yes I try set dropbear port on 200 and don't work
You still have not posted the configuration from the VPS.
yes, see up on 3d
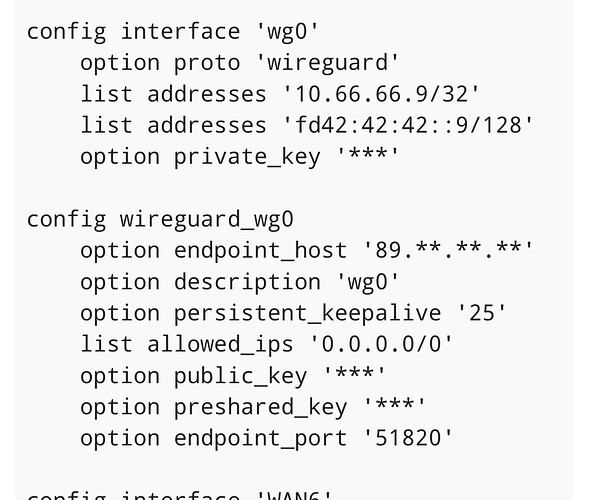
If you are referring to this one, this is the OpenWrt client configuration. There is no configuration from the VPS.
This configuration is from OpenWrt, not from the VPS.
Sorry I don't understand you request
The configuration of the vps
cat /etc/wireguard/params
SERVER_PUB_IP=89.*****
SERVER_PUB_NIC=eth0
SERVER_WG_NIC=wg0
SERVER_WG_IPV4=10.66.66.1
SERVER_WG_IPV6=fd42:42:42::1
SERVER_PORT=51820
SERVER_PRIV_KEY=****
SERVER_PUB_KEY=****
CLIENT_DNS_1=8.8.8.8
CLIENT_DNS_2=8.8.4.4
cat /etc/wireguard/wg0.conf
[Interface]
Address = 10.66.66.1/24,fd42:42:42::1/64
ListenPort = 51820
PrivateKey = ****
iptables -S
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
-A INPUT -i wg0 -j ACCEPT
-A INPUT -i eth0 -p udp -m udp --dport 51194 -j ACCEPT
-A FORWARD -i eth0 -o wg0 -j ACCEPT
-A FORWARD -i wg0 -o eth0 -j ACCEPT
iptables -S -t nat
-P PREROUTING ACCEPT
-P INPUT ACCEPT
-P POSTROUTING ACCEPT
-P OUTPUT ACCEPT
-A POSTROUTING -s 10.66.66.0/24 -o eth0 -j MASQUERADE
The peer configuration is missing. You have posted only the interface configuration for wireguard on VPS, but there must be some configuration for the OpenWrt peer.
The client's end of the tunnel is 10.66.66.9/32 this means the client won't route to the server at .1 They need to both be netmasked within the same subnet.
this is a peer on server side
[Peer]
PublicKey = ****
PresharedKey = ****
AllowedIPs = 10.66.66.9/32,fd42:42:42::9/128
I connect from another peer to openwrt router! is same subnet 10.66.66.0
One thing is to fix the subnet mask on OpenWrt as @mk24 suggested, 10.66.66.9/24 and fd42:42:42::9/64. Also this needs to be fix to all other wg clients you have
The other thing is that on server side you allow only the wg tunnel IP, so while ssh to 10.66.66.9 will work, 192.168.2.1 will not work. You'll need to add 192.168.2.0/24 to allowed networks and add static route, if you don't do it automatically from wireguard.