You configure port forwarding when you have NAT, you configure traffic rule when you don't. In either case you need port and protocol to be referenced.
Please read my earlier response.
First you need to remove the static setting as @trendy said. The OpenVPN server will push an IP address netmask and route to be applied to the tun0 interface as it is created (by the OpenVPN client process, not UCI).
It is no longer necessary to reference anything about OpenVPN in /etc/config/network. Include tun0 in a firewall zone as a device not as a network. If you trust everything on the VPN it can just be in the lan firewall zone. For more options as far as blocking connections, define a separate zone.
If the zone that the VPN interface is in allows input generally, or it has a specific rule allowing TCP port 22, an incoming connection to dropbear will be possible. Connections to services on the router itself are accepted directly on the interface, not forwarded.
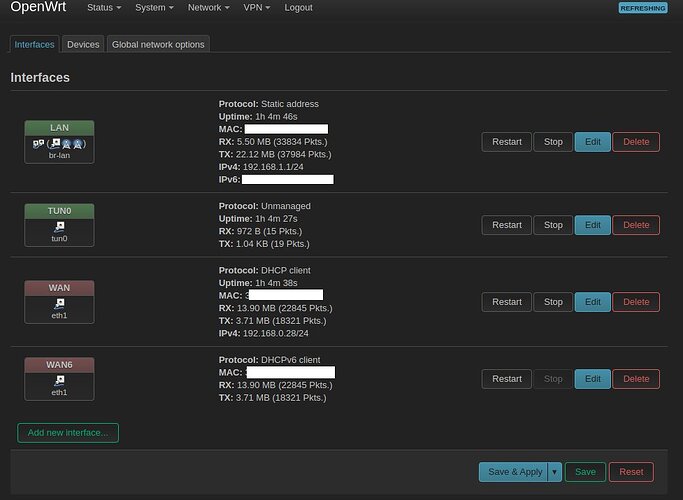
@mk24 yes I act as @trendy said. Please look attached image:
Yes I trust everything on the VPN.
But, no work!
Thank you
What address are you using when you attempt to ssh to the router over your OpenVPN connection?
Let's see the configs in text format:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/firewall
cat /etc/config/openvpn
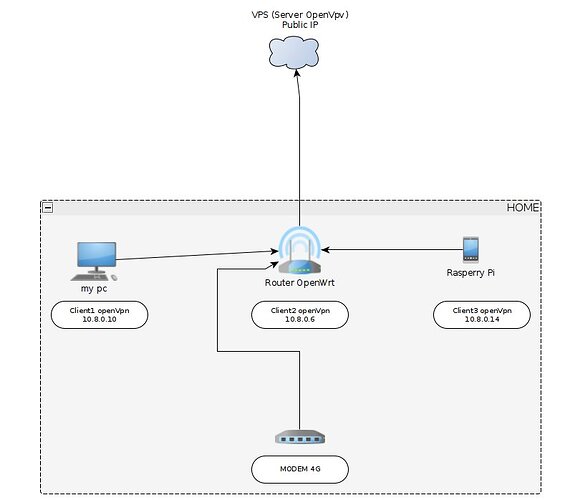
@psherman Before you lose time with my problem I want to show the schema of the system:
From "my pc" I can shh with server open vpn at address 10.8.0.1. From "my pc" I can ssh with Rasperry Pi at address 10.8.0.14 and I can ssh to Router OpenWrt at address 192.168.1.1 but not able to ssh to Router OpenWrt at address 10.8.0.6. Also from the VPS I'm not able to ssh to the router at address 10.8.0.6.
After this preamble, what output can I show you? which device?
Thank you very much.
Are there OpenVPN clients running on the PC, the Pi, and the router? If so, why? In most cases, the router would be the only device running OpenWrt, and your PC and Pi would be able to use the tunnel via the OpenWrt router.
Are there OpenVPN clients running on the PC, the Pi, and the router? If so, why?
Yes there are 3 client OpenVpn. On my pc only for test/devolepment. On Pi for safety. If OpenVPN on router fail, then I can to come in "house" through the PI.
What is the purpose of the main router's OpenVPN connection? Is it to create a full outbound tunnel (i.e. all of the traffic through the tunnel rather than the normal WAN)? or is it purely for remote access? or something else?
Only for remote access.
Ok... I suspect that if the OpenWrt's OpenVPN connection fails, so will the Pi. So I don't think you've really got a reliable backup plan, but we'll focus on the main issue.
So to summarize and make sure I understand
- all 3 devices (router, PC, Pi) have a tunnel running via the VPS.
- ssh PC (10.8.0.10) > VPS (10.8.0.1) works
- ssh PC (10.8.0.10) > Pi (10.8.0.14) works
- ssh PC (10.8.0.10) > Pi (10.8.0.14) > ssh Pi > router LAN (192.168.1.1) works
- ssh (any 10.8.0.0/24) > OpenWrt (10.8.0.6) fails
Is that all correct?
Let's verify that the OpenVPN connection is working from the OpenWrt side...
ssh into the router (using the 192.168.1.1 address), then ssh from there to 10.8.0.1 (VPS). Does it work? If not, can you ping successfully? If not, let's see the logs after you attempt to start the OpenVPN client on the OpenWrt router.
all 3 devices (router, PC, Pi) have a tunnel running via the VPS.
Yes
ssh PC (10.8.0.10) > VPS (10.8.0.1) works
Yes
ssh PC (10.8.0.10) > Pi (10.8.0.14) works
Yes
ssh PC (10.8.0.10) > Pi (10.8.0.14) > ssh Pi > router LAN (192.168.1.1) works
root@Pi:~# ssh 192.168.1.1
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ED21232 key fingerprint is SHA256:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx+xxxxxxxxxxxx.
Are you sure you want to continue connecting (yes/no/[fingerprint])?
ssh (any 10.8.0.0/24) > OpenWrt (10.8.0.6) fails
Yes
Let's verify that the OpenVPN connection is working from the OpenWrt side...
ssh into the router (using the 192.168.1.1 address), then ssh from there to 10.8.0.1 (VPS). Does
it work?
yes it work.
The ping work for all and everywhere. For the ping VPS does not response because I have blocked it.
Ok... let's see the config files I asked for earlier -- all from the OpenWrt router.
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:xxxx::/48'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan'
option ipaddr '192.168.1.1'
config device 'lan_dev'
option name 'eth0'
option macaddr 'xx:xx:xx:xx:xx:xx'
config interface 'wan'
option proto 'dhcp'
option device 'eth1'
config interface 'wan6'
option proto 'dhcpv6'
option device 'eth1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option blinkrate '2'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5'
config switch_port
option device 'switch0'
option port '1'
option led '6'
config switch_port
option device 'switch0'
option port '2'
option led '9'
config switch_port
option device 'switch0'
option port '5'
option led '2'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'tun0'
option device 'tun0'
option proto 'none'
config device
option name 'tun0'
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'tun0'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config openvpn 'OpenVpn_client'
option client '1'
option dev 'tun'
option proto 'udp'
option resolv_retry 'infinite'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/router.crt'
option key '/etc/openvpn/router.key'
option verb '3'
option remote 'xx.xx.xx.xx remote VPS IP'
option port '1194'
option comp_lzo 'yes'
option enabled '1'
option nobind '1'
This doesn't match the screenshots you posted earlier (in #23)
Anyway, remove the tun0 network from the wan zone and then do the following:
I have done, but no work.
Sorry.
let's see the latest firewall file
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'tun0'
config forwarding
option src 'vpn'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'vpn'
I don't see anything wrong at this point... is there anything in your firewall.user file?
Can you ssh from the router > pc and/or the router > pi (via the OpenVPN addresses)?
firewall.user is empty.
I can ssh from router > pc
I can ssh from router > pi
I can ssh from router > vps
all via OpenVPN addresses
Sorry
let's see the output from
ifconfig
(don't forget to redact your public IP from the WAN)