hello, I have an l2tp server on RouterOS, and an SMT+ router connected to the server, the problem is I cant see the smt+ lan from the server, routes are ok, have other mikrotiks connetcted to the server with the same routes, no troubles with them. smt+ firewall is default, Ive tried to allow and accept everything, made nat rules, no use. ive figured out the problem is with firewall, but have no idea what to do, help me please
So what openwrt release and device are you using exactly?
smartbox turbo +
22.03.0 stable
the router should be similar to Netgear R6220
Now we'll need all your customized configs (make sure you redact mac public ips/domains and certs/ passwd)
sorry Ive no idea how to extract that
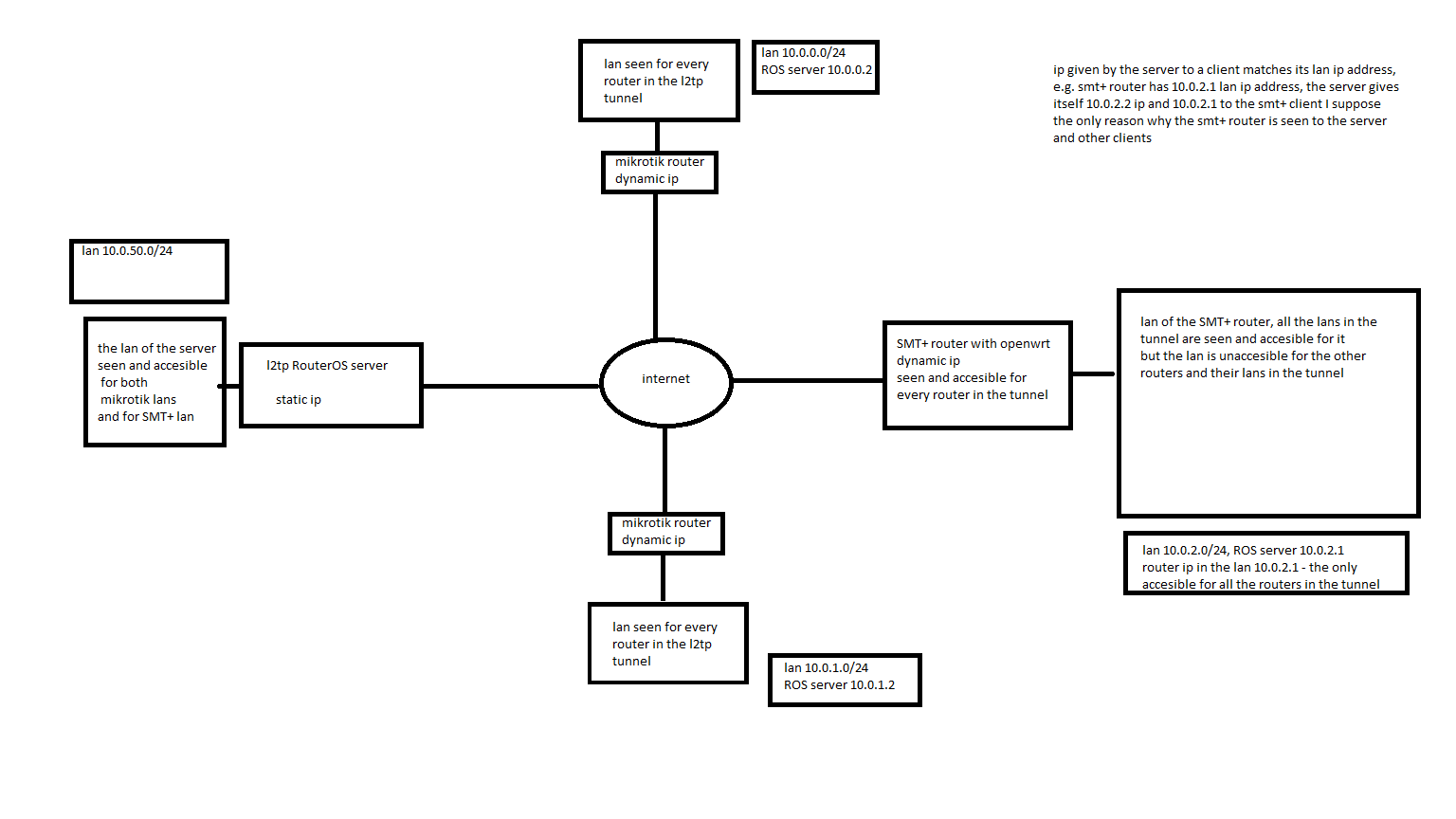
my RouterOS server has 10.0.50.0/24 network and 10.0.50.1 ip, it gives local 10.0.2.2 and remote 10.0.2.1 ip to the client, ive added 10.0.2.0/24 10.0.2.1 route
i can make only ROS cli config in text, openwrt doesnt seem to have such option
the smartbox turbo+ device on openwrt config is
wan: via dchp, dynamic ISP ip
lan: 10.0.2.0/24 network and 10.0.2.1 router ip
the l2tp tunnel 10.0.2.1(that ROS gives to)
and a route set by me 10.0.0.0/16 10.0.2.2 gateway, interface: the l2tp tunnel
firewall config:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wwan'
list network 'white_ip'
option input 'ACCEPT' #the only change I made. ive set this accepted for the router to be accesible from the ROS server, what should i do to make the hole lan interface 10.0.2.0/24 to be accesible from the server and its lan?
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option fw4_compatible '1'
option path '/etc/firewall.user'
sorry for the late reply
if you need any config else please let me know ill try to do this
cat /etc/config/network
make sure you redact private stuff like MAC and public ip
Network config:
root@SBT:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option delegate '0'
option device 'br0'
option ipaddr '10.0.2.1'
config interface 'wan'
option proto 'dhcp'
option metric '5'
option delegate '0'
option device 'wan'
config globals 'globals'
option packet_steering '1'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'wwan0'
option ipv6 '0'
option multicast '0'
config device
option name 'lan1'
option ipv6 '0'
config device
option name 'lan2'
option ipv6 '0'
config device
option name 'lan3'
option ipv6 '0'
config device
option name 'lan4'
option ipv6 '0'
config device
option name 'wan'
option ipv6 '0'
config device
option name 'br0'
option type 'bridge'
option ipv6 '0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'wlan0'
option ipv6 '0'
config device
option name 'wlan1'
option ipv6 '0'
config interface 'white_ip'
option proto 'l2tp'
option server '1.2.3.4'
option username 'name'
option password 'pass'
option defaultroute '0'
option peerdns '0'
option ipv6 '0'
option delegate '0'
option force_link '1'
option mtu '1400'
option checkup_interval '10'
option keepalive '20 5'
config route
option interface 'white_ip'
option target '10.0.0.0/16'
option gateway '10.0.2.2'
I see nothing out of the ordenering.
Does it work from a different device like let's say your pc?
no, but it works well on a mikrotik router connected to the server, with the same config with no tuned firewall I see all the clients at the lan. I dont know why it doest work on OW either, maybe I should wait for the final release, theyll be fixing some bugs, ive heard of the new firewall v4. havent tried on OW 19.07.10 yet
Can we get some logs when the failure occurs?
logread | grep ppp or
logread | grep l2tp
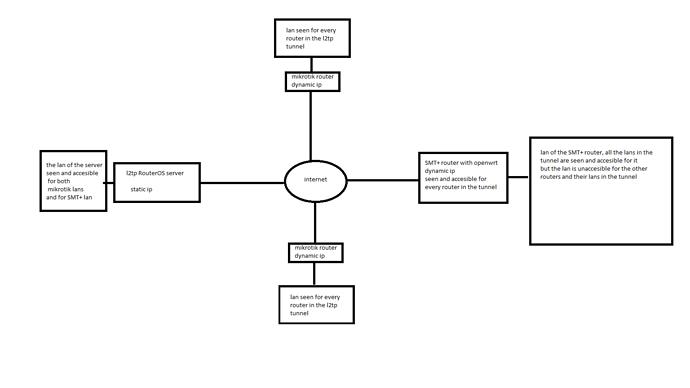
sorry i think i was wierd in my explanation, ive made a picture to make it clear. I think there's no failure.
though the commands didnt work, no log in cli
To have the openwrt lan accesible for the other vpn endpoint you need to move l2tp net device from wan to lan (firewall zone)
ive just mooved it, no result unfortunatelly
yes indeed you should have created a dedicated zone:
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'white_ip'
option input 'ACCEPT'
then restart firewall (or device)
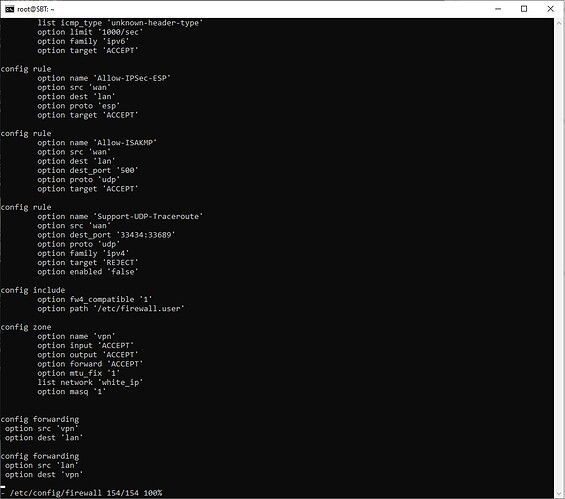
didnt help. firewall config at the moment:
root@SBT:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'white_ip'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'REJECT'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option fw4_compatible '1'
option path '/etc/firewall.user'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'white_ip'
You also need a:
config forwarding
option src 'vpn'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'vpn'
I tried to edit it in vi, once I restart firewall this pops up
root@SBT:~# /etc/init.d/firewall restart
ubus rule (ubus:igmpproxy[instance1] rule 0) option 'src' specifies invalid value 'wan'
ubus rule (ubus:igmpproxy[instance1] rule 0) skipped due to invalid options
ubus rule (ubus:igmpproxy[instance1] rule 1) option 'src' specifies invalid value 'wan'
ubus rule (ubus:igmpproxy[instance1] rule 1) skipped due to invalid options
ubus rule (ubus:igmpproxy[instance1] rule 2) option 'src' specifies invalid value 'wan'
ubus rule (ubus:igmpproxy[instance1] rule 2) skipped due to invalid options
ubus rule (ubus:igmpproxy[instance1] rule 3) option 'src' specifies invalid value 'lan'
ubus rule (ubus:igmpproxy[instance1] rule 3) skipped due to invalid options
then I tried to edit it with echo, got this
doesnt work either, I dont know whats wrong
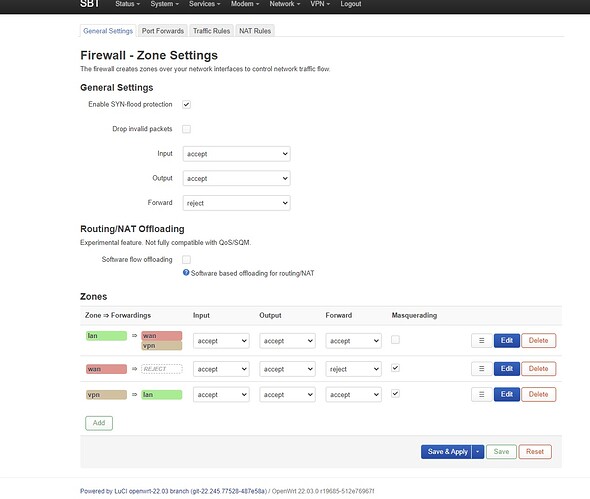
You could try doing it from luci if it's installed