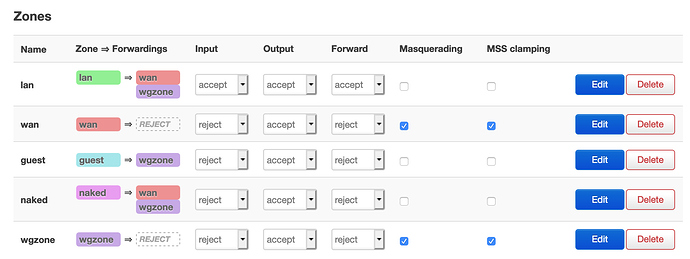
I think I've fixed it; by:
- Allow forwarding from guest to the wireguard zone
- Allow forwarding from my non-wireguard network to wireguard zone and WAN
- added to the PBR a rule to redirect all traffic from the non-wireguard network across the WAN.
Screenshots:
and /etc/config/vpn-policy-routing:
config vpn-policy-routing 'config'
option verbosity '2'
option ipv6_enabled '0'
option ipset_enabled '1'
option dnsmasq_enabled '0'
option strict_enforcement '1'
option boot_timeout '30'
option chain_control '1'
option enabled '1'
config policy
option name 'TV'
option local_address '192.168.1.100'
option interface 'wan'
option proto 'tcp'
option chain 'PREROUTING'
config policy
option chain 'PREROUTING'
option interface 'wan'
option name 'Hello'
option local_address '192.168.1.102'
option proto 'tcp'
config policy
option proto 'tcp'
option chain 'PREROUTING'
option interface 'wan'
option name 'Homerun'
option local_address '192.168.1.101'
config policy
option proto 'tcp'
option chain 'PREROUTING'
option interface 'wan'
option name 'Naked'
option local_address '192.168.3.0/24'