I'm running LEDE Reboot 17.01.0 r3205-59508e3 (release) on Archer C7 v2. My ISP supply IPv6 through 6rd tunnel.
TL;DR: ISP's 6rd IPv6 is assigned to LAN (br-lan), not WAN. There is not NAT with IPv6 and all devices are exposed to the Internet, so you need good IPv6 firewall rules (e.g. block IPv6 traffic originating from WAN going to LAN).
In the past I've tried to configure IPv6 without success and I gave up (everything was reset to DHCP).
Recently I noticed that I was getting an ISP's IPv6 on my router and all networks peripherals. I was expecting my WAN6 or WAN interface to get the ISP's IPv6 address, but it's the LAN interface that gets it. ![]()
Could that expose all my devices directly and insecurely to the Internet through IPv6, including IoT ? Did I seriously messed things up while experimenting back then ? Can someone confirm/explain/point me to the right documentation ?
I'm running SQM with cake/piece_of_cake, and I've created a Guest network for WLAN. When I go to https://www.whatismyip.com/, it shows my IPv6 address and http://test-ipv6.com/ reports that I have a working IPv6 setup using 6rd.
Here is a screenshot of my Luci interfaces:
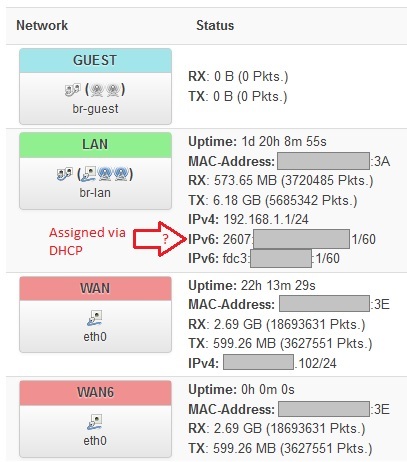
Here is "ifconfig" for relevant interfaces (note that 6rd-wan_6 is not a creation of mine so I assume it was auto-created):
6rd-wan_6 Link encap:IPv6-in-IPv4
inet6 addr: ::xxxx:xxxx/96 Scope:Compat
inet6 addr: 2607:xxxx:xxxx:xxxx::1/45 Scope:Global
UP RUNNING NOARP MTU:1280 Metric:1
br-lan Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:3A
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::xxxx:xxxx:xxxx:xxxx/64 Scope:Link
inet6 addr: 2607:xxxx:xxxx:xxxx::1/60 Scope:Global
inet6 addr: fdc3:xxxx:xxxx::1/60 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
(wan)
eth0 Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:3E
inet addr:xxx.xxx.xxx.102 Bcast:xxx.xxx.xxx.255 Mask:255.255.255.0
inet6 addr: fe80::xxxx:xxxx:xxxx:xxxx/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
(lan)
eth1 Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:3A
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
ifb4eth0 Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:73
inet6 addr: fe80::xx:xxx:xxxx:xxxx/64 Scope:Link
UP BROADCAST RUNNING NOARP MTU:1500 Metric:1