@lleachii yes its a good suggestion i will post about letsencrypt process
Then I would advise the user not to install SSL on LuCI (which is contrary to what the OP wants)! They should use VPN or SSH, as noted. Please stop trying to confuse OpenWrt users! Some are new and are easily confused by these antics.
Also, since you suggest a Public cert, please tell me what domain name you would register for a router?
OpenWrt.lan?
why are you not letting me help him out dude ??
you are not even understand what i am saying ?
i didnt see this ..lol
can you explain ? neither if these are safe dude . I think you are not taking me seriosly , Let me update my profile too , so that atleast you wont argue me on security dude
now plz let me complete the point when in securty atleast ??
LOL...Yes I understand:
- OP installs LuCI SSL package
- OP get cert err
- @arjuniet asks about Public cert chain
- @lleachii offers solution
SSH (using keys) , VPN remotely or a local management interface. The routers web service could be brute forced otherwise.
Rarely read them, I measure worth of people here by the number solutions a person collects.
really a solution ??? say by your heart ?
To the OP's issue, yes.
Or...Feel free to instruct him on setup of a VPN or SSH keys or a management VLAN (which assumes the OP is opening it on WAN, he didn't tell us that)!
Otherwise, stop hijacking topics!
good if you still thinks so .
dude try to understand , i am still trying to explain dont be in a habbit of bypassing ssl error in browsers , or one day you will be remembering me

I agree, I just think we could have waited for the OP to tell us if this is on WAN first.
BTW, before you proceeded on the security concerns you had, I was also going to tell the OP to note the serial number produced by the router cert before accepting it in a browser.
Also, most people address their router at 192.168.1.1, a cert won't work for that without accepting it, or using an invalid one.
yes all acceptable points and important too
Good Evening all,
I was not able to answer sooner (and I was not expecting so hard discussions on it)
So I am close to security as I am comnecting on LAN under wps2 wifi Keychain. Maybe i'm advanced n00b ^^
(ssh is active by fault, but I did nit understand yet fully the concept _ like a shared key that needs to be installed on the router and on the pc)
I also figure out the trick to access under https, but... It's a trick
Certificate is not seen as "official" and browser are not liking it and warning pushing and so on...
I'm just wondering if it is possible have "official certificate" or options to install this certificate in chrome (my favorite browser)
You could configure an SSH server on the router or a downstream PC to use keys, instead of username/password. I planned to suggest this if you were connecting to the router on the Internet via WAN.
Correct.
From: https://openwrt.org/docs/guide-user/luci/luci.secure
Of course, you can just buy a properly signed certificate for your own openwrt.lan domain and ip address to get rid of the annoying browser warning. You can also just import the self-signed root CA used for certificate creation to your browser certificate store.
If so, it would likely be here: chrome://settings/certificates?search=cert
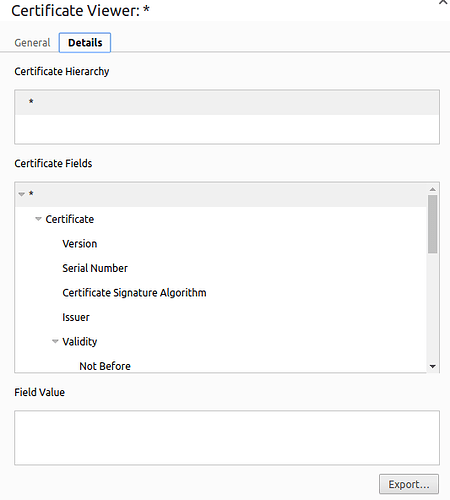
You will need to export the certificate:
- Click on the Not Secure button:
![]()
- Select "Certificate", you will then see the window below.
-
Export the file (OPEN AND NOTE THE SERIAL NUMBER)
-
Import at: chrome://settings/certificates?search=cert
Be advised, @arjuniet warns:
But since you: know the certificate, what device generated it, its serial number, etc. - this warning should be in the scope of your understanding to be safely ignored in your OpenWrt use case only.
In addition to the link above, also see:
https with or without a certificate does not stop anyone from loading pages from your server and doing brute force attacks or other methods of trying to hack in.
It's not intended to do that. uttpd / LuCI is not considered secure enough to be opened on the Internet, with or without https.
Thanks to all for the details.
@lleachii now, I better understand the certificate can not be signed / I'll install this specific one on my browser. And I'll still have warning on other devices.
@arjuniet I'll install this certificate on my browser and understand where this one is coming from (router create his own). But should not be done on unknown website
@mk24 my intention is not to access from internet only from intranet (connected to wifi or LAN), Thanks for warning and remind to the users
I really appreciate your help to understand the OpenWrt 
great . my concern was just this SSH , HTTPS both are serving same purpose. that is
-
HTTP (plain text) >>> ssl engine >>HTTPs
-
Telnet (plain text) >>> ssl engine >> SSH ( can be assumed)
The privacy that they provide to this communication is only worth when we as a client know that we are connecting to correct server that we wanted to , if we keep bypassing the warning than it means we are ready to believe any website saying that its twitter,com
thx
You're correlating two entirely different things:
- LAN connection to LuCI
- The reason for the error @mac_low is receiving is two-fold
- The SSL cert is self-signed
- The SSL cert is likely using an IP for CN, which should instead be placed in the SAN as
IP.1- The RFC has implied IPs/Hostnames should not be contained in the CN for ~2 decades, and Chrome distrusted all certs with the IP/hostname not stored in the SAN around a year or two ago.
- Unfortunately, I don't believe there's a way around this if utilizing the self-signed cert that's auto-created by
uhttpd, as it's not using an openssl.cnf to specify a SAN profile
- The reason for the error @mac_low is receiving is two-fold
- A WAN connection to a WAN hosted website
- In this case, if receiving any error regarding the SSL cert, the site should not be entered.
- In this case, if receiving any error regarding the SSL cert, the site should not be entered.
- The solution to 1.1 and/or 1.2 is to utilize the OpenSSL PKI wiki to create a self-signed CA and utilize that CA to sign a new cert for
uhttpd.
All,
I tried to refrain. Please try to stop playing into the chicken-or-the-egg theories.
- A person gets a router
- Installs Official firmware
- The person manages to get Internet
- The person installs an SSL package
- Someone suggests a Public cert
- The person now doesn't trust his/her own router.
At some point, there's a "root of trust..." Your router is this root (as its configurations are concerned, and the console you trusted to configure it)...otherwise, make a local [wired] management interface; and block port 80 and 22 to all other networks.
Actually, you miss-assumed, the traffic would not be telnet, it would be 80(or 443)/tcp SSH tunneled.
dude stop this now .
it was an analogy telnet is not preferred for remote method of shell access because its plain text exchange all visible if you just tap the communication media ? agree ?
ssh is prefered ? because it gives you an encrypted session .. that is data exchane happends only after a session with an encryption key is established ? agree ?
bydefault this is the ssh implementation . during first time communicaction when you enter command on your terminal
ssh lleachii@myserver.in
and on prompt you give password . and you are hacked dude ? i thing you know why
password based vs key based
In ssh either you do key based authentication or password based it equally safe or equally vulnerable ( this is for you @lleachii)
It just an analogy like authentication is check ether by checking by something you have or by something you know
and even in VPN i dont know why you feel secure ? explain plz
HTTPS or SSH
In present scenario if you keep you eyes open its only HTTPS that can save you how ?
TLS on its default implementation get implemented by server authentication ? how ?
if you are not in a habbit of bypassing ssl invalid CA error your cliet ( you browser) is giving you warning that i dont think you are getting connected to abc.com ? why it warns ?
because site abc.com is sending a non trusted CA signed certificate ( which is the proof of it being a genuine server on which abc.com is hosted ) bypassing it is inviting a attack on yourself
are you even aware of how may routers have generated the same private key at present ?
If you are use crypo method for trying to make your communication safe i admit the privacy is importation which we all can achieve with default ssh as well as self-signed certificate bypass trick is giving you
but ask your self what are you missing . do you guarantee tthe server authenticity ? are you really having a private encrypted communication with the real server ? NO you can never
that is why trusted CA certificate comes in scene
I even saw you saying that you will suggest to check the certificate serial key . LOL you should know any cerificate number can be choosed
- Did understand the previous post, given user is on LAN (needing an RFC-invalid cert for an IP)?
- Did not understand the previous post, given user is on LAN (needing an RFC-invalid cert for an IP)?
I did.
- Please edit ALL the OpenWrt Wikis that thus suggest you should accept the cert.
I hope the best in your endeavours.