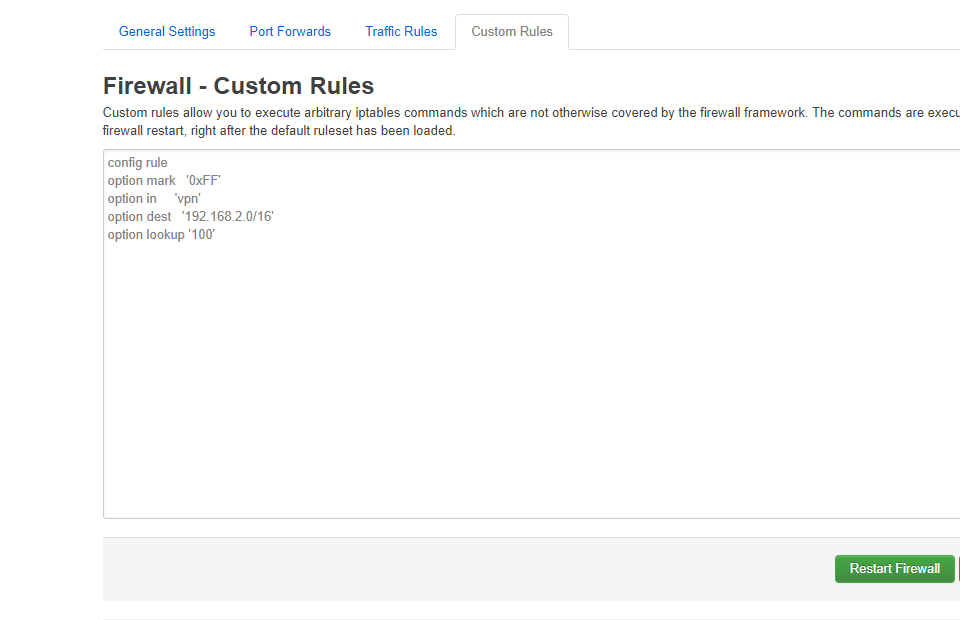
In VPN firewall zone change the forward from reject to accept.
For the rule and route check the links in this post:
Hello,
1°)
I do to dosable gateway redirect on vpn server:
sed -i -e "
/^push.*redirect-gateway/s/^/#/
" /etc/openvpn/zoogvpn_us4.ovpn
service openvpn restart
and
uci add firewall forwarding
uci set firewall.@forwarding[-1].src='lan'
uci set firewall.@forwarding[-1].dest='wan'
service openvpn restart
But if the vpn it's start my wifi doesn't work
2°) I have an interface zoogvpn_vpn with ip 192.168.2.1 (Lan interface has ip 192.168.1.1) (Bridge interfaces not activated)

i created a wifi for the VPN named VPN on network zoogvpn_vpn
The DHCP it's enable (not ignore ) but it's don't attrubute any IP when i'm connected on wifi vpn
I have do this and click on restart Firewall but i'm not shure it's do somethings
For the static route i have to do ?
config 'route' 'MyVPN'
option 'interface' 'lan'
option 'target' '192.168.2.0'
option 'netmask' '255.255.255.0'
option 'gateway' '192.168.1.1'
Regards
Nope this is wrong.
In the previous post you had the wifi VPN interface and the ZOOGVPN_VPN in the same firewall zone, but the Forward rule was reject, so I told you to make it accept.
Then the rules and the routes are configured inside /etc/config/network not in firewall.
Firstly, thanks for your patience ...
I'm too bad ...I resset again my config.
I will try step by step ...
I config the vpn ans is working.
To beguining i would like to stop the VPN from the network, it will be only on 1 wifi specific vpn .
I do this
sed -i -e "
/^push.*redirect-gateway/s/^/#/
" /etc/openvpn/zoogvpn_us4.ovpn
service openvpn restart
But when the vpn it's start i'm automaticly on the vpn ..
My conf :
cat /etc/config/network; cat /etc/config/firewall; cat /etc/config/wireless ; cat /etc/config/dhcp ; ip -4 addr ; ip -4 ro ; ip -4 ru
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb9:99da:a865::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '50:64:2b:b2:71:cc'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option peerdns '0'
list dns '208.67.222.222'
list dns '208.67.220.220'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
config interface 'zoogvpn_vpn'
option proto 'none'
option ifname 'tun0'
option metric '10'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'zoogvpn_vpn'
option forward 'ACCEPT'
config forwarding
option dest 'vpn'
option src 'lan'
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:00.0/0000:01:00.0'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:01.0/0000:02:00.0'
option htmode 'VHT80'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
list dhcp_option '6,208.67.222.222,208.67.220.220'
list dhcp_option '6,8.8.8.8,8.8.4.4'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.0.253/24 brd 192.168.0.255 scope global eth0.2
valid_lft forever preferred_lft forever
9: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 100
inet 10.8.11.14 peer 10.8.11.13/32 scope global tun0
valid_lft forever preferred_lft forever
0.0.0.0/1 via 10.8.11.13 dev tun0
default via 192.168.0.254 dev eth0.2 src 192.168.0.253
10.8.11.1 via 10.8.11.13 dev tun0
10.8.11.13 dev tun0 scope link src 10.8.11.14
23.229.0.242 via 192.168.0.254 dev eth0.2
128.0.0.0/1 via 10.8.11.13 dev tun0
192.168.0.0/24 dev eth0.2 scope link src 192.168.0.253
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
It's this the pb ?
config forwarding
option dest 'vpn'
option src 'lan'
The problem to start with is that you still install the default route:
Post again the ovpn configuration.
redirect-gateway def1 should not be there and just in case route-nopull would make sure the server is not pushing anything to you.
Thanks,
Here the ovpn file
cat /etc/openvpn/zoogvpn_us4.ovpn
client
dev tun
proto udp
remote us4.east.zoogvpn.com 1194
redirect-gateway
cipher AES-256-CBC
auth SHA256
resolv-retry infinite
nobind
redirect-gateway
persist-key
persist-tun
persist-remote-ip
<ca>
-----BEGIN CERTIFICATE-----
MIIDjTCCAvagAwIBAgIJALBMSxQKBBi6MA0GCSqGSIb3DQEBBQUAMIGMMQswCQYD
VQQGEwJVUzENMAsGA1UECBMEVVRBSDESMBAGA1UEBxMJU2FsdCBMYWtlMQ8wDQYD
VQQKEwZab29nVFYxEjAQBgNVBAsTCUFNRVIxIFZQTjESMBAGA1UEAxMJWm9vZ1RW
IENBMSEwHwYJKoZIhvcNAQkBFhJzdXBwb3J0QHpvb2d0di5jb20wHhcNMTQwNjA5
MjEyNzU2WhcNMjQwNjA2MjEyNzU2WjCBjDELMAkGA1UEBhMCVVMxDTALBgNVBAgT
BFVUQUgxEjAQBgNVBAcTCVNhbHQgTGFrZTEPMA0GA1UEChMGWm9vZ1RWMRIwEAYD
VQQLEwlBTUVSMSBWUE4xEjAQBgNVBAMTCVpvb2dUViBDQTEhMB8GCSqGSIb3DQEJ
ARYSc3VwcG9ydEB6b29ndHYuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKB
gQC7kIiPpph0xTYtmdEASddEHxgQVWAeg8gv+AzLEvvmcIHjsO4Rl0x765r7PViE
FDlrE6ShXUoOLxmS7mLj1fOlMPTnTGS5xr37mQmAjWJllLzoncYSuWOhY0tIOAsE
0R2juwyddyZCnu+iqC/MFLKG3ldgA4dOfVwnbMVcdtj+QQIDAQABo4H0MIHxMB0G
A1UdDgQWBBSkH6efW4hbVd5TIBJYrBpMs6/lPjCBwQYDVR0jBIG5MIG2gBSkH6ef
W4hbVd5TIBJYrBpMs6/lPqGBkqSBjzCBjDELMAkGA1UEBhMCVVMxDTALBgNVBAgT
BFVUQUgxEjAQBgNVBAcTCVNhbHQgTGFrZTEPMA0GA1UEChMGWm9vZ1RWMRIwEAYD
VQQLEwlBTUVSMSBWUE4xEjAQBgNVBAMTCVpvb2dUViBDQTEhMB8GCSqGSIb3DQEJ
ARYSc3VwcG9ydEB6b29ndHYuY29tggkAsExLFAoEGLowDAYDVR0TBAUwAwEB/zAN
BgkqhkiG9w0BAQUFAAOBgQAZ/cLbuSDEGZXf+aA5OAQnFmsO4fT8/Gq3B4FMa3mr
Ddi2VQ01tGzCalK4KDHRNAkqcuf5ao4suj8XEqi5fyXgvZwn2Cs+We+epDG7WXUn
sbNy1hhTFbi+3jl3He84KUoulPO6CFYgN44juuN3qjVklioxg+IhGsoHHe7AHPKw
FA==
-----END CERTIFICATE-----
</ca>
fast-io
auth-user-pass /etc/openvpn/zoogvpn_auth.txt
log-append /var/log/openvpn.log
status /var/log/openvpn-status.log
script-security 2
up /etc/openvpn/updns
down /etc/openvpn/downdns
reneg-bytes 0
reneg-sec 0
verb 3
The pb it's here ?
Since you're running a separate interface for VPN users you don't want to change anything with your LAN. The LAN will always be a regular non-VPN connection direct to the Internet through the WAN.
So you need two new network interfaces i.e. vpnuser and vpntun. Remember to keep interface names short and by convention use only lower case.
vpnuser is a bridge with a static IP (with a range that doesn't overlap any of your other networks); it has a DHCP server and a link to at least one wifi or wired physical network. The users of the VPN will connect here.
vpntun's "physical" connection is the tunnel to the VPN that OpenVPN creates after it connects to the VPN server.
Then you make two separate firewall zones which can have the same names vpnuser and vpntun. These are analogous to the existing lan and wan and are going to work about the same way. Thus zone vpntun needs to have masq enabled. Then you have a forwarding rule from vpnuser to vpntun.
Again all of this is separate from and operates in parallel with the existing lan and wan. Leave those alone.
yes
It cannot be bridged with tun0, as NAT will not work. vpnuser and zoogvpn must be different interfaces.
I think the eth0 physical interface is wrong, as well as the DHCP client protocol.
You already have zoogvpn interface which is the tunnel interface to your vpn provider. You don't need them both.
vpntun (or your already established zoogvpn) is not a bridge, and has only tun0. vpnuser is a bridge and has at least one wifi or wired interface for the VPN users in your house to connect to.
Since there are vlans on eth0 you always refer to eth0 with a VLAN number. Do not connect plain eth0 to anything. The two VLANs now are LAN (1) and WAN (2). If you want to support wired VPN users you need to create a new VLAN (3) in the switch connecting the CPU tagged to at least one physical port untagged, then attach eth0.3 to vpnuser.
Hi i delete 2 line ( redirect-gateway) of my ovpn files but all trafic pass by vpn ever ...
cat /etc/openvpn/zoogvpn_us4.ovpn
client
dev tun
proto udp
remote us4.east.zoogvpn.com 1194
cipher AES-256-CBC
auth SHA256
resolv-retry infinite
nobind
persist-key
persist-tun
persist-remote-ip
<ca>
-----BEGIN CERTIFICATE-----
MIIDjTCCAvagAwIBAgIJALBMSxQKBBi6MA0GCSqGSIb3DQEBBQUAMIGMMQswCQYD
VQQGEwJVUzENMAsGA1UECBMEVVRBSDESMBAGA1UEBxMJU2FsdCBMYWtlMQ8wDQYD
VQQKEwZab29nVFYxEjAQBgNVBAsTCUFNRVIxIFZQTjESMBAGA1UEAxMJWm9vZ1RW
IENBMSEwHwYJKoZIhvcNAQkBFhJzdXBwb3J0QHpvb2d0di5jb20wHhcNMTQwNjA5
MjEyNzU2WhcNMjQwNjA2MjEyNzU2WjCBjDELMAkGA1UEBhMCVVMxDTALBgNVBAgT
BFVUQUgxEjAQBgNVBAcTCVNhbHQgTGFrZTEPMA0GA1UEChMGWm9vZ1RWMRIwEAYD
VQQLEwlBTUVSMSBWUE4xEjAQBgNVBAMTCVpvb2dUViBDQTEhMB8GCSqGSIb3DQEJ
ARYSc3VwcG9ydEB6b29ndHYuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKB
gQC7kIiPpph0xTYtmdEASddEHxgQVWAeg8gv+AzLEvvmcIHjsO4Rl0x765r7PViE
FDlrE6ShXUoOLxmS7mLj1fOlMPTnTGS5xr37mQmAjWJllLzoncYSuWOhY0tIOAsE
0R2juwyddyZCnu+iqC/MFLKG3ldgA4dOfVwnbMVcdtj+QQIDAQABo4H0MIHxMB0G
A1UdDgQWBBSkH6efW4hbVd5TIBJYrBpMs6/lPjCBwQYDVR0jBIG5MIG2gBSkH6ef
W4hbVd5TIBJYrBpMs6/lPqGBkqSBjzCBjDELMAkGA1UEBhMCVVMxDTALBgNVBAgT
BFVUQUgxEjAQBgNVBAcTCVNhbHQgTGFrZTEPMA0GA1UEChMGWm9vZ1RWMRIwEAYD
VQQLEwlBTUVSMSBWUE4xEjAQBgNVBAMTCVpvb2dUViBDQTEhMB8GCSqGSIb3DQEJ
ARYSc3VwcG9ydEB6b29ndHYuY29tggkAsExLFAoEGLowDAYDVR0TBAUwAwEB/zAN
BgkqhkiG9w0BAQUFAAOBgQAZ/cLbuSDEGZXf+aA5OAQnFmsO4fT8/Gq3B4FMa3mr
Ddi2VQ01tGzCalK4KDHRNAkqcuf5ao4suj8XEqi5fyXgvZwn2Cs+We+epDG7WXUn
sbNy1hhTFbi+3jl3He84KUoulPO6CFYgN44juuN3qjVklioxg+IhGsoHHe7AHPKw
FA==
-----END CERTIFICATE-----
</ca>
fast-io
auth-user-pass /etc/openvpn/zoogvpn_auth.txt
log-append /var/log/openvpn.log
status /var/log/openvpn-status.log
script-security 2
up /etc/openvpn/updns
down /etc/openvpn/downdns
reneg-bytes 0
reneg-sec 0
verb 3
The vpnuser interface (eth0 ip 192.168.2.1) was bridged with my wirless Network named WifiVPN (wlan0-1)

DHCP Works, when i'm connect on i have a correct range of ip adresse but internet does not works
Adresse IPv4. . . . . . . . . . . . . .: 192.168.2.134(préféré)
Masque de sous-réseau. . . . . . . . . : 255.255.255.0
Bail obtenu. . . . . . . . . . . . . . : mardi 2 juillet 2019 16:44:32
Bail expirant. . . . . . . . . . . . . : mercredi 3 juillet 2019 04:44:32
Passerelle par défaut. . . . . . . . . : 192.168.2.1
Serveur DHCP . . . . . . . . . . . . . : 192.168.2.1
IAID DHCPv6 . . . . . . . . . . . : 316207818
DUID de client DHCPv6. . . . . . . . : 00-01-00-01-23-E4-D8-1E-C8-5B-76-C4-79-B0
Serveurs DNS. . . . . . . . . . . . . : 192.168.2.1
NetBIOS sur Tcpip. . . . . . . . . . . : Activé
Thanks for your help
Please post again the output of these commands:
cat /etc/config/network; cat /etc/config/firewall; cat /etc/config/wireless ; cat /etc/config/dhcp ; ip -4 addr ; ip -4 ro ; ip -4 ru
Thanks !
cat /etc/config/network; cat /etc/config/firewall; cat /etc/config/wireless ; cat /etc/config/dhcp ; ip -4 addr ; ip -4 ro ; ip -4 ru
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb9:99da:a865::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '50:64:2b:b2:71:cc'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option peerdns '0'
list dns '208.67.222.222'
list dns '208.67.220.220'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
config interface 'zoogvpn_vpn'
option proto 'none'
option ifname 'tun0'
option metric '10'
config interface 'vpnuser'
option proto 'static'
option ifname 'eth0'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option type 'bridge'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'ACCEPT'
option network 'zoogvpn_vpn'
config forwarding
option dest 'vpn'
option src 'lan'
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:00.0/0000:01:00.0'
option htmode 'HT20'
option country '00'
option legacy_rates '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Wifi'
option encryption 'psk2'
option key '0102030405'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:01.0/0000:02:00.0'
option htmode 'VHT80'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-iface
option device 'radio0'
option mode 'ap'
option encryption 'none'
option ssid 'WifiVPN'
option network 'vpnuser'
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option serversfile '/tmp/adb_list.overall'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
list dhcp_option '6,208.67.222.222,208.67.220.220'
list dhcp_option '6,8.8.8.8,8.8.4.4'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vpnuser'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'vpnuser'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
7: br-vpnuser: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-vpnuser
valid_lft forever preferred_lft forever
8: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.0.253/24 brd 192.168.0.255 scope global eth0.2
valid_lft forever preferred_lft forever
default via 192.168.0.254 dev eth0.2 src 192.168.0.253
192.168.0.0/24 dev eth0.2 scope link src 192.168.0.253
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.2.0/24 dev br-vpnuser scope link src 192.168.2.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Take that out. Using plain eth0 when there are VLANs active on eth0 will not work. For now VPN users can use only wifi. Once that is working you can look at adding wired VPN access.
That is not what you want. The VPN users are out on their own network, you don't want the LAN to have anything to do with the VPN. So use this instead.
config forwarding
option src vpnuser
option dest vpnThus you also need a vpnuser zone like this:
config zone
option name 'vpnuser'
option network 'vpnuser'
option input ACCEPT
option output ACCEPT
option forward ACCEPTI don't now if the config is better but now no wifi works ...
cat /etc/config/network; cat /etc/config/firewall; cat /etc/config/wireless ; cat /etc/config/dhcp ; ip -4 addr ; ip -4 ro ; ip -4 ru
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb9:99da:a865::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '50:64:2b:b2:71:cc'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option peerdns '0'
list dns '208.67.222.222'
list dns '208.67.220.220'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
config interface 'zoogvpn_vpn'
option proto 'none'
option ifname 'tun0'
option metric '10'
config interface 'vpnuser'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option type 'bridge'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'ACCEPT'
option network 'zoogvpn_vpn'
config forwarding
option dest 'wan'
option src 'lan'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'vpnuser'
option forward 'ACCEPT'
option network 'vpnuser'
config forwarding
option dest 'vpn'
option src 'vpnuser'
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:00.0/0000:01:00.0'
option htmode 'HT20'
option country '00'
option legacy_rates '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Wifi'
option encryption 'psk2'
option key '0102030405'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:01.0/0000:02:00.0'
option htmode 'VHT80'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-iface
option device 'radio0'
option mode 'ap'
option encryption 'none'
option ssid 'WifiVPN'
option network 'vpnuser'
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option serversfile '/tmp/adb_list.overall'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
list dhcp_option '6,208.67.222.222,208.67.220.220'
list dhcp_option '6,8.8.8.8,8.8.4.4'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vpnuser'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'vpnuser'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.0.253/24 brd 192.168.0.255 scope global eth0.2
valid_lft forever preferred_lft forever
8: br-vpnuser: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-vpnuser
valid_lft forever preferred_lft forever
11: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 100
inet 10.8.11.6 peer 10.8.11.5/32 scope global tun0
valid_lft forever preferred_lft forever
0.0.0.0/1 via 10.8.11.5 dev tun0
default via 192.168.0.254 dev eth0.2 src 192.168.0.253
10.8.11.1 via 10.8.11.5 dev tun0
10.8.11.5 dev tun0 scope link src 10.8.11.6
23.229.0.242 via 192.168.0.254 dev eth0.2
128.0.0.0/1 via 10.8.11.5 dev tun0
192.168.0.0/24 dev eth0.2 scope link src 192.168.0.253
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.2.0/24 dev br-vpnuser scope link src 192.168.2.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Do you mean that nor the lan or the vpnuser wifi work?
For the lan, you still need to get rid of the default gateway from OpenVPN.
For the vpnuser wifi to work you also need the following in config/network
config rule
option in 'vpnuser'
option lookup '100'
config 'route' 'vpn'
option 'interface' 'zoogvpn_vpn'
option 'target' '0.0.0.0'
option 'netmask' '0.0.0.0'
option 'table' '100'
Hello,
The default gateway from OpenVPN it's not desactived ? How can i verify it ?
Where can i add option lookup '100' in network, firwall vpnnuser zone ?
I had a static route i don't now it's the good way and i have now 
config route
option interface 'zoogvpn_vpn'
option target '0.0.0.0'
option netmask '0.0.0.0'
Is it very strange,
On Lan and Wifi(no vpn) it's works only if i stop the openvpn connection.
On the wifivpn it's works only if i start again the openvpn connection (it's look normal)but not on all internet for exemple http://www.record.pt/ i have DNS_PROBE_FINISHED_NXDOMAIN but http://www.abola.pt/ it's works
It's a dns Pb ?
You can verify with the ip -4 ro command, if you see these 2 lines it means that you still get the default route from vpn tunnel.
0.0.0.0/1 via 10.8.11.5 dev tun0
128.0.0.0/1 via 10.8.11.5 dev tun0