issue: no internet on vlan1 or vlan2,I try many times,but no success at all,someone help me please
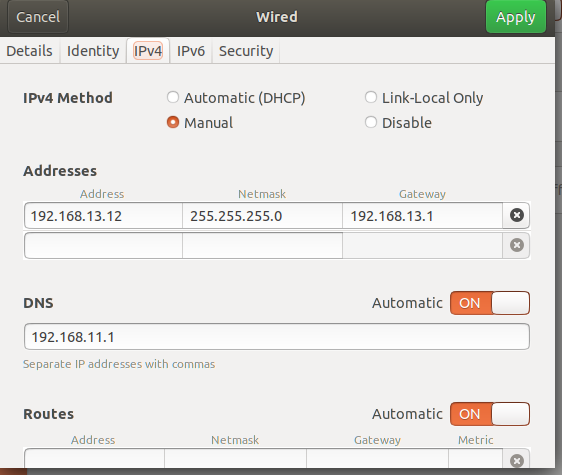
my main openwrt lan ip 192.168.11.1
my layer 3 switch (another openwrt)
both router turn of dhcp server
main openwrt setting
layer 3 switch setting
my pc network setting
Are you masquerading on the wan interface of the main router?
@trendy
iptables -t nat -A POSTROUTING -s 192.168.13.0/24 -o wan -j MASQUERADE
mikma
June 8, 2020, 11:32pm
4
The kernel name of the wan interface is "eth0.2" in your case, and that's the name you need to use with iptables. But the rules shouldn't be needed since a masquerade rule which match any source address is added by default anyway when you enable masquerading.
1 Like
mikma:
masquerading
yes,I used eth0.2 before ,but it didn't work
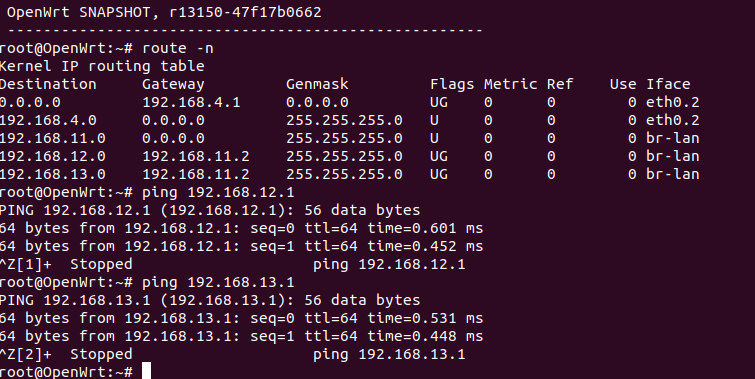
I can use ssh ping 192.168.11.1 on layer 3 switch ,but can't ping any website
Please copy the output of the following commands from both routers and post it here using the "Preformatted text </> " button:
uci export network; uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
ls -l /etc/resolv.* /tmp/resolv.*; head -n -0 /etc/resolv.* /tmp/resolv.*
mk24
June 9, 2020, 8:24am
7
The switch machine needs a default route to 11.1. As it is now that second router doesn't know how to send packets from anything (a 12 or 13 machine, or even itself) to the Internet. The PC at 13.12 has been configured to gateway through 13.1, but again 13.1 does not know it needs to forward to 11.1
Thank you very much
root@OpenWrt:~# uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd83:c41e:263f::/48'
config interface 'lan'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.12.1'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'xx:xx:43:1d:35:ff'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 3 4'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1 2'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 5'
option vid '3'
config interface 'lanb'
option ifname 'eth0.2'
option proto 'static'
option ipaddr '192.168.13.1'
option netmask '255.255.255.0'
config interface 'lanc'
option ifname 'eth0.3'
option proto 'static'
option ipaddr '192.168.11.2'
option netmask '255.255.255.0'
config route
option target '0.0.0.0'
option gateway '192.168.11.1'
option netmask '0.0.0.0'
option interface 'lan'
root@OpenWrt:~# uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ra_management '1'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# uci export firewall
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan lanb lanc'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
root@OpenWrt:~# head -n -0 /etc/firewall.user
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
root@OpenWrt:~#
root@OpenWrt:~# iptables-save -c
# Generated by iptables-save v1.8.4 on Tue Jun 9 04:47:23 2020
*nat
:PREROUTING ACCEPT [2024:259018]
:INPUT ACCEPT [40:7594]
:OUTPUT ACCEPT [127:8636]
:POSTROUTING ACCEPT [338:23142]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[2024:259018] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[0:0] -A PREROUTING -i eth0.1 -m comment --comment "!fw3" -j zone_lan_prerouting
[1518:154006] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_lan_prerouting
[506:105012] -A PREROUTING -i eth0.3 -m comment --comment "!fw3" -j zone_lan_prerouting
[338:23142] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o eth0.1 -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_lan_postrouting
[211:14506] -A POSTROUTING -o eth0.3 -m comment --comment "!fw3" -j zone_lan_postrouting
[211:14506] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[2024:259018] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Tue Jun 9 04:47:23 2020
# Generated by iptables-save v1.8.4 on Tue Jun 9 04:47:23 2020
*mangle
:PREROUTING ACCEPT [8207:2179171]
:INPUT ACCEPT [1589:129659]
:FORWARD ACCEPT [4819:1806494]
:OUTPUT ACCEPT [1559:138832]
:POSTROUTING ACCEPT [6348:1943460]
COMMIT
# Completed on Tue Jun 9 04:47:23 2020
# Generated by iptables-save v1.8.4 on Tue Jun 9 04:47:23 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[1020:69360] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[570:60287] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[348:31438] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[6:360] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[0:0] -A INPUT -i eth0.1 -m comment --comment "!fw3" -j zone_lan_input
[31:3363] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_lan_input
[191:25486] -A INPUT -i eth0.3 -m comment --comment "!fw3" -j zone_lan_input
[4785:1804333] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[3556:1713702] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A FORWARD -i eth0.1 -m comment --comment "!fw3" -j zone_lan_forward
[1229:90631] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0.3 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[1020:69360] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[512:68664] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[511:68584] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o eth0.1 -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_lan_output
[1:80] -A OUTPUT -o eth0.3 -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[6:360] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_lan_dest_ACCEPT -o eth0.1 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[1230:90711] -A zone_lan_dest_ACCEPT -o eth0.3 -m comment --comment "!fw3" -j ACCEPT
[1229:90631] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[1229:90631] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[1229:90631] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[222:28849] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[222:28849] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[1:80] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[1:80] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[0:0] -A zone_lan_src_ACCEPT -i eth0.1 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[31:3363] -A zone_lan_src_ACCEPT -i eth0.2 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[191:25486] -A zone_lan_src_ACCEPT -i eth0.3 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[0:0] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[0:0] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[0:0] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
COMMIT
# Completed on Tue Jun 9 04:47:23 2020
root@OpenWrt:~# ip -4 addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.12.1/24 brd 192.168.12.255 scope global eth0.1
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.13.1/24 brd 192.168.13.255 scope global eth0.2
valid_lft forever preferred_lft forever
8: eth0.3@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.11.2/24 brd 192.168.11.255 scope global eth0.3
valid_lft forever preferred_lft forever
root@OpenWrt:~# ip -4 addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.12.1/24 brd 192.168.12.255 scope global eth0.1
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.13.1/24 brd 192.168.13.255 scope global eth0.2
valid_lft forever preferred_lft forever
8: eth0.3@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.11.2/24 brd 192.168.11.255 scope global eth0.3
valid_lft forever preferred_lft forever
root@OpenWrt:~# ip -4 ro li tab all
192.168.11.0/24 dev eth0.3 scope link src 192.168.11.2
192.168.12.0/24 dev eth0.1 scope link src 192.168.12.1
192.168.13.0/24 dev eth0.2 scope link src 192.168.13.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.11.0 dev eth0.3 table local scope link src 192.168.11.2
local 192.168.11.2 dev eth0.3 table local scope host src 192.168.11.2
broadcast 192.168.11.255 dev eth0.3 table local scope link src 192.168.11.2
broadcast 192.168.12.0 dev eth0.1 table local scope link src 192.168.12.1
local 192.168.12.1 dev eth0.1 table local scope host src 192.168.12.1
broadcast 192.168.12.255 dev eth0.1 table local scope link src 192.168.12.1
broadcast 192.168.13.0 dev eth0.2 table local scope link src 192.168.13.1
local 192.168.13.1 dev eth0.2 table local scope host src 192.168.13.1
broadcast 192.168.13.255 dev eth0.2 table local scope link src 192.168.13.1
root@OpenWrt:~# ip -4 ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
root@OpenWrt:~# ls -l /etc/resolv.* /tmp/resolv.*
lrwxrwxrwx 1 root root 16 Jun 8 19:16 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Jun 9 02:39 /tmp/resolv.conf
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 0 Jun 9 02:39 resolv.conf.auto
root@OpenWrt:~# ls -l /etc/resolv.* /tmp/resolv.*
lrwxrwxrwx 1 root root 16 Jun 8 19:16 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Jun 9 02:39 /tmp/resolv.conf
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 0 Jun 9 02:39 resolv.conf.auto
root@OpenWrt:~# head -n -0 /etc/resolv.* /tmp/resolv.*
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
........................next reply for main router
here for main router
root@OpenWrt:~# uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc9:c5d8:8009::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.11.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'xx:xx:xx:da:80:ba'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
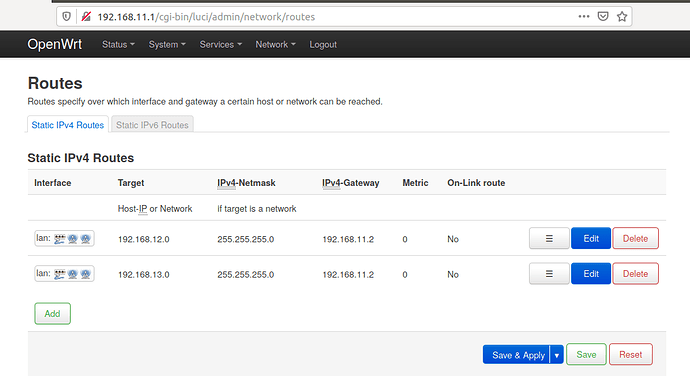
config route
option interface 'lan'
option target '192.168.12.0'
option netmask '255.255.255.0'
option gateway '192.168.11.2'
option metric '2'
config route
option interface 'lan'
option target '192.168.13.0'
option netmask '255.255.255.0'
option gateway '192.168.11.2'
option metric '2'
root@OpenWrt:~# uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ra_management '1'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# uci export firewall
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option flow_offloading '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
root@OpenWrt:~# head -n -0 /etc/firewall.user
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
root@OpenWrt:~# iptables-save -c
# Generated by iptables-save v1.8.4 on Tue Jun 9 19:14:25 2020
*nat
:PREROUTING ACCEPT [1420:434874]
:INPUT ACCEPT [118:8347]
:OUTPUT ACCEPT [618:38488]
:POSTROUTING ACCEPT [46:3251]
:MINIUPNPD - [0:0]
:MINIUPNPD-POSTROUTING - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[1420:434874] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[608:58336] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[812:376538] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[1050:79667] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[1004:76416] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[608:58336] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[1004:76416] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[1004:76416] -A zone_wan_postrouting -j MINIUPNPD-POSTROUTING
[1004:76416] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[812:376538] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[812:376538] -A zone_wan_prerouting -j MINIUPNPD
COMMIT
# Completed on Tue Jun 9 19:14:25 2020
# Generated by iptables-save v1.8.4 on Tue Jun 9 19:14:25 2020
*raw
:PREROUTING ACCEPT [6473:918593]
:OUTPUT ACCEPT [3095:564007]
:zone_lan_helper - [0:0]
[2474:226987] -A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Tue Jun 9 19:14:25 2020
# Generated by iptables-save v1.8.4 on Tue Jun 9 19:14:25 2020
*mangle
:PREROUTING ACCEPT [6476:918749]
:INPUT ACCEPT [4060:355160]
:FORWARD ACCEPT [1557:181861]
:OUTPUT ACCEPT [3099:564775]
:POSTROUTING ACCEPT [4625:745384]
[251:15060] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Tue Jun 9 19:14:25 2020
# Generated by iptables-save v1.8.4 on Tue Jun 9 19:14:25 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [6:504]
:MINIUPNPD - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[352:24631] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[3714:330841] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[3515:312724] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[10:600] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[157:12878] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[42:5239] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[1557:181861] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[982:125502] -A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD
[982:125502] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[575:56359] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[352:24631] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[2752:541140] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[2109:502032] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[637:38604] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[31:1677] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[11:3562] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[10:600] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[575:56359] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[575:56359] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[157:12878] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[157:12878] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[0:0] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[0:0] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[157:12878] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[31:1252] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[1181:93711] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -j MINIUPNPD
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[42:5239] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[42:5239] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[637:38604] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[637:38604] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[42:5239] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Tue Jun 9 19:14:25 2020
root@OpenWrt:~# ip -4 addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
57: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.11.1/24 brd 192.168.11.255 scope global br-lan
valid_lft forever preferred_lft forever
59: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.4.167/24 brd 192.168.4.255 scope global eth0.2
valid_lft forever preferred_lft forever
root@OpenWrt:~# ip -4 ro li tab all
default via 192.168.4.1 dev eth0.2 proto static src 192.168.4.167
192.168.4.0/24 dev eth0.2 proto kernel scope link src 192.168.4.167
192.168.11.0/24 dev br-lan proto kernel scope link src 192.168.11.1
192.168.12.0/24 via 192.168.11.2 dev br-lan proto static metric 2
192.168.13.0/24 via 192.168.11.2 dev br-lan proto static metric 2
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.4.0 dev eth0.2 table local proto kernel scope link src 192.168.4.167
local 192.168.4.167 dev eth0.2 table local proto kernel scope host src 192.168.4.167
broadcast 192.168.4.255 dev eth0.2 table local proto kernel scope link src 192.168.4.167
broadcast 192.168.11.0 dev br-lan table local proto kernel scope link src 192.168.11.1
local 192.168.11.1 dev br-lan table local proto kernel scope host src 192.168.11.1
broadcast 192.168.11.255 dev br-lan table local proto kernel scope link src 192.168.11.1
root@OpenWrt:~# ip -4 ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
root@OpenWrt:~# ls -l /etc/resolv.* /tmp/resolv.*
lrwxrwxrwx 1 root root 16 May 6 08:59 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Jun 9 19:12 /tmp/resolv.conf
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 50 Jun 9 18:54 resolv.conf.auto
root@OpenWrt:~# head -n -0 /etc/resolv.* /tmp/resolv.*
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
@mk24
trendy
June 9, 2020, 12:19pm
11
The default gateway is not configured properly.
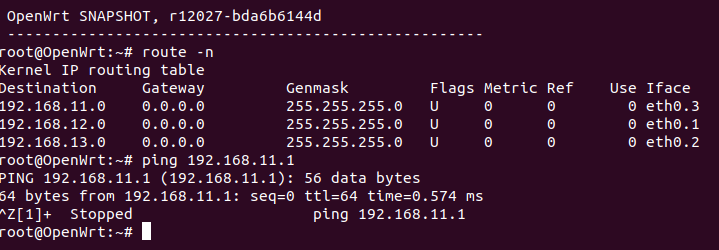
I updated it ,but no internet yet
root@OpenWrt:~# ping 192.168.11.1
PING 192.168.11.1 (192.168.11.1): 56 data bytes
64 bytes from 192.168.11.1: seq=0 ttl=64 time=0.621 ms
64 bytes from 192.168.11.1: seq=1 ttl=64 time=0.454 ms
^C
--- 192.168.11.1 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.454/0.537/0.621 ms
root@OpenWrt:~# ping www.linksys.com
ping: bad address 'www.linksys.com'
root@OpenWrt:~# uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd83:c41e:263f::/48'
config interface 'lan'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.12.1'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'xx:xx:1d:35:ff'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 3 4'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1 2'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 5'
option vid '3'
config interface 'lanb'
option ifname 'eth0.2'
option proto 'static'
option ipaddr '192.168.13.1'
option netmask '255.255.255.0'
config interface 'lanc'
option ifname 'eth0.3'
option proto 'static'
option ipaddr '192.168.11.2'
option netmask '255.255.255.0'
config route
option target '0.0.0.0'
option gateway '192.168.11.1'
option netmask '0.0.0.0'
option interface 'lanc'
trendy
June 9, 2020, 12:53pm
13
You also need to configure a DNS, in order to resolve names into IPs.
Could you tell where to make it ? and on main router or layer 3 switch?
trendy
June 9, 2020, 12:58pm
15
The main router is getting settings from DHCP, so it is not necessary.
it's working !!
trendy
June 9, 2020, 1:25pm
17
I am glad you got it working.How to mark a topic as [Solved] for a short how-to.
tmomas
June 19, 2020, 1:25pm
18
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.