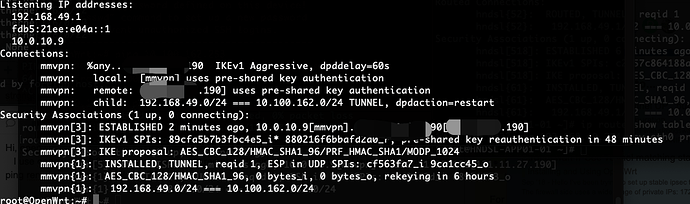
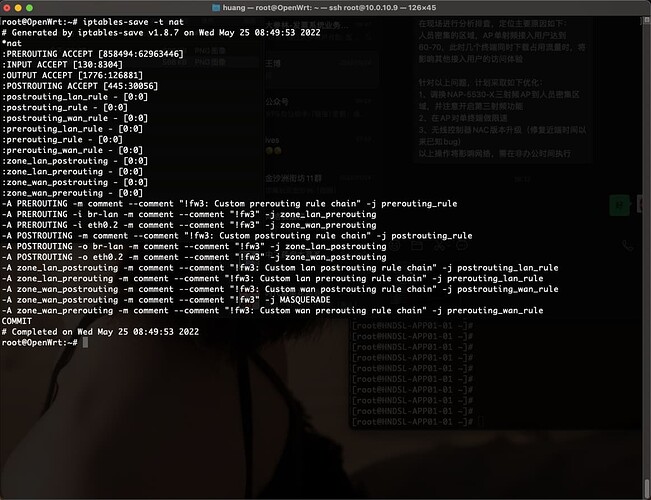
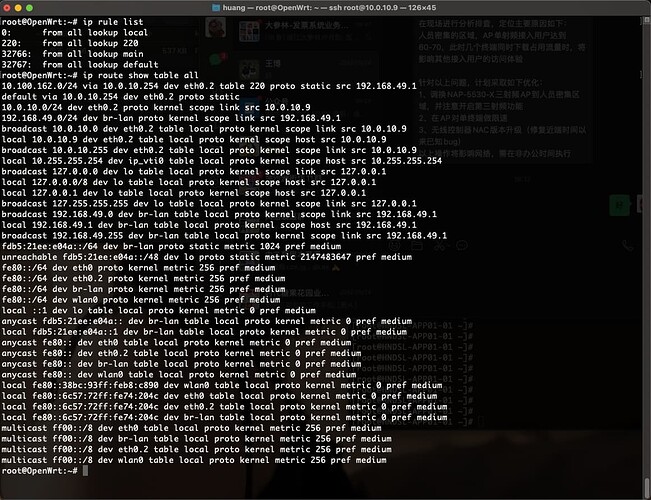
Hi, openwrt
I use openwrt 21.0.3 strongswan connect to remote with side to side, the tunnel is up ,but local can't ping remote,can anyone help me? Thanks.
Need the output of these commands. It's probably that your iptables nat changes the ips of packet and causes the packets to be missed from the xfrm policies.
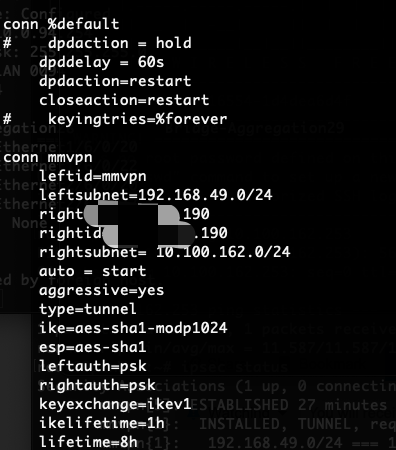
ipsec statusall
ip rule
ip -4 ro sh table all
ip xfrm policy
iptables-save -t nat
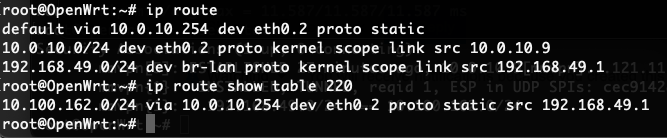
root@OpenWrt:~# ip route show table 220
10.100.162.0/24 via 10.0.10.254 dev eth0.2 proto static src 192.168.49.1
seems normal?
Pick one of these and your problem should be resolved.
Do the same on remote end if it's behind NAT just reverse the src/dst.
To understand why this is needed look at the packet flow
iptables -t nat -I POSTROUTING -s 192.168.49/24 -d 10.100.162/24 -j ACCEPT
iptables -t nat -I postrouting_rule -s 192.168.49/24 -d 10.100.162/24 -j ACCEPT
iptables -t nat -I postrouting_wan_rule -s 192.168.49/24 -d 10.100.162/24 -j ACCEPT
It's works,Thanks for you help.
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
@ppmm
Can you help me too? I have a roadwarrior setup where i connect to openwrt but can't ping my hosts and vice versa.
root@router:~# swanctl -l
ikev2-eap-mschapv2: #2, ESTABLISHED, IKEv2, 241d38a86ef900e3_i bfd4c34625cf6656_r*
local 'xxxx.xx' @ 77.6.92.193[4500]
remote 'x1cg6' @ 109.42.113.155[19575] [192.168.1.213]
AES_CBC-256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_3072
established 2340s ago, rekeying in 11776s
ikev2-eap-mschapv2: #1, reqid 1, INSTALLED, TUNNEL-in-UDP, ESP:AES_CBC-256/HMAC_SHA2_384_192
installed 2340s ago, rekeying in 1052s, expires in 1620s
in c62fb0f8, 408972 bytes, 5864 packets, 0s ago
out ce78c252, 392322 bytes, 5637 packets, 0s ago
local 192.168.1.0/24
remote 192.168.1.213/32
root@router:~# ip r
default via 62.52.200.148 dev pppoe-wan proto static
62.52.200.148 dev pppoe-wan proto kernel scope link src 77.6.92.193
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
root@router:~# ip -4 ro sh table all
192.168.1.213 via 62.52.200.148 dev pppoe-wan table 220 proto static src 192.168.1.1
default via 62.52.200.148 dev pppoe-wan proto static
62.52.200.148 dev pppoe-wan proto kernel scope link src 77.6.92.193
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
local 77.6.92.193 dev pppoe-wan table local proto kernel scope host src 77.6.92.193
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
root@router:~# ip xfrm policy
src 192.168.1.0/24 dst 192.168.1.213/32
dir out priority 371327
mark 0x10/0xffffffff
tmpl src 77.6.92.193 dst 109.42.113.155
proto esp spi 0xc4288991 reqid 1 mode tunnel
src 192.168.1.213/32 dst 192.168.1.0/24
dir fwd priority 371327
mark 0x10/0xffffffff
tmpl src 109.42.113.155 dst 77.6.92.193
proto esp reqid 1 mode tunnel
src 192.168.1.213/32 dst 192.168.1.0/24
dir in priority 371327
mark 0x10/0xffffffff
tmpl src 109.42.113.155 dst 77.6.92.193
proto esp reqid 1 mode tunnel
src 0.0.0.0/0 dst 0.0.0.0/0
socket in priority 0
src 0.0.0.0/0 dst 0.0.0.0/0
socket out priority 0
src 0.0.0.0/0 dst 0.0.0.0/0
socket in priority 0
src 0.0.0.0/0 dst 0.0.0.0/0
socket out priority 0
src ::/0 dst ::/0
socket in priority 0
src ::/0 dst ::/0
socket out priority 0
src ::/0 dst ::/0
socket in priority 0
src ::/0 dst ::/0
socket out priority 0
root@router:~# iptables-save -t nat
# Generated by iptables-save v1.8.8 (nf_tables) on Sat Oct 14 13:20:03 2023
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A PREROUTING -p tcp -m tcp --dport 8022 -j REDIRECT --to-ports 22
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 22 -j DNAT --to-destination 192.168.1.4:10002
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 21 -j DNAT --to-destination 192.168.1.104:21
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 20000:20010 -j DNAT --to-destination 192.168.1.104:20000-20010
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 25 -j DNAT --to-destination 192.168.1.100:25
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 587 -j DNAT --to-destination 192.168.1.100:587
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 465 -j DNAT --to-destination 192.168.1.100:465
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 143 -j DNAT --to-destination 192.168.1.100:143
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 993 -j DNAT --to-destination 192.168.1.100:993
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.1.100:80
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 443 -j DNAT --to-destination 192.168.1.100:443
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 5665 -j DNAT --to-destination 192.168.1.100:5665
-A PREROUTING -d 77.6.92.193/32 -p tcp -m tcp --dport 3389 -j DNAT --to-destination 192.168.1.106:3389
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.213/32 -m policy --dir out --pol ipsec --reqid 1 --proto esp -j ACCEPT
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 10002 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 21 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 20000:20010 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 25 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 587 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 465 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 143 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 993 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 80 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 443 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 5665 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.0/24 -p tcp -m tcp --dport 3389 -j SNAT --to-source 192.168.1.1
-A POSTROUTING -o pppoe-wan -j MASQUERADE
COMMIT
# Completed on Sat Oct 14 13:20:03 2023
# Warning: iptables-legacy tables present, use iptables-legacy-save to see them
It worked once but i don't know what happened since then.
OpenWRT's fw3 firewall is completly disabled
Is 192.168.1.0/24 configured on both sides? Try different subnets.