ok thanks for the information but do you have to create a veth interface for the input?
or should I create once with the rule that I said and once with what you propose to me?
yes i'm on fw4
ok thanks for the information but do you have to create a veth interface for the input?
or should I create once with the rule that I said and once with what you propose to me?
yes i'm on fw4
on my gaming pc which is connected via a switch to my openwrt router
I put like this ip.dst==192.168.2.160 and there I see the traffic marked CS5 or CS4
on the other hand if I put ip.Src==192.168.2.160. packages are CS0
in the past with iptables i make like that
##CALL OF DUTY
iptables -t mangle -A POSTROUTING -p udp --dst 192.168.2.160 -j DSCP --sport 30000:45000 --dport 3074 --set-dscp-class CS5 -m comment --comment "Dopam-IT_1987-UDP-1"
iptables -t mangle -A POSTROUTING -p udp --src 192.168.2.160 -j DSCP --sport 3074 --dport 30000:45000 --set-dscp-class CS5 -m comment --comment "Dopam-IT_1987-UDP-2"
iptables -t mangle -A POSTROUTING -p tcp --dst 192.168.2.160 -j DSCP --dport 50000:65535 --sport 3074 --set-dscp-class CS5 -m comment --comment "Dopam-IT_1987-TCP-3"
iptables -t mangle -A POSTROUTING -p tcp --src 192.168.2.160 -j DSCP --dport 3074 --sport 50000:65535 --set-dscp-class CS5 -m comment --comment "Dopam-IT_1987-TCP-4"
iptables -t mangle -A POSTROUTING -p udp --src 192.168.2.160 -j DSCP --sport 3074 --dport 3074 --set-dscp-class CS5 -m comment --comment "cod-UDP-6"
i don't remember but i can make the same things in traffic rules
I've always wondered why I didn't wash the packages at the entrance, an important question is raised in my opinion.
Ingress is different kettle of fish, I am just trying to address the fact that the otherwise impressive qosify does not yet allow classification by internal IP addresses, and I had realized that for egress traffic existing firewall/iptables/nftables methods already suffice. Since egress is often much narrower than ingress, even just the capability to do ip/port based marking for prioritisation for egress might already be helpful.
For ingress either a veth pair or instantiating the download shaper on a LAN-interface (in a dual-port wired only router) would allow the same method to work.
it's really interesting how to create the lanveth suddenly,
I know you need kmod-veth and in unmanaged interface then firewall lan but it tells me device not present
config rule
option name 'BROADCAST VIDEO TWITCH'
list proto 'tcp'
option src '*'
option src_port '1935 1936 2935 2396'
list dest_ip '192.168.2.160'
option target 'DSCP'
option set_dscp 'CS3'
option enabled '0'
list src_ip '192.168.2.160'
option dest '*'
option dest_port '1935 1936 2935 2396'
I live on twitch from time to time and according to your very good explanation it could be fair to classify like that, right? for TWITCH
Well, if you only see the default DSCP0/TOS0 on there that is expected, as the firewall rule will change the DSCP of the packets once they reach the router. So think like:
gaming pc (DSCP 0) -> router br-lan (DSCP 0) -> once the packets are received the router changes the DSCP according to the rule -> router wan (DSCP EF)
since sqm/qosify should live on wan as well they will see EF and hence will be able to steer packets from the gaming PC to a higher priority tin.
BUT be careful, cake does not work with hard rate limits for the tiers, so if you push too much traffic into the higher tins, some of that traffic will end up in the Best Effort tin... for typical gaming traffic that will not matter, but if you download say a big game update (and your priority rule included TCP) that will cause issues, but I assume nobody will download big data files while playing ayways.
I am happy to believe that, but unlike @dlakelan I have zero first hand experience with setting up veth interfaces, so would respectfully refer you into his expertise.
if [ $USEVETHDOWN = "yes" ] ; then
ip link show lanveth || ip link add lanveth type veth peer name lanbrport
LAN=lanveth
ip link set lanbrport master $LANBR
ip route flush table 100
ip route add default via $LAN table 100
ip rule add iif $WAN table 100
ip link set lanveth up
ip link set lanbrport up
fi
two ways
## Use "Veth" method
if [ "$DOWN_METHOD" = "veth" ] ; then
## Suppress warnings about missing public prefix.
uci show dhcp.odhcpd.loglevel | grep "3" > /dev/null 2>&1 || {
uci set dhcp.odhcpd.loglevel='3'
uci commit dhcp
/etc/init.d/odhcpd restart
}
## Stop IFB interface.
ip link show ifb4${WAN} > /dev/null 2>&1 && {
ip link set ifb4${WAN} down
ip link del ifb4${WAN}
}
## Creating Veth interface.
uci show network.veth > /dev/null 2>&1 || {
uci set network.veth=interface
uci set network.veth.proto='none'
uci set network.veth.device='lanveth'
uci add_list firewall.@zone[0].network='veth'
uci commit network
uci commit firewall
/etc/init.d/network restart
/etc/init.d/firewall restart > /dev/null 2>&1
}
## Start Veth interface.
ip link show lanveth > /dev/null 2>&1 || ip link add lanveth type veth peer name lanbrport
VETH="lanveth"
ip link set lanveth up
ip link set lanbrport up
ip link set lanbrport master $LAN
ip rule del priority 100 > /dev/null 2>&1
ip -6 rule del priority 100 > /dev/null 2>&1
ip route flush table 100 > /dev/null 2>&1
ip -6 route flush table 100 > /dev/null 2>&1
ip route add default dev $VETH table 100
ip -6 route add default dev $VETH table 100
ip rule add iif $WAN priority 100 table 100
ip -6 rule add iif $WAN priority 100 table 100
fi
![]()
seems good but not sure
so lets say i want to prioritize a port or port range is this the correct config
27005 is my port but the other port of the server changes when i join another server
This still tries to mark incoming packets, which will be to late for cake on ifb-wan...
The source zone should either be any or LAN, and the destination zone wan or any... for the port you need to select the stable one.
I think, but have not tested that 27005 should work as well as 27000-27100, that is I think one can add port ranges there (not 100% sure what separator is used, - or mayby :?)
@grrr2 with that
config rule
list proto 'udp'
option src '*'
option dest 'lan'
list dest_ip '192.168.2.160'
option target 'DSCP'
option enabled '1'
option set_dscp 'CS5'
option name 'CS5 gaming'
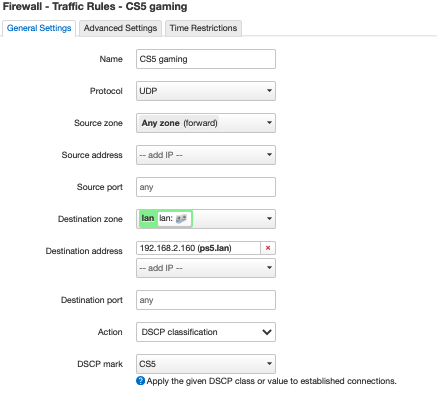
this is for ip.dst==..... postrouting
ok are you using this with sqm or qosify?
wired or wireless i'm play wired
sqm layer_cake
wired
ok I'm going the same with qosify and remove the gaming class it would look like you want to test
config defaults
list defaults /etc/qosify/*.conf
option dscp_icmp besteffort
option dscp_default_udp besteffort
option dscp_default_tcp besteffort
config class browsing
option ingress CS0
option egress CS0
option prio_max_avg_pkt_len 575
option dscp_prio AF41
option bulk_trigger_pps 1000
option bulk_trigger_timeout 10
option dscp_bulk CS1
config class bulk
option ingress CS1
option egress CS1
config class besteffort
option ingress CS0
option egress CS0
config class network_services
option ingress CS2
option egress CS2
config class broadcast_video
option ingress CS3
option egress CS3
config class multimedia_conferencing
option ingress AF42
option egress AF42
option prio_max_avg_pkt_len 575
option dscp_prio AF41
config class telephony
option ingress EF
option egress EF
config interface wan
option name wan
option disabled 0
option bandwidth_up 16mbit
option bandwidth_down 56mbit
option overhead_type bridged-ptm
# defaults:
option ingress 1
option egress 1
option mode diffserv4
option nat 1
option host_isolate 1
option autorate_ingress 0
option ingress_options ""
option egress_options "wash"
option options "ether-vlan"
config device wandev
option disabled 1
option name wan
option bandwidth 100mbit
config rule
list proto 'udp'
option target 'DSCP'
option name 'CS7 gaming'
option src 'lan'
list src_ip '192.168.2.160'
option dest 'wan'
option set_dscp 'CS7'
config rule
option target 'DSCP'
list proto 'udp'
option name 'CS7 GAMING 2'
option src 'wan'
option dest 'lan'
list dest_ip '192.168.2.160'
option set_dscp 'CS7'
ok so i came make 2 Game my charachter is louder and slow ![]()
do you has try layer_Ctinfo ?
config queue 'eth1'
option qdisc 'cake'
option ingress_ecn 'ECN'
option egress_ecn 'ECN'
option itarget 'auto'
option etarget 'auto'
option enabled '1'
option interface 'wan'
option download '56000'
option upload '16000'
option debug_logging '0'
option verbosity '5'
option qdisc_advanced '1'
option squash_dscp '1'
option qdisc_really_really_advanced '1'
option linklayer 'ethernet'
option overhead '26'
option linklayer_advanced '1'
option tcMTU '2047'
option tcTSIZE '128'
option tcMPU '0'
option iqdisc_opts 'diffserv4'
option eqdisc_opts 'diffserv4'
option linklayer_adaptation_mechanism 'cake'
option script 'layer_cake_ct.qos'
option squash_ingress '0'
@N1K, don't try it, this is incorrect. By default this file is not in the system.
nope i has download the files
opkg update
opkg install luci-app-sqm kmod-sched-ctinfo iptables-mod-hashlimit ipset nano
# Install modified layer_cake to sqm-scripts
wget https://gist.githubusercontent.com/heri16/06c94b40f0d30f11e3a82166eca718f3/raw/layer_cake_ct.qos -O /usr/lib/sqm/layer_cake_ct.qos
wget https://gist.github.com/heri16/06c94b40f0d30f11e3a82166eca718f3/raw/layer_cake_ct.qos.help -O /usr/lib/sqm/layer_cake_ct.qos.help
so you can try i think
you can try this file will enter the system of the router ![]() which normally is not there then I do not know the configuration that amteza speaks who did it with xato
which normally is not there then I do not know the configuration that amteza speaks who did it with xato
@segal72
Stop it, you are going to confuse him/her. What you offer is incomplete, you are not helping, mate.
ok so what is the way to get this ct_info with the config can you create a topic to help others or is it too complicated ![]()