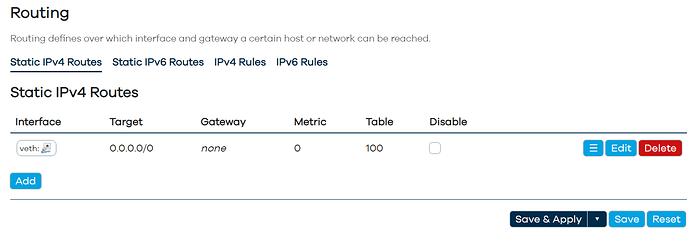
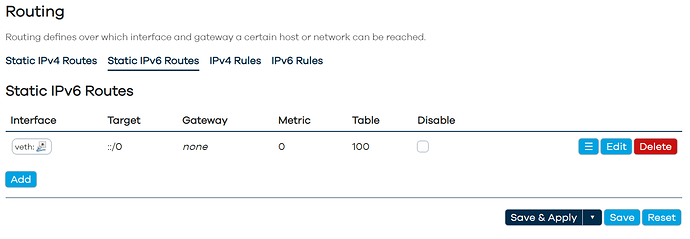
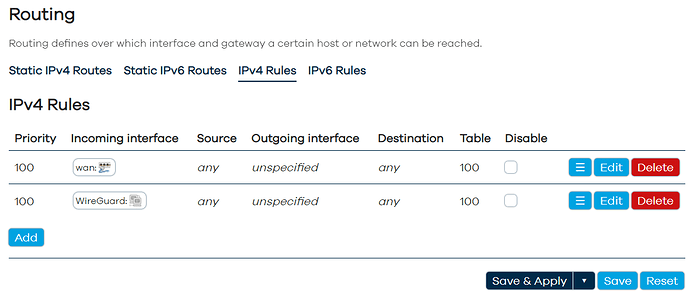
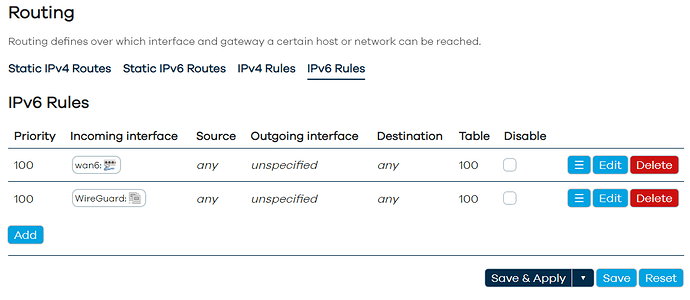
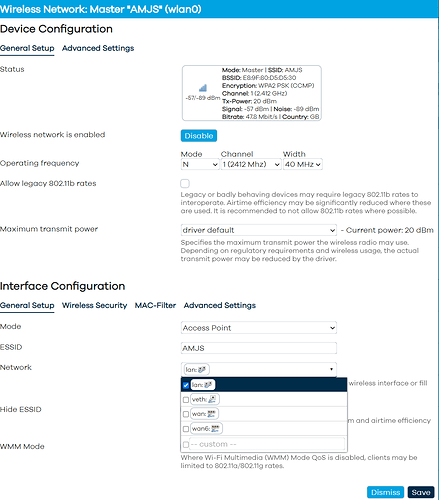
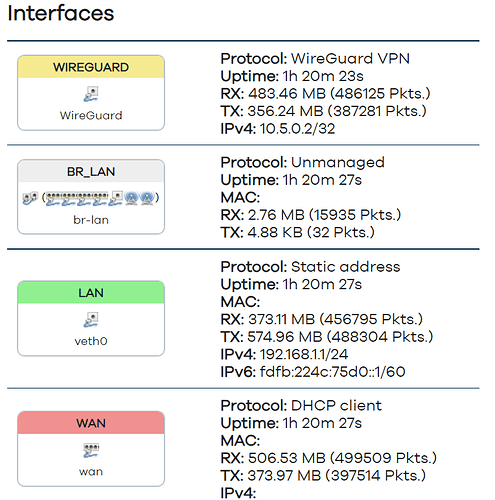
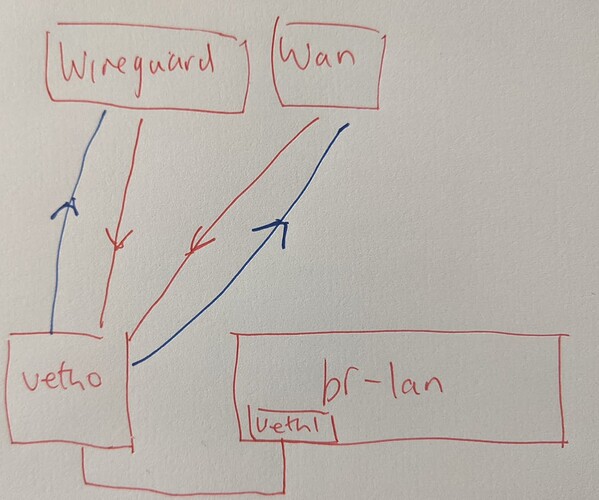
Thanks for your help @vgaetera. Last night I thought I saw it working, but it seems I am missing something. Can you see what I am missing? Right now I see only:
root@OpenWrt:~# tcpdump -vpni veth0
tcpdump: listening on veth0, link-type EN10MB (Ethernet), capture size 262144 bytes
06:49:26.634465 IP (tos 0x0, ttl 255, id 62024, offset 0, flags [none], proto UDP (17), length 203)
192.168.1.119.49160 > 255.255.255.255.6666: UDP, length 175
06:49:27.247711 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.120 tell 192.168.1.120, length 28
06:49:28.019859 IP (tos 0x0, ttl 255, id 51000, offset 0, flags [none], proto UDP (17), length 216)
192.168.1.179.49154 > 255.255.255.255.6667: UDP, length 188
06:49:28.425658 IP (tos 0x0, ttl 255, id 62416, offset 0, flags [none], proto UDP (17), length 203)
192.168.1.156.49159 > 255.255.255.255.6666: UDP, length 175
06:49:28.969674 IP (tos 0x0, ttl 255, id 1181, offset 0, flags [none], proto UDP (17), length 203)
192.168.1.192.49177 > 255.255.255.255.6666: UDP, length 175
06:49:29.202037 IP (tos 0x0, ttl 255, id 36749, offset 0, flags [none], proto UDP (17), length 203)
192.168.1.191.49178 > 255.255.255.255.6666: UDP, length 175
I have set as follows:
root@OpenWrt:~# ip route show table 100
default dev veth0 proto static scope link
root@OpenWrt:~# ip rule show all
0: from all lookup local
98: from all fwmark 0x20000/0xff0000 lookup WireGuard
99: from all fwmark 0x10000/0xff0000 lookup wan
100: from all iif wan lookup 100
100: from all iif WireGuard lookup 100
32766: from all lookup main
32767: from all lookup default
90064: from all iif lo lookup 100
root@OpenWrt:~# ip route show table all
default dev veth0 table 100 proto static scope link
default via 10.0.0.1 dev wan table wan
192.168.1.0/24 dev br-lan table wan proto kernel scope link src 192.168.1.1
default via 10.5.0.2 dev WireGuard table WireGuard
192.168.1.0/24 dev br-lan table WireGuard proto kernel scope link src 192.168.1.1
default via 10.0.0.1 dev wan proto static src 10.14.39.177
10.0.0.0/8 dev wan proto kernel scope link src 10.14.39.177
81.92.203.202 via 10.0.0.1 dev wan proto static
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
broadcast 10.0.0.0 dev wan table local proto kernel scope link src 10.14.39.177
local 10.5.0.2 dev WireGuard table local proto kernel scope host src 10.5.0.2
local 10.14.39.177 dev wan table local proto kernel scope host src 10.14.39.177
broadcast 10.255.255.255 dev wan table local proto kernel scope link src 10.14.39.177
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
default dev veth0 table 100 proto static metric 1024 pref medium
fd30:aae4:ef12:a800::/64 dev wan proto static metric 256 pref medium
unreachable fd30:aae4:ef12:a800::/64 dev lo proto static metric 2147483647 pref medium
fdfb:224c:75d0::/64 dev br-lan proto static metric 1024 pref medium
unreachable fdfb:224c:75d0::/48 dev lo proto static metric 2147483647 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
fe80::/64 dev wan proto kernel metric 256 pref medium
fe80::/64 dev br-lan proto kernel metric 256 pref medium
fe80::/64 dev wlan0 proto kernel metric 256 pref medium
fe80::/64 dev wlan1 proto kernel metric 256 pref medium
fe80::/64 dev ifb4WireGuard proto kernel metric 256 pref medium
fe80::/64 dev veth0 proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fd30:aae4:ef12:a800:: dev wan table local proto kernel metric 0 pref medium
local fd30:aae4:ef12:a800:ea9f:80ff:fed5:d52e dev wan table local proto kernel metric 0 pref medium
anycast fdfb:224c:75d0:: dev br-lan table local proto kernel metric 0 pref medium
local fdfb:224c:75d0::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev wan table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
anycast fe80:: dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan0 table local proto kernel metric 0 pref medium
anycast fe80:: dev ifb4WireGuard table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan1 table local proto kernel metric 0 pref medium
anycast fe80:: dev veth0 table local proto kernel metric 0 pref medium
local fe80::64ce:9dff:fe62:7a87 dev veth0 table local proto kernel metric 0 pref medium
local fe80::88a2:b7ff:fe87:5f2 dev ifb4WireGuard table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fed5:d52e dev wan table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fed5:d52f dev eth0 table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fed5:d52f dev br-lan table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fed5:d530 dev wlan0 table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fed5:d531 dev wlan1 table local proto kernel metric 0 pref medium
multicast ff00::/8 dev eth0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev wan table local proto kernel metric 256 pref medium
multicast ff00::/8 dev br-lan table local proto kernel metric 256 pref medium
multicast ff00::/8 dev wlan0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev wlan1 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev WireGuard table local proto kernel metric 256 pref medium
multicast ff00::/8 dev ifb4WireGuard table local proto kernel metric 256 pref medium
multicast ff00::/8 dev veth0 table local proto kernel metric 256 pref medium
veth0 Link encap:Ethernet HWaddr 72:D9:56:56:4B:F2
inet6 addr: fe80::70d9:56ff:fe56:4bf2/64 Scope:Link
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:1193 errors:0 dropped:0 overruns:0 frame:0
TX packets:18 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:217855 (212.7 KiB) TX bytes:3951 (3.8 KiB)
veth1 Link encap:Ethernet HWaddr 82:D8:4E:68:77:97
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:18 errors:0 dropped:0 overruns:0 frame:0
TX packets:1193 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3951 (3.8 KiB) TX bytes:217855 (212.7 KiB)