Thank's for you help again ...
But i have updated my version OpenWrt 18.06.1 to OpenWrt 18.06.2 and i loose my vpn config ...i try to restore an archive but it's do not work ...
so i try to reinstall my VPN but it's not work ...
i do this :
ssh root@192.168.1.1
opkg update
opkg install openvpn-openssl luci-app-openvpn
opkg install libustream-openssl ca-bundle ca-certificates
->Cmder
λ cd
cd vpn
C:\vpn
λ scp vpnclient.ovpn root@192.168.1.1:/etc/openvpn/vpnclient.ovpn
vpnclient.ovpn 100% 1520 367.3KB/s 00:00
ssh root@192.168.1.1
cat > /etc/openvpn/userpass.txt << EOF
myVPN_Username
myVPN_Password
EOF
OPENVPN_LOCATION=US4
VPN_PROVIDER=ZOOGVPN
OVPN_INAME="$VPN_PROVIDER"_"$OPENVPN_LOCATION"
uci show openvpn.ZOOGVPN_US4
openvpn.ZOOGVPN_US4=openvpn
openvpn.ZOOGVPN_US4.enabled='0'
openvpn.ZOOGVPN_US4.config='/etc/openvpn/ZOOGVPN_US4.ovpn'
sed -i '/auth-user-pass*/a log-append /var/log/openvpn.log\nstatus /var/log/openvpn-status.log' /etc/openvpn/*.ovpn
uci set network."$VPN_PROVIDER"_vpn=interface
uci set network."$VPN_PROVIDER"_vpn.proto='none'
uci set network."$VPN_PROVIDER"_vpn.ifname='tun0'
uci set network."$VPN_PROVIDER"_vpn.metric='10'
uci add firewall zone
uci set firewall.@zone[-1].name='vpn'
uci set firewall.@zone[-1].input='REJECT'
uci set firewall.@zone[-1].output='ACCEPT'
uci set firewall.@zone[-1].forward='REJECT'
uci set firewall.@zone[-1].masq='1'
uci set firewall.@zone[-1].mtu_fix='1'
uci add_list firewall.@zone[-1].network="$VPN_PROVIDER"_vpn
uci add firewall forwarding
uci set firewall.@forwarding[-1].src='lan'
uci set firewall.@forwarding[-1].dest='vpn'
uci commit
/etc/init.d/firewall reload
/etc/init.d/network restart
/etc/init.d/openvpn restart
uci add_list dhcp.lan.dhcp_option='6,208.67.222.222,208.67.220.220'
uci add_list dhcp.lan.dhcp_option='6,8.8.8.8,8.8.4.4'
uci set network.wan.peerdns='0' # Désactive les DNS fournis par DHCP
uci del network.wan.dns # Supprime les DNS existants s'ils existent
uci add_list network.wan.dns='208.67.222.222'
uci add_list network.wan.dns='208.67.220.220'
uci add_list network.wan.dns='8.8.8.8'
uci add_list network.wan.dns='8.8.4.4'
My vpnclient.ovpn file :
client
dev tun
proto udp
remote us4.east.zoogvpn.com 1194
cipher AES-256-CBC
auth SHA256
resolv-retry infinite
nobind
persist-key
persist-tun
persist-remote-ip
-----BEGIN CERTIFICATE-----
MIIDjTCCAvagAwIBAgIJALBMSxQKBBi6MA0GCSqGSIb3DQEBBQUAMIGMMQswCQYD
VQQGEwJVUzENMAsGA1UECBMEVVRBSDESMBAGA1UEBxMJU2FsdCBMYWtlMQ8wDQYD
VQQKEwZab29nVFYxEjAQBgNVBAsTCUFNRVIxIFZQTjESMBAGA1UEAxMJWm9vZ1RW
IENBMSEwHwYJKoZIhvcNAQkBFhJzdXBwb3J0QHpvb2d0di5jb20wHhcNMTQwNjA5
MjEyNzU2WhcNMjQwNjA2MjEyNzU2WjCBjDELMAkGA1UEBhMCVVMxDTALBgNVBAgT
BFVUQUgxEjAQBgNVBAcTCVNhbHQgTGFrZTEPMA0GA1UEChMGWm9vZ1RWMRIwEAYD
VQQLEwlBTUVSMSBWUE4xEjAQBgNVBAMTCVpvb2dUViBDQTEhMB8GCSqGSIb3DQEJ
ARYSc3VwcG9ydEB6b29ndHYuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKB
gQC7kIiPpph0xTYtmdEASddEHxgQVWAeg8gv+AzLEvvmcIHjsO4Rl0x765r7PViE
FDlrE6ShXUoOLxmS7mLj1fOlMPTnTGS5xr37mQmAjWJllLzoncYSuWOhY0tIOAsE
0R2juwyddyZCnu+iqC/MFLKG3ldgA4dOfVwnbMVcdtj+QQIDAQABo4H0MIHxMB0G
A1UdDgQWBBSkH6efW4hbVd5TIBJYrBpMs6/lPjCBwQYDVR0jBIG5MIG2gBSkH6ef
W4hbVd5TIBJYrBpMs6/lPqGBkqSBjzCBjDELMAkGA1UEBhMCVVMxDTALBgNVBAgT
BFVUQUgxEjAQBgNVBAcTCVNhbHQgTGFrZTEPMA0GA1UEChMGWm9vZ1RWMRIwEAYD
VQQLEwlBTUVSMSBWUE4xEjAQBgNVBAMTCVpvb2dUViBDQTEhMB8GCSqGSIb3DQEJ
ARYSc3VwcG9ydEB6b29ndHYuY29tggkAsExLFAoEGLowDAYDVR0TBAUwAwEB/zAN
BgkqhkiG9w0BAQUFAAOBgQAZ/cLbuSDEGZXf+aA5OAQnFmsO4fT8/Gq3B4FMa3mr
Ddi2VQ01tGzCalK4KDHRNAkqcuf5ao4suj8XEqi5fyXgvZwn2Cs+We+epDG7WXUn
sbNy1hhTFbi+3jl3He84KUoulPO6CFYgN44juuN3qjVklioxg+IhGsoHHe7AHPKw
FA==
-----END CERTIFICATE-----
fast-io
auth-user-pass
reneg-bytes 0
reneg-sec 0
verb 3
The vpn do not start ...

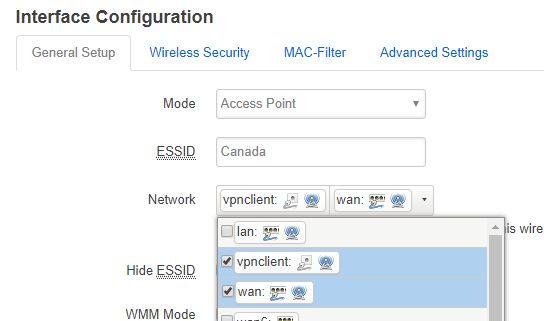
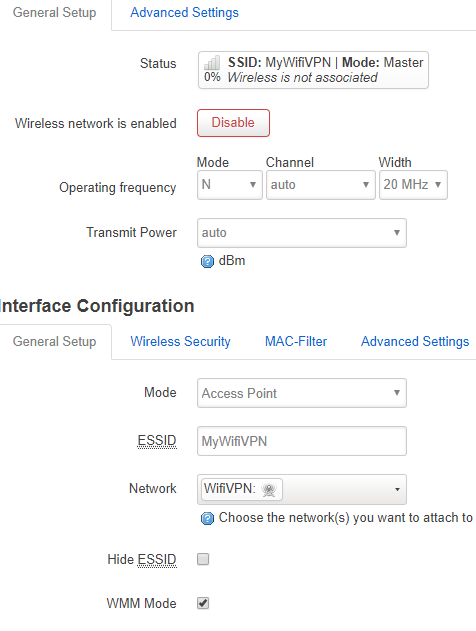
 and i have activated DHCP on
and i have activated DHCP on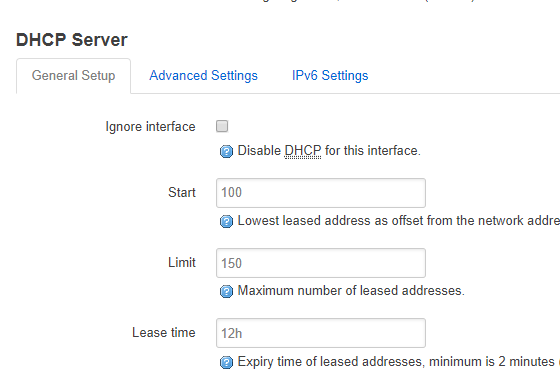 .
.