You do that on the main router. But all that that has done is create a new network for guests that is independently routed to the Internet and can be accessed by wifi on the main router.
To extend your guest network to another AP via Ethernet, you would make the "guest" network a bridge so you can add more interfaces to it. Specifically you're going to add an Ethernet VLAN that feeds the other router (the AP). Go to the guest network edit page and on physical settings check the box for bridge. Note that the radio buttons where you attach the network to one device (the local WiFi AP) change to check boxes where you can attach to more than one device. You will be coming back to this later.
How to make Ethernet VLANs depends on the hardware you have. Unless the port is dedicated to one Ethernet cable (typically the "WAN" port on a 10/100 router), you need to set up both the CPU Ethernet port and the switch.
First, be logged into your main router on its wifi. This will have you stay connected and able to fix it if you mis-configure the Ethernet ports. On the main router you're almost certainly going to be working through a switch since the WAN port is connected to your cable or DSL modem.
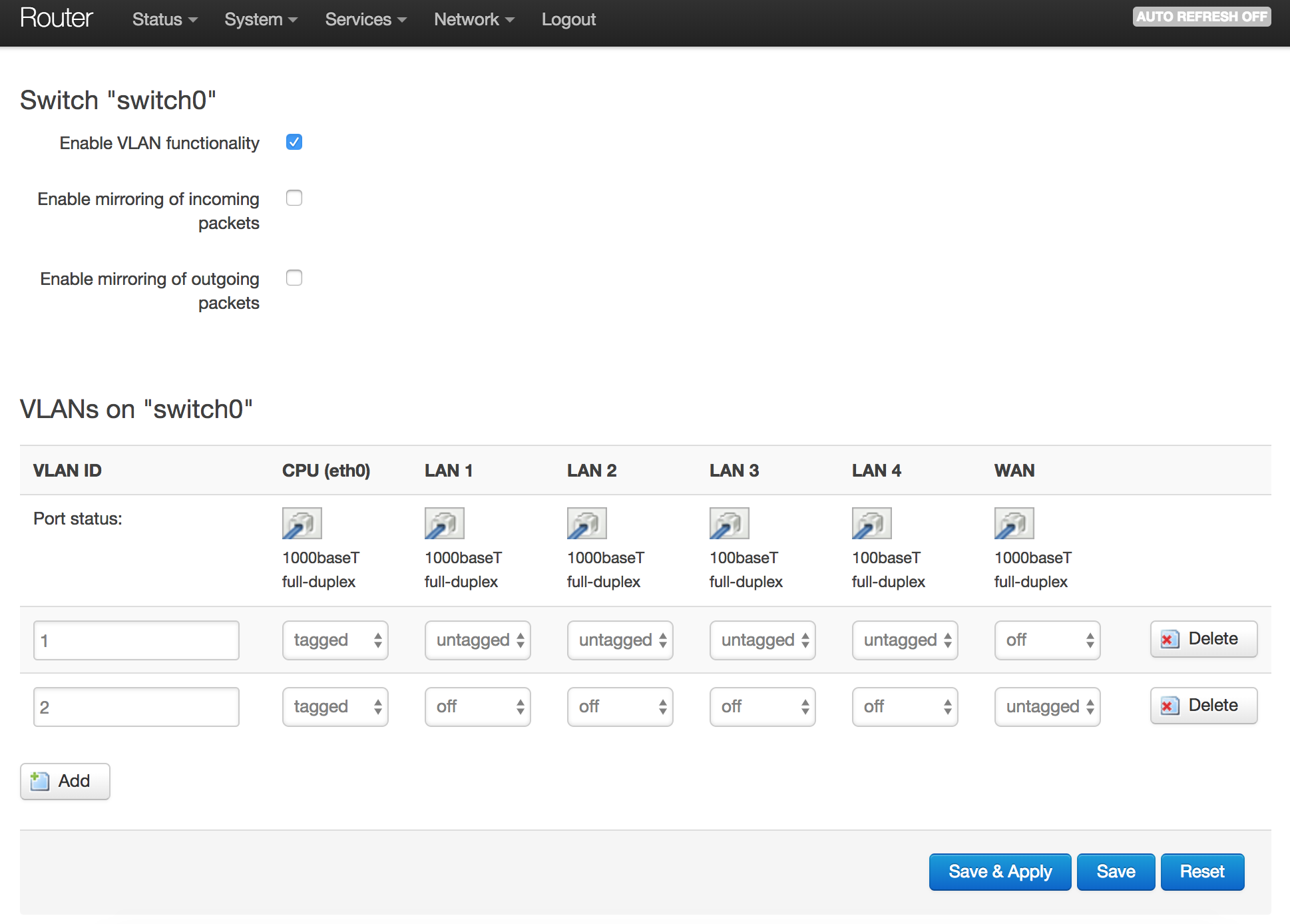
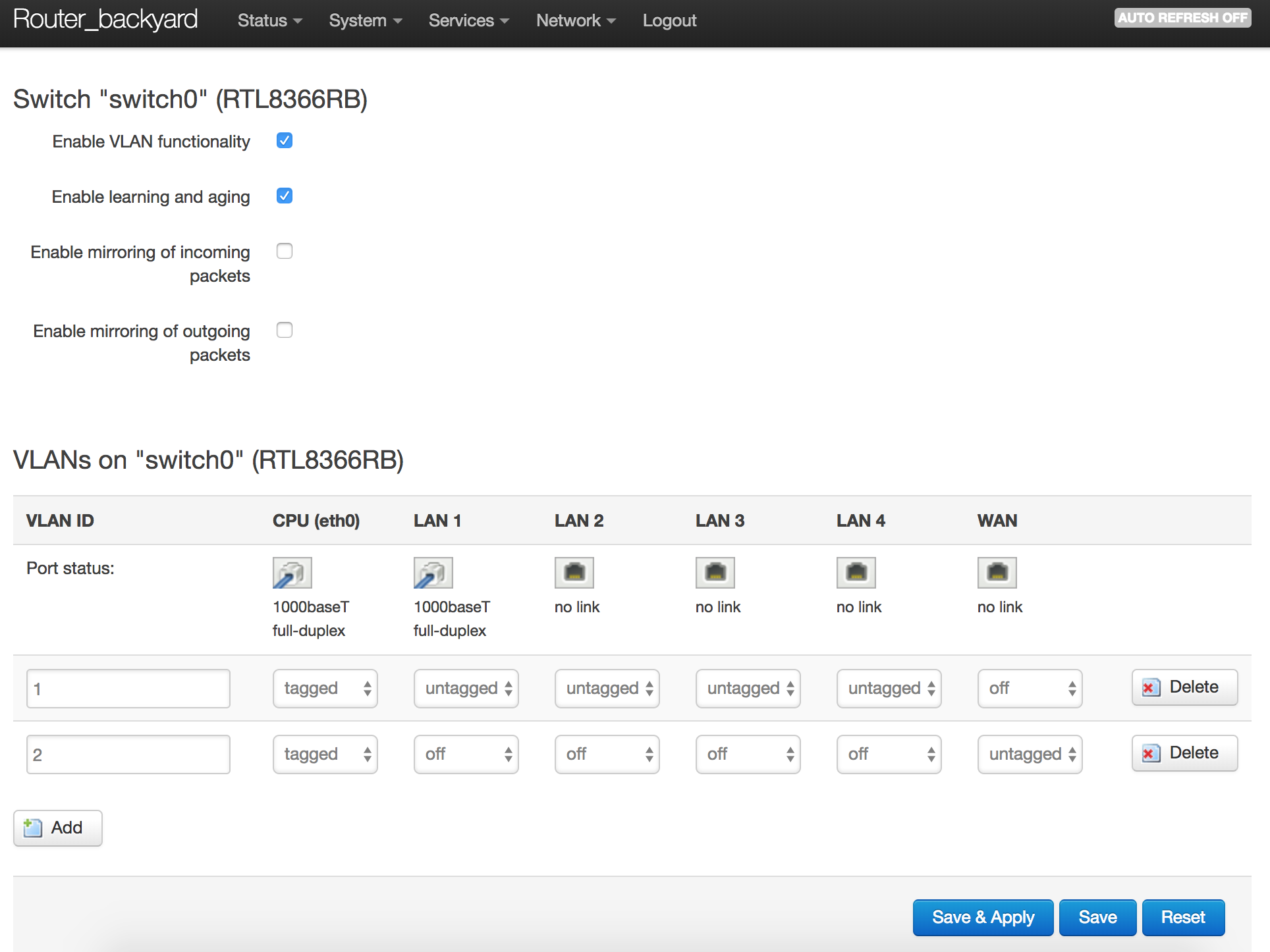
On the "Network:switch" page, find the Ethernet port that is connected to the cable between the two routers. The numbering doesn't always correspond to the label on the outside of the router, so plug and unplug the cable and notice which one goes from connected to disconnected.
Make a new VLAN with the "add" button. In both the CPU and the link cable, set "tagged" on both VLANs. The other ports remain "untagged" in only the LAN VLAN, so that ordinary LAN devices like a printer can be connected.
If the default configuration of the router had everything untagged, you need to go to LAN interface edit, physical settings and change from e.g. eth0 to eth0.1, assuming the LAN VLAN is number 1 in the switch. If the LAN was already tagged in the CPU, skip this step, your LAN should continue to work without changing anything.
Usually the new "guest" VLAN is number 2, so go back to the guest interface physical settings and click the eth0.2 or eth1.2 or whatever the guest VLAN is.
You now should have two VLANs live on the interconnect port. So time to go to the remote AP. You will need to temporarily connect the interconnect cable to an untagged LAN port on the main router to have access, since the AP does not understand VLANs yet.
Presuming this is set up as a dumb AP with only a LAN connection, first you need to change the LAN to be tagged instead of untagged. Set up a VLAN through the switch and change the physical settings of the AP's LAN to be this tagged interface. This VLAN of course has to have the same number as the LAN one on the main router. You can now (actually you have to now) connect the interconnect cable to the tagged port on the main router, and the LAN should work as before.
Now to hook up the guests at the AP. On the AP, create a new interface called guest with protocol Unmanaged. The guests are going to be completely dumbly switched through the AP from wifi to Ethernet without the AP's CPU even looking at what they do. All the routing and firewalling of guests is done by the main router. Make it a bridge. Make a VLAN through the switch and connect that ethernet port to the guest bridge. Make a second wifi AP and connect it to the guest bridge.
If your dumb AP is a router with a dedicated CPU Ethernet to the WAN port, you don't need to set up its switch, you can just use eth0.1 and eth0.2 directly and plug the interconnect cable into the WAN port.