Hey Guys,
I'm trying to figure out why my port forward isn't working.
First of all some information about the situation.
Due to the quarantine i want to host a Cities Skyline Multiplayer Server for me and my friends.
I have setup the Port Forwarding as explained in many Tutorials.
I have tried numerous of configuration and due to this i have also collected many Data about it.
Now some Infos about the actual configs and findings:
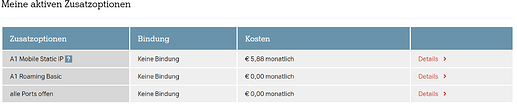
I have bought some options from my ISP:
- All ports are open
- Static IP: (84.20.xx.xx/28) / Gateway: 84.20.xx.xx
Below is a screenshot of the ordered and ACTIVE options of my ISP:
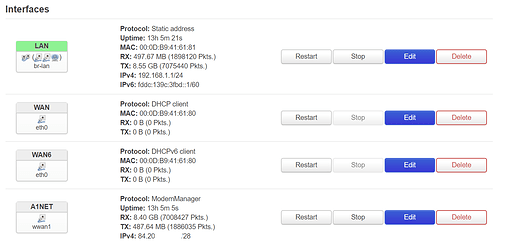
Now i will attach a screenshot of my Port Forwarding configured and active in OpenWRT done through LuCi because im not that familiar with the configuration of firewalls through CLI's:
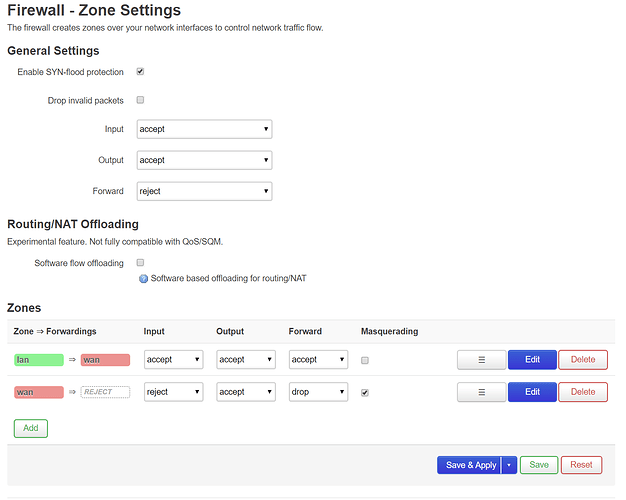
Also here's a screenshot of my overall Firewall settings:
Also i opened the Ports in the Windows Firewall:
Now the curious things:
With the following tcpdump command:
tcpdump -pnvvi wwan1 port 49150
i sniff on the WAN port with tcpdump running on the OpenWRT device it get this when making a port check with Port Checker:
tcpdump: listening on wwan1, link-type RAW (Raw IP), capture size 262144 bytes
06:58:25.801812 IP (tos 0x0, ttl 49, id 63213, offset 0, flags [DF], proto TCP (6), length 60)
198.199.98.246.38094 > 84.20.187.167.49150: Flags [S], cksum 0x6f23 (correct), seq 1773835175, win 14600, options [mss 1400,sackOK,TS val 2937873738 ecr 0,nop,wscale 8], length 0
06:58:25.802020 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40)
84.20.187.167.49150 > 198.199.98.246.38094: Flags [R.], cksum 0x2427 (correct), seq 0, ack 1773835176, win 0, length 0
06:58:25.986937 IP (tos 0x0, ttl 49, id 23, offset 0, flags [DF], proto TCP (6), length 60)
198.199.98.246.38096 > 84.20.187.167.49150: Flags [S], cksum 0x8993 (correct), seq 2102551918, win 14600, options [mss 1400,sackOK,TS val 2937873785 ecr 0,nop,wscale 8], length 0
06:58:25.987227 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40)
84.20.187.167.49150 > 198.199.98.246.38096: Flags [R.], cksum 0x3ec6 (correct), seq 0, ack 2102551919, win 0, length 0
06:58:26.174914 IP (tos 0x0, ttl 49, id 64572, offset 0, flags [DF], proto TCP (6), length 60)
198.199.98.246.38097 > 84.20.187.167.49150: Flags [S], cksum 0x7697 (correct), seq 1542625691, win 14600, options [mss 1400,sackOK,TS val 2937873831 ecr 0,nop,wscale 8], length 0
06:58:26.175190 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40)
84.20.187.167.49150 > 198.199.98.246.38097: Flags [R.], cksum 0x2bf8 (correct), seq 0, ack 1542625692, win 0, length 0
And thats the actual conclusion why i think my ISP isn't blocking it because the pakets are arriving.
And thats the next problem because i dont know if tcpdump actually sniffs/catches only the outgoing request or also the incoming?
But when sniffing on the Bridged LAN or only on the eth1 i dont get any pakets or sniffs.
What am i did wrong?
I ask you kindly to answer as detailed as possible so other inexperienced users and also me will understand the answers and may take advantage of this Thread.
Thanks in Advance for help!!
Answer from @psherman:
Your source and destination zones in the port forwarding configuration are backwards.
Thanks for the input!
Changed this setting but anyways when sniffing with tcpdump on eth1 or br-lan i still cant get a sniff.
root@OpenWrt:~# tcpdump -pnvvi eth1 port 49150
tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
^C
0 packets captured
0 packets received by filter
0 packets dropped by kernel
root@OpenWrt:~# tcpdump -pnvvi br-lan port 49150
tcpdump: listening on br-lan, link-type EN10MB (Ethernet), capture size 262144 bytes
^C
0 packets captured
4 packets received by filter
0 packets dropped by kernel
Answer #2 of @psherman:
You also may need to add the port number 49150 to the internal port field.
Make sure the service is active and can be reached from within your network. Once that is proven to work, test from outside your network
Also changed this but anyways tcpdump still can't sniff any pakets on the eth1 or br-lan when making a port check with the above mentioned port checker.