my setup includes a working mwan3 - balancing or only_wan/only_wanb from lan to the outside is performing well.
for now, the wan interface with the higher metric is the default one, unplugging immediately makes use of wanb. By that I mean my port forwardings, services are reached via a public ip on wan, except on failover, then like I earlier told, wanb's public ip is the winner.
having a higher metric on interface wanb, leads as well to the redirects to the services.
At the moment, with working wan (default), I reach local webservers... and via wanb's public IP, my browser call is firewalled, timing out... My understanding of mwan3 is that with policies and rules each wan interface can be used for reaching services from lan machines, right?
I need help here, can someone describe how to set this up?


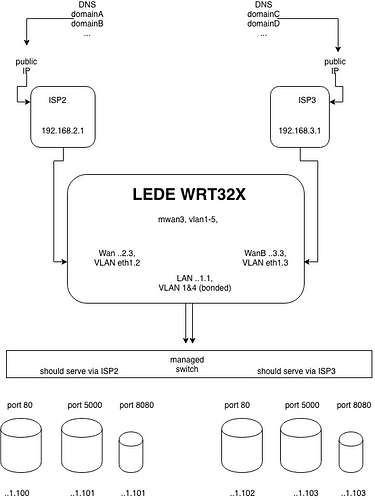
 although the first ones I did are like steady on wanb...
although the first ones I did are like steady on wanb...
