To be clear, I do NOT maintain the OpenWrt code/images. I've just used ImageBuilder to "bundle" it from the official image and opkg sources.
df -h shows
Filesystem Size Used Available Use% Mounted on
/dev/root 8.3M 8.3M 0 100% /rom
tmpfs 60.3M 108.0K 60.2M 0% /tmp
/dev/mtdblock9 4.8M 340.0K 4.4M 7% /overlay
overlayfs:/overlay 4.8M 340.0K 4.4M 7% /
tmpfs 512.0K 0 512.0K 0% /dev
I use batman-adv to have on mesh SSID (802.11s) running that carries the traffic of multiple VLAN networks through the batman interface. For example, you can build a mesh network with "only driven by wireless uplink" access points. One VLAN is the management VLAN where I can access the AP's web UI LUCI, one VLAN is a corporate network and one VLAN is a guest network. Without batman-adv, you would have needed to configure multiple WDS SSID for every single VLAN to provide it to a non-wired access point "on the outside".
My configs are:
/etc/rc.local - Avoids uncaught crashing of the ath10k wifi driver.
# Put your custom commands here that should be executed once
# the system init finished. By default this file does nothing.
/bin/bash /root/wrtwatchdog start
exit 0
/etc/sysctl.conf - Turns off IPv6 (better network performance, proof still under investigation why that is better)
# Defaults are configured in /etc/sysctl.d/* and can be customized in this file
net.ipv6.conf.all.disable_ipv6=1
net.ipv6.conf.default.disable_ipv6=1
net.ipv6.conf.lo.disable_ipv6=1
/etc/sysupgrade.conf - Preserve /root on upgrade
## This file contains files and directories that should
## be preserved during an upgrade.
# /etc/example.conf
# /etc/openvpn/
/root
/etc/config/dhcp - turn off DNS server on external interfaces, preserve on lo (for the opkg update) - Note the "list interface 'lo'"
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option domain 'mycorp.local'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
list interface 'lo'
config dhcp 'lan'
option interface 'lan'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
/etc/config/network - Provide the BATMAN hardIF - VL10 (management VLAN) - VL50 (client VLAN)
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'TO_FILL'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '10'
option ports '0t 1t'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '50'
option ports '0t 1t'
config interface 'VL10'
option proto 'static'
option delegate '0'
option ipaddr 'TO_FILL'
option netmask 'TO_FILL'
option gateway 'TO_FILL'
option broadcast 'TO_FILL'
option igmp_snooping '1'
option igmp_v3 '1'
option multicast_querier '0'
option ifname 'bat0.10 eth0.10'
list dns 'TO_FILL'
list dns 'TO_FILL'
option type 'bridge'
config interface 'VL50'
option type 'bridge'
option proto 'static'
option delegate '0'
option igmp_snooping '1'
option igmp_v3 '1'
option multicast_querier '0'
option ifname 'bat0.50 eth0.50'
config interface 'bat0'
option proto 'batadv'
option routing_algo 'BATMAN_IV'
option aggregation '1'
option ap_isolation '0'
option bonding '0'
option fragmentation '1'
option gw_mode 'off'
option log_level '0'
option orig_interval '10000'
option bridge_loop_avoidance '1'
option distributed_arp_table '1'
option multicast_mode '1'
option network_coding '0'
option hop_penalty '30'
option isolation_mark '0x00000000/0x00000000'
config interface 'nwi_mesh0'
option mtu '1532'
option proto 'batadv_hardif'
option master 'bat0'
/etc/config/wireless - Provide the 802.11s mesh interface and attach it to "nwi_mesh0" (batman hardIF) - Provide SSID (VLAN 50) where your client machines connect to. The VLAN 50 is driven through the batman-adv wireless mesh tunnel.
config wifi-device 'radio0'
option type 'mac80211'
option beacon_int '100'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
option txpower '23'
option country 'DE'
option legacy_rates '0'
option noscan '0'
option disabled '0'
config wifi-device 'radio1'
option type 'mac80211'
option channel '1'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT40'
option txpower '20'
option country 'DE'
option legacy_rates '0'
option noscan '0'
option disabled '0'
config wifi-iface 'wifinet0'
option device 'radio0'
option disabled '0'
option mode 'mesh'
option mesh_id 'CORPMESH'
option encryption 'sae'
option dtim_period '1'
option disassoc_low_ack '0'
option key 'TO_FILL'
option network 'nwi_mesh0'
option mesh_fwding '0'
option mesh_rssi_threshold '0'
config wifi-iface 'wifinet1'
option device 'radio0'
option disabled '0'
option mode 'ap'
option ssid 'CLIENT_WIFI_TO_FILL'
option network 'VL50'
option dtim_period '1'
option disassoc_low_ack '0'
option encryption 'wpa2+ccmp'
option auth_server 'TO_FILL_FOR_EAP'
option auth_port '1812'
option acct_server '1TO_FILL_FOR_EAP'
option acct_port '1813'
option nasid 'TO_FILL_FOR_EAP'
option ieee80211w '1'
option wpa_disable_eapol_key_retries '1'
option auth_secret 'TO_FILL_FOR_EAP'
option acct_secret 'TO_FILL_FOR_EAP'
/etc/config/firewall
config defaults
option syn_flood '1'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
config include
option path '/etc/firewall.user'
config zone
option forward 'REJECT'
option output 'ACCEPT'
option network 'VL10'
option input 'ACCEPT'
option name 'VL10'
config zone
option name 'VL50'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
option network 'VL50'
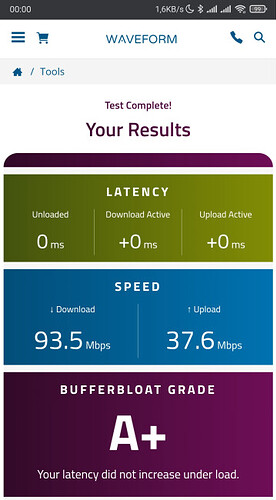

 very nice to see!
very nice to see!