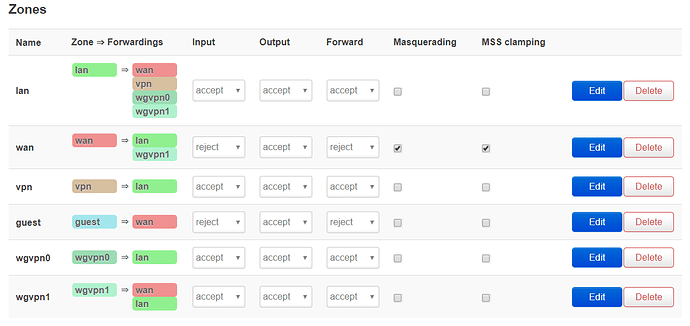
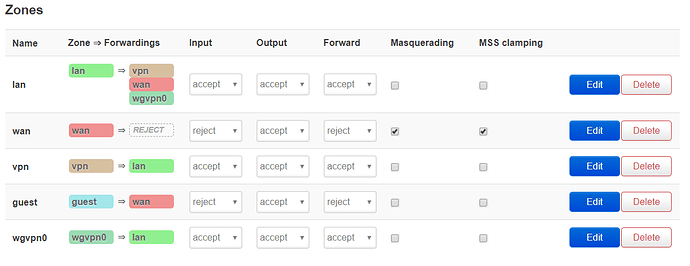
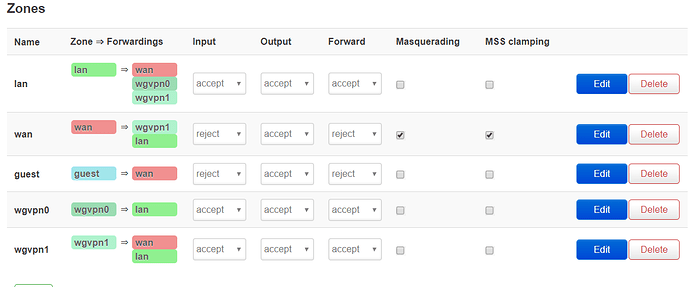
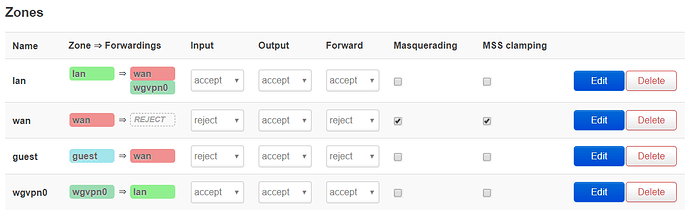
Dear OpenWRT-Community,
i want to connect two networks through a wireguard site2site tunnel.
Its pretty easy to get the tunnel up and running between the two openwrt peers. I can ping the router to router interfaces from each other site consistently.
My problem relies probably within routing or firewalling since my clients are not able to reach hosts from the other lan from the other site properly.
General
Router 1 has a static IPv4 Adress (it is acting as a "server"-Peer)
LAN1: 192.168.1.0/24 --> with several clients and servers
Router 2 has an LTE/4G connection without a static adress
LAN2: 192.168.5.0/24 --> with several clients and servers
- Both sides should remain using their own local WAN connection for the internet.
- Clients/Servers from both sites should reach the other site.
WGVPN0 is for the Wireguard Tunnel as 10.200.100.0/24:
--> Router 1: 10.200.100.1/32
--> Router 2: 10.200.100.2/32
Configuration
Here is my configuration:
Router 1:
OpenWrt 18.06.4, r7808-ef686b7292
/etc/config/network:
config interface 'wgvpn0'
option proto 'wireguard'
option private_key 'someprivatekey'
option listen_port '23498'
list addresses '10.200.100.1/24'
config wireguard_wgvpn0
option public_key 'somepublickey'
option route_allowed_ips '1'
option persistent_keepalive '25'
option description 'wgvpn0_client1'
option preshared_key 'somepresharedkey'
list allowed_ips '10.200.100.2/32'
list allowed_ips '192.168.5.0/24'
# list allowed_ips '0.0.0.0/0'
/etc/config/firewall:
config rule
option target 'ACCEPT'
option proto 'udp'
option dest_port '23498'
option name 'Allow-Wireguard-Site2Site Inbound'
option src 'wan'
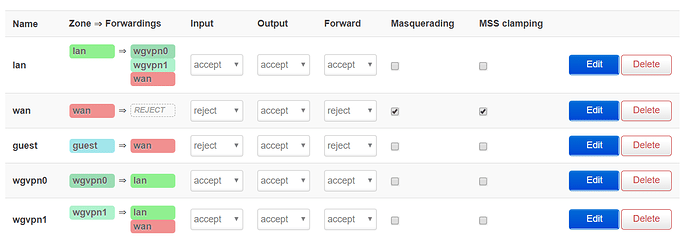
config zone 'wgvpn0'
option name 'wgvpn0'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'wgvpn0'
option dest 'lan'
config forwarding
option dest 'wgvpn0'
option src 'lan'
route output:
- dont mind about those 10.200.200.0/24 Routes... they are for a already working roadwarrior-wireguard vpn configuration --> different interface wgvpn1
- 192.168.99.0 is just a guest wifi with limited access
charlie@router1:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 213.143.120.1 0.0.0.0 UG 0 0 0 eth1
10.200.100.0 * 255.255.255.0 U 0 0 0 wgvpn0
10.200.100.2 * 255.255.255.255 UH 0 0 0 wgvpn0
10.200.200.0 * 255.255.255.0 U 0 0 0 wgvpn1
10.200.200.2 * 255.255.255.255 UH 0 0 0 wgvpn1
10.200.200.3 * 255.255.255.255 UH 0 0 0 wgvpn1
10.200.200.4 * 255.255.255.255 UH 0 0 0 wgvpn1
10.200.200.5 * 255.255.255.255 UH 0 0 0 wgvpn1
10.200.200.6 * 255.255.255.255 UH 0 0 0 wgvpn1
10.200.200.7 * 255.255.255.255 UH 0 0 0 wgvpn1
192.168.1.0 * 255.255.255.0 U 0 0 0 br-lan
192.168.5.0 * 255.255.255.0 U 0 0 0 wgvpn0
192.168.99.0 * 255.255.255.0 U 0 0 0 br-guest
213.143.120.0 * 255.255.255.0 U 0 0 0 eth1
Router 2:
OpenWrt 18.06.4, r7808-ef686b7292
/etc/config/network:
config interface 'wgvpn0'
option proto 'wireguard'
option private_key 'someprivatekey'
option listen_port '23498'
list addresses '10.200.100.2/24'
config wireguard_wgvpn0
option public_key 'somepublickey'
option persistent_keepalive '25'
option description 'wgvpn0_client1'
option preshared_key 'somepresharedkey'
option endpoint_host 'someworkingdomainname.com'
option endpoint_port '23498'
list allowed_ips '192.168.1.0/24'
list allowed_ips '10.200.100.1/32'
# list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
/etc/config/firewall:
config zone
option name 'wgvpn0'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'wgvpn0'
config forwarding
option dest 'wgvpn0'
option src 'lan'
config forwarding
option dest 'lan'
option src 'wgvpn0'
route output
charlie@router2:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 10.181.15.97 0.0.0.0 UG 0 0 0 wwan0
10.181.15.96 * 255.255.255.240 U 0 0 0 wwan0
10.200.100.0 * 255.255.255.0 U 0 0 0 wgvpn0
10.200.100.1 * 255.255.255.255 UH 0 0 0 wgvpn0
192.168.1.0 * 255.255.255.0 U 0 0 0 wgvpn0
192.168.5.0 * 255.255.255.0 U 0 0 0 br-lan
192.168.99.0 * 255.255.255.0 U 0 0 0 wlan1-1
213.143.120.58 10.181.15.97 255.255.255.255 UGH 0 0 0 wwan0
Troubleshooting - Wireguard Interfaces
charlie@router1:~# ping 10.200.100.2
PING 10.200.100.2 (10.200.100.2): 56 data bytes
64 bytes from 10.200.100.2: seq=0 ttl=64 time=26.743 ms
64 bytes from 10.200.100.2: seq=1 ttl=64 time=30.739 ms
64 bytes from 10.200.100.2: seq=2 ttl=64 time=30.442 ms
64 bytes from 10.200.100.2: seq=3 ttl=64 time=25.352 ms
64 bytes from 10.200.100.2: seq=4 ttl=64 time=30.231 ms
charlie@router2:~# ping 10.200.100.1
PING 10.200.100.1 (10.200.100.1): 56 data bytes
64 bytes from 10.200.100.1: seq=0 ttl=64 time=46.519 ms
64 bytes from 10.200.100.1: seq=1 ttl=64 time=30.362 ms
64 bytes from 10.200.100.1: seq=2 ttl=64 time=31.351 ms
64 bytes from 10.200.100.1: seq=3 ttl=64 time=31.233 ms
64 bytes from 10.200.100.1: seq=4 ttl=64 time=30.181 ms
seem to be okay
Troubleshooting - Try to ping servers on the other site from routers
charlie@router1:~# ping server.lan2
PING server.lan2 (192.168.5.168): 56 data bytes
64 bytes from 192.168.5.168: seq=0 ttl=63 time=27.279 ms
64 bytes from 192.168.5.168: seq=1 ttl=63 time=30.863 ms
64 bytes from 192.168.5.168: seq=2 ttl=63 time=24.775 ms
64 bytes from 192.168.5.168: seq=3 ttl=63 time=30.655 ms
--> Router 1 can reach a server from the remote LAN2!
charlie@router2:~# ping server.lan1
PING server.lan1 (192.168.1.43): 56 data bytes
^C
--- server.lan1 ping statistics ---
181 packets transmitted, 0 packets received, 100% packet loss
--> Router 2 cannot reach a server from the remote LAN1!
Troubleshooting - lets test from the servers:
Pinging another server:
charlie@server.lan1:~$ ping server.lan2
PING server.lan2 (192.168.5.168) 56(84) bytes of data.
From router.lan1 (192.168.1.1) icmp_seq=3 Destination Port Unreachable
From router.lan1 (192.168.1.1) icmp_seq=6 Destination Port Unreachable
From router.lan1 (192.168.1.1) icmp_seq=11 Destination Port Unreachable
From router.lan1 (192.168.1.1) icmp_seq=15 Destination Port Unreachable
From router.lan1 (192.168.1.1) icmp_seq=16 Destination Port Unreachable
^C
--- openhabianpi.lan2 ping statistics ---
16 packets transmitted, 0 received, +5 errors, 100% packet loss, time 15329ms
--> Server from the LAN1 cannot reach a server from the LAN2!
charlie@server.lan2:~$ ping server.lan1
PING server.lan1 (192.168.1.43) 56(84) bytes of data.
From 10.200.100.1 icmp_seq=1 Destination Port Unreachable
From 10.200.100.1 icmp_seq=2 Destination Port Unreachable
From 10.200.100.1 icmp_seq=3 Destination Port Unreachable
From 10.200.100.1 icmp_seq=4 Destination Port Unreachable
--> Server from the LAN2 cannot reach a server from the LAN1!
Ping the other router from server:
charlie@server.lan1:~$ ping 192.158.5.1
PING 192.158.5.1 (192.158.5.1) 56(84) bytes of data.
^C
--- 192.158.5.1 ping statistics ---
30 packets transmitted, 0 received, 100% packet loss, time 29644ms
--> Server from the LAN1 cannot reach the remote router on the LAN2 interface!
charlie@server.lan2:~$ ping 192.168.1.1
PING 192.168.1.1 (192.168.1.1) 56(84) bytes of data.
64 bytes from 192.168.1.1: icmp_seq=1 ttl=63 time=34.3 ms
64 bytes from 192.168.1.1: icmp_seq=2 ttl=63 time=32.8 ms
64 bytes from 192.168.1.1: icmp_seq=3 ttl=63 time=31.9 ms
64 bytes from 192.168.1.1: icmp_seq=4 ttl=63 time=25.5 ms
--> Server from the LAN2 can reach the remote router on the LAN1 interface!
What did i try?
- I changed the allowed_ips to '0.0.0.0/0' and disabled the creation of routes like:
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '0'
Additionally i manually set the routes acordingly:
on router 1:
ip route add 192.168.5.0/24 via 10.200.100.2 dev wgvpn0
on router 2:
ip route add 192.168.1.0/24 via 10.200.100.1 dev wgvpn0
--> I got the exact same results as i've shown you already
Deductions
- The tunnel itself is working
- Server/Client-Hosts cannot reach Servers/Clients from the other LAN
- Server from the LAN1 cannot reach the remote router on the LAN2 interface!
- Server from the LAN2 can reach the remote router on the LAN interface!
- Router 1 is able to reach Servers/Clients from LAN2
- Router 2 is not able to reach Servers/Clients from LAN1
I cannot seem to find the error in my configuration. The circumstances especially deduction 4 and 5 confuse me more than that they help on finding the solution.
I really would appreciate it if there is somebody out there that can relieve me from my misery!
i already would like to thank you in advance for keep reading till the and and assisting me with this!
best wishes
satheras