeVPN]...16.170.**.**[vpn.***.com]
swanvpn[1]: IKEv2 SPIs: 82e34ce0545eed81_i* b733c622c29ebe8a_r, pre-shared key reauthentication in 7 hours
swanvpn[1]: IKE proposal: AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
swanvpn{1}: INSTALLED, TUNNEL, reqid 1, ESP in UDP SPIs: c793299e_i c47eb650_o
swanvpn{1}: AES_CBC_256/HMAC_SHA1_96, 61667 bytes_i (398 pkts, 96s ago), 45705 bytes_o (480 pkts, 96s ago), rekeying in 23 hours
swanvpn{1}: 10.10.10.1/32 === 0.0.0.0/0
uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].forward='ACCEPT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[1].input='ACCEPT'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Support-UDP-Traceroute'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='33434:33689'
firewall.@rule[9].proto='udp'
firewall.@rule[9].family='ipv4'
firewall.@rule[9].target='REJECT'
firewall.@rule[9].enabled='false'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].name='VPN_ZONE'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].network='VPN'
firewall.@zone[2].masq='1'
firewall.@zone[3]=zone
firewall.@zone[3].name='VPNTUNNEL_ZONE'
firewall.@zone[3].forward='ACCEPT'
firewall.@zone[3].input='ACCEPT'
firewall.@zone[3].output='ACCEPT'
firewall.@zone[3].network='WINTUNNEL'
firewall.@zone[3].masq='1'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='lan'
firewall.@forwarding[1].dest='VPN_ZONE'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].src='VPN_ZONE'
firewall.@forwarding[2].dest='lan'
firewall.@forwarding[3]=forwarding
firewall.@forwarding[3].src='lan'
firewall.@forwarding[3].dest='VPNTUNNEL_ZONE'
firewall.@forwarding[4]=forwarding
firewall.@forwarding[4].src='VPNTUNNEL_ZONE'
firewall.@forwarding[4].dest='lan'
firewall.@forwarding[5]=forwarding
firewall.@forwarding[5].src='wan'
firewall.@forwarding[5].dest='lan'
Ubuntu_Server ipsec.conf
config setup
charondebug="ike 1, knl 1, cfg 0"
uniqueids=no
conn win-psk-base
type=tunnel
auto=add
keyexchange=ikev2
authby=secret
left=%any
leftsubnet=172.31.0.0/20
right=%any
rightdns=8.8.8.8,8.8.4.4
ike=aes256-sha1-modp1024!
esp=aes256-sha1!
aggressive=no
keyingtries=%forever
ikelifetime=28800s
lifetime=3600s
dpddelay=30s
dpdtimeout=120s
dpdaction=restart
leftupdown=/etc/ipsec.d/firewall.updown
conn WIN-Office
also=win-psk-base
rightsubnet=10.11.10.1/32
rightid=OfficeVPN
conn WIN-Zinina
also=win-psk-base
rightsubnet=10.11.10.2/32
rightid=ZininaVPN
I know for sure, that i've had both tunnels working at the same time.
I think i've messed things up when i was "standartizing" configs and installation with bash scripts.
I've tried to make route to 172.31.0.0/20 from OpenWrt_2 for testing with
ip r add 172.31.0.0/20 via 192.168.1.230
No success.
I am a little bit stumped.