hey, maybe you can help to get this setup working, I'm trying to use Cyberghost VPN as a client via OpenVPN on a LEDE router.
The VPN setup seemed to work, but as soon as i launch the openvpn daemon and the tunnel is established, i can't ping any external IPs anymore. If i shut down openvpn i can connect to WAN IPs just fine. What might be the reason? Let me know what info might be helpful.
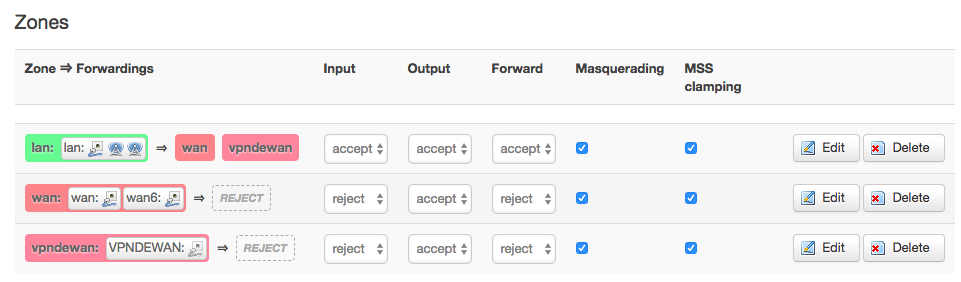
Do you have forwarding setup for lan > vpn? This would be in the firewall config.
Hey psherman, that is what i set up in firewall config:
how does this look ?
Looks okay from forwarding perspective (at least what is visible). But you should turn off masquerading and mss clamping on all but the wan interface.
ok I changed that, but it doesn't allow me to connect through the VPN still.
In the Syslog i found this entry:
is that maybe key to why no WAN connection can be made when VPN is up ?
Im not sure what other information might be of use.
Post your config filed for network, dhcp, openvpn, and firewall. You can ssh into the router and find them in /etc/config
here we go, that's the config. i wonder if this might reveal why when starting openvpn WAN connection is lost!
dhcp
option proto 'dhcp'
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
.
network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdba:9fcf:fd6c::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0 1 2 3t 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '3t 4t'
option vid '100'
config interface 'VPNDEWAN'
option _orig_ifname 'tun0'
option _orig_bridge 'false'
option proto 'none'
option auto '1'
option ifname 'tun0'
config route
.
firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option input 'REJECT'
option network 'VPNDEWAN'
option output 'ACCEPT'
option name 'vpndewan'
option forward 'REJECT'
config forwarding
option dest 'wan'
option src 'lan'
config forwarding
option dest 'vpndewan'
option src 'lan'
.
openvpn
config openvpn 'cyberghost_de'
option dh 'dh1024.pem'
option float '1'
option client '1'
option comp_lzo 'yes'
option reneg_sec '0'
option persist_key '1'
option nobind '1'
option remote_cert_tls 'server'
option key '/etc/luci-uploads/cbid.openvpn.cyberghost_de.key'
list remote '1-de.cg-dialup.net'
option enabled '1'
option ca '/etc/luci-uploads/cbid.openvpn.cyberghost_de.ca'
option cert '/etc/luci-uploads/cbid.openvpn.cyberghost_de.cert'
option port '443'
option proto 'udp'
option dev 'tun'
option cipher 'AES-256-CBC'
option auth_user_pass '/etc/openvpn/userpass.txt'
option auth 'SHA256'
option tls_client '1'
option verb '1'
option redirect_gateway 'def1'
mk24
November 25, 2017, 8:17pm
8
Check your route table (Status-->Routes or route command) to be sure that the default route is through the VPN. I don't think you should forward from lan to wan at all when you want all Internet use (except router to VPN server of course) to go through the VPN.
hey mk24,
thats mey routes table (when connected to VPN and thus 'deconnected')
Active IPv4-Routes
i'm not sure what i can see from this, and how this could be changed
Hi, 've U done with it ?