Hello there!
Hoping for some guidance / help to resolve an issue I've been grappling with for the last few weeks.
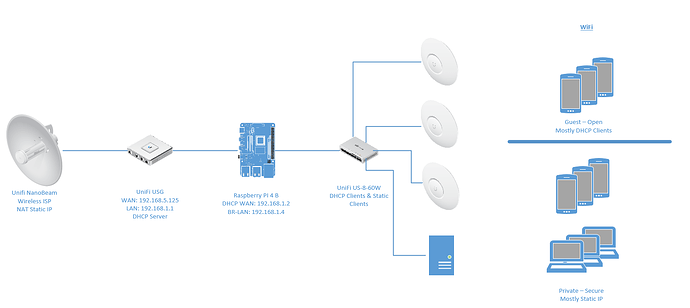
My home network is a Wireless ISP, connected to a Unifi Secure Gateway (USG), then to a Unifi Switch that provides both wired and wireless connectivity (the latter through Unifi APs). I have a secure private network, and an open WiFi guest network.
I have added a Raspberry PI 4 B between the USG and Switch, and the config for the ExpressVPN is working with no errors, and I can ping / traceroute on the vpn/tun0 interface. However all traffic regardless of using --pull-filter ignore redirect-gateway, or route-noexec, etc... all traffic passes between the LAN and WAN on the rPI and never goes over the VPN.
The outcome I'm hoping to achieve is the following:
- Push all LAN traffic through the VPN; then once working...
- Implement Split Tunnelling (perhaps using PBR / VPN-Bypass) so that only certain devices use the VPN, e.g. TV/Netflix, access my remote server from my home server, have guest-clients not use the VPN, and then selectively add private devices to use the VPN in the future as required.
The network looks like this:
Please note that I don't wish to use the rPI for WiFi as it just can't cover the distances required. Also note that I have set the firewall back to something that appears to work with a LAN-to-LAN config (including a VPN that gets not traffic!).
Having followed MANY(!) threads here and on Reddit, I'm stuck. I feel this is a routing and firewall issue but having tried lots of different variations, I simply can't get it to what I want. All help greatly appreciated.
Configs as per @trendy output, as follows:
root@OpenWrt:~# ubus call system board; \
> uci export network; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
{
"kernel": "5.10.146",
"hostname": "OpenWrt",
"system": "ARMv8 Processor rev 3",
"model": "Raspberry Pi 4 Model B Rev 1.4",
"board_name": "raspberrypi,4-model-b",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.2",
"revision": "r19803-9a599fee93",
"target": "bcm27xx/bcm2711",
"description": "OpenWrt 22.03.2 r19803-9a599fee93"
}
}
package network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option ula_prefix 'fd98:b5b9:9ffb::/48'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
list dns '8.8.8.8'
option delegate '0'
option device 'br-lan'
option ipaddr '192.168.1.4'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config device
option name 'br-lan'
option type 'bridge'
option ipv6 '0'
option acceptlocal '1'
list ports 'eth0'
list ports 'eth1'
config device
option name 'eth0'
option ipv6 '0'
option acceptlocal '1'
config device
option name 'eth1'
option acceptlocal '1'
option ipv6 '0'
config device
option name 'tun0'
option acceptlocal '1'
option ipv6 '0'
config interface 'vpn'
option proto 'static'
option device 'tun0'
package firewall
config defaults
option output 'ACCEPT'
option synflood_protect '1'
option input 'ACCEPT'
option forward 'REJECT'
config zone 'vpn'
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'tun0'
option masq '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'lan'
option forward 'ACCEPT'
config zone 'wan'
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
list network 'wan'
list network 'vpn'
config forwarding
option src 'lan'
option dest 'wan'
config include
option path '/etc/firewall.user'
config forwarding
option src 'vpn'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'vpn'
head: /etc/firewall.user: No such file or directory
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group defaul t qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP gro up default qlen 1000
inet 192.168.1.4/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
7: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 500
inet 10.159.0.194 peer 10.159.0.193/32 scope global tun0
valid_lft forever preferred_lft forever
0.0.0.0/1 via 10.159.0.193 dev tun0
default via 192.168.1.1 dev br-lan proto static
10.159.0.1 via 10.159.0.193 dev tun0
10.159.0.193 dev tun0 proto kernel scope link src 10.159.0.194
45.x.x.x via 192.168.1.1 dev br-lan [ExpressVPN IP]
128.0.0.0/1 via 10.159.0.193 dev tun0
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.4
local 10.159.0.194 dev tun0 table local proto kernel scope host src 10.159.0.194
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0 .1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168 .1.4
local 192.168.1.4 dev br-lan table local proto kernel scope host src 192.168.1.4
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.1 68.1.4
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
###OpenVPN config '#' are some attempts to get it to work...
dev tun
fast-io
persist-key
persist-tun
nobind
remote australia-sydney-ca-version-2.expressnetw.com 1195
remote-random
pull
#pull-filter ignore redirect-gateway
#pull-filter ignore dhcp-option
#pull-filter ignore route
#route-noexec
#route-nopull
#route 0.0.0.0 192.0.0.0 net_gateway
#route 10.0.0.0 192.0.0.0 net_gateway
#route 128.0.0.0 192.0.0.0 net_gateway
#route 192.0.0.0 192.0.0.0 net_gateway
comp-lzo no
tls-client
verify-x509-name Server name-prefix
remote-cert-tls server
key-direction 1
route-method exe
route-delay 2
tun-mtu 1500
fragment 1300
mssfix 1200
verb 3
data-ciphers AES-256-CBC
keysize 256
auth SHA512
sndbuf 524288
rcvbuf 524288
auth-user-pass "/etc/openvpn/eVPN.auth"
auth-nocache