Hi,
I've seen other topics but they do not seem to have my same problem. Maybe this is not a really openWRT thread but here I have seen lot of expert!
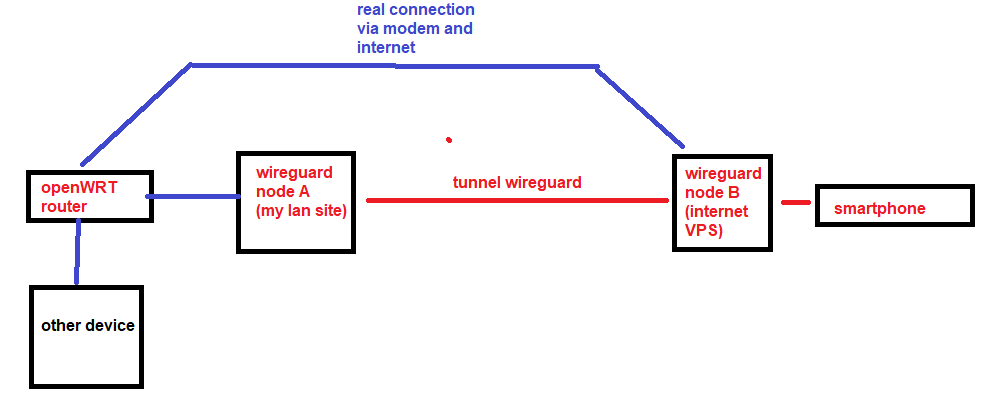
I have configured a tunnel as described here
and shown in the following picture.
Please note that:
- openWRT router is not used as wireguard tunnel node: infact I'm using a more powerful x86 linux based machine to do this. I just want to access to the router and other machines behind the tunnel.
- wireguard lan site node A is physically connected directly to the router: I think the router itself drops down the packets and do not answer when I try to connect to it from the otherside;
- if I connect to services exposed on the wireguard lan node A, using the lan ip (not the wireguard one), I can reach them;
- the tcpdump -i wg0 on the wireguard node A produce the following lines, it seems to forward data to the router... so, it is the router that do not accept them because they come from wireguard node B ip 10.0.0.1? How can they be translated? I actived the forwarding and masquerating rule on wireguard node A...
tcpdump -i wg0
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on wg0, link-type RAW (Raw IP), capture size 262144 bytes
18:05:40.697381 IP 10.0.0.1.40924 > router1.lan.https: Flags [S], seq 2141972520, win 65535, options [mss 1240,sackOK,TS val 438081211 ecr 0,nop,wscale 9], length 0
18:05:40.962499 IP 10.0.0.1.40926 > router1.lan.https: Flags [S], seq 2731689407, win 65535, options [mss 1240,sackOK,TS val 438081467 ecr 0,nop,wscale 9], length 0
18:05:41.767663 IP 10.0.0.1.40924 > router1.lan.https: Flags [S], seq 2141972520, win 65535, options [mss 1240,sackOK,TS val 438082280 ecr 0,nop,wscale 9], length 0
18:05:42.003119 IP 10.0.0.1.40926 > router1.lan.https: Flags [S], seq 2731689407, win 65535, options [mss 1240,sackOK,TS val 438082520 ecr 0,nop,wscale 9], length 0
18:05:43.772652 IP 10.0.0.1.40924 > router1.lan.https: Flags [S], seq 2141972520, win 65535, options [mss 1240,sackOK,TS val 438084281 ecr 0,nop,wscale 9], length 0
18:05:44.000681 IP 10.0.0.1.40926 > router1.lan.https: Flags [S], seq 2731689407, win 65535, options [mss 1240,sackOK,TS val 438084520 ecr 0,nop,wscale 9], length 0
18:05:47.770006 IP 10.0.0.1.40924 > router1.lan.https: Flags [S], seq 2141972520, win 65535, options [mss 1240,sackOK,TS val 438088281 ecr 0,nop,wscale 9], length 0
18:05:47.999470 IP 10.0.0.1.40926 > router1.lan.https: Flags [S], seq 2731689407, win 65535, options [mss 1240,sackOK,TS val 438088521 ecr 0,nop,wscale 9], length 0
18:05:55.769834 IP 10.0.0.1.40924 > router1.lan.https: Flags [S], seq 2141972520, win 65535, options [mss 1240,sackOK,TS val 438096281 ecr 0,nop,wscale 9], length 0
18:05:56.003046 IP 10.0.0.1.40926 > router1.lan.https: Flags [S], seq 2731689407, win 65535, options [mss 1240,sackOK,TS val 438096520 ecr 0,nop,wscale 9], length 0
This is the wireguard config on node A:
cat /etc/wireguard/wg0.conf
[Interface]
Address = 10.0.0.186/32
PrivateKey = the_KEY
DNS = 1.1.1.1
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o enol -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o enol -j MASQUERADE
[Peer]
PublicKey = the_KEY
#AllowedIPs =0.0.0.0/0
AllowedIPs = 10.0.0.0/24
PersistentKeepalive = 10
Endpoint = VPS_PUBLIC_IP:51820