"Works for me", at least on the 5 GHz radio, in recent builds (April and later) off master and should be working on openwrt-18.06
Hmm. Tried the latest 18.06 snapshot. Had no luck. I needed to disable the AP before I got a working mesh. This was with wpad-mesh.
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:01/0000:01:00.0'
option htmode 'VHT80'
option disabled '0'
#config wifi-iface 'default_radio0'
# option device 'radio0'
# option network 'lan'
# option mode 'ap'
# option ssid 'OpenWrt'
# option encryption 'none'
config wifi-iface 'mesh'
option device 'radio0'
option ifname 'wlan0-1'
option mode 'mesh'
option mesh_id 'mymesh'
option encryption 'none'
option network 'lan'
# option mesh_fwding '1'
option disabled '0'
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/qca955x_wmac'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
This is the only way mesh works for me.
Sorry for a double post but I managed to fix the issue. I'll just document it, in case anybody else has problems.
config wifi-iface 'default_radio0'
option device 'radio0'
option ifname 'wlan0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
I needed to add an ifname for the AP config.
The thread subject is "authenticated" mesh -- how is it "authenticated"?
Because the following works quite well, once you've got your mesh stations and APs straightened out without encryption
config wifi-iface 'mesh0'
option device 'radio5'
option ifname 'mesh0'
option mode 'mesh'
option mesh_id '<your mesh ID here>'
option mesh_fwding '1'
option encryption 'psk2+ccmp'
option key '<your key here>'
option sae_password '<your key here>'
This is running config, and the presence of both key and sae_password is due to numerous changes in the OpenWRT code which had it flip-flopping between which of the two worked at any moment.
Yeah. Sorry. Just confirming that I did what jeff said above, putting encryption afterwards presented no issues.
I've set up a working 802.11s mesh on single band routers running OpenWrt 18.06.1, but have yet to secure it. My current configuration is as follows:
/etc/config/network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '<redacted>'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.0.2'
option netmask '255.255.255.0'
option gateway '192.168.0.1'
list dns '200.12.232.4'
list dns '200.12.229.1'
list dns '8.8.8.8'
option ip6assign '60'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '<redacted>'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_dev'
option name 'eth0.2'
option macaddr '<redacted>'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
/etc/config/wireless:
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11g'
option path 'platform/10300000.wmac'
option htmode 'HT20'
option disabled '0'
option legacy_rates '1'
option channel '1'
config wifi-iface
option device 'radio0'
option ifname 'wlan0'
option network 'lan'
option mode 'ap'
option ssid '<redacted>'
option encryption 'psk2+ccmp'
option key '<redacted>'
config wifi-iface
option device 'radio0'
option ifname 'mesh0'
option network 'lan'
option mode 'mesh'
option mesh_id '<redacted>'
option mesh_fwding '1'
Both wifi interfaces (wlan0 in AP mode and mesh0 in mesh mode) are on the same radio0 device.
Previous attempts at adding @jeff's suggested encryption options
option encryption 'psk2+ccmp'
option key '<your key here>'
option sae_password '<your key here>'
to the mesh0 interface have rendered wlan0 inaccesible.
I'll document my attempts to get encryption to work on both interfaces in this thread.
First trial after adding @jeff's suggested encryption options:
- the mesh comes up: I can see the other two non-wired meshed routers on the wired, meshed router's luci interface.
- from a station associated to the wired, meshed router I can't ping the other two non-wired meshed routers.
- I can't ping the other two non-wired meshed routers from the wired meshed router.
- stations that associate to the non-wired meshed routers can't access the Internet through the wired, meshed router.
Since I can't ping the non-wired meshed routers from stations or from the wired meshed router, I assume IP packets aren't being routed through the mesh. But I could when the mesh was unencrypted.
I'll appreciate hints and tips.
@oavaldezi just note if you are using a Mediatek Wifi Chipset these cant run AP and Mesh at the same time,
Disable your 'ap' section and see if the mesh devices can ping each other
Thank you for your comment, which is unfortunate news to me. Is this fact documented?
There are limitations on chipsets/firmware/drivers that can limit or prevent use of mesh. I haven't found any up-to-date information about what is and is not supported. iw list will show you the available combinations, here from an Archer C7
[...]
Supported interface modes:
* managed
* AP
* AP/VLAN
* monitor
* mesh point
[...]
valid interface combinations:
* #{ AP, mesh point } <= 8, #{ managed } <= 1,
total <= 8, #channels <= 1, STA/AP BI must match, radar detect widths: { 20 MHz (no HT), 20 MHz, 40 MHz, 80 MHz }
"managed" is, as I understand it, "client-mode"
The output of iw dev <mesh dev> station dump will show connectivity status.
On the routing, 802.11s routing only supports mesh clients themselves. It does not route or bridge traffic from "off-mesh" nodes transparently. As most client devices aren't mesh nodes, but are connected through "hybrid nodes", explicit routing or bridging is required. This is likely why mesh nodes can "see" each other, but off-mesh nodes don't have connectivity.
Static routing is the "simplest" to accomplish, but does not "play well" with roaming from AP to AP. Basically each AP gets its own subnet and supplies DHCP. All of the hybrid nodes need static routes for each of the "remote" subnets.
If you wish to bridge the segments of a single subnet, then you need to supply something other than just 802.11s routing. There are several approaches, each with its own set of advantages and disadvantages.
Static GRE bridging can be set up with the tunnel end points being the mesh addresses. 802.11s will find the "best route" from one mesh end point to another. This is very functional, but complexity grows as the product of the number of end points and number of gateways. It has the disadvantages that both ends of each tunnel need configuration to know about their peers. I have used this and it functions well. It was the administration complexity that had me explore other approaches.
B.A.T.M.A.N. replacing 802.11s routing is another option. It will accommodate connections between both nodes that have mesh connectivity, as well as those bridged to them. https://openwrt.org/docs/guide-user/network/wifi/mesh/batman
There are other routing protocols that can be used as well, such as OLSR.
I cant find it specifically documented
I found it out the hard way
Only my Atheros/Qualcom devices can reliably mesh and ap at same time
you will notice as @jeff has posted the output differ from wifi chipset to wifi chipset for
iw phy phy0 info
iw phy phy1 info
Here is an example of such a encrypted OLSR mesh i setup for testing/evaluation
Im connected to the mesh from my pc via wifi to the GL-iNet 6416A v1 (which is connected to the internet) (Device has LAN and WAN Port)
Device
10.0.71.5
FriendlyARM NanoPi NEO (512mb Ram, 2Gb sdcard, quad-core arm, 100Mbps Lan)
RT3070 USB Wifi Dongle
Only Mesh
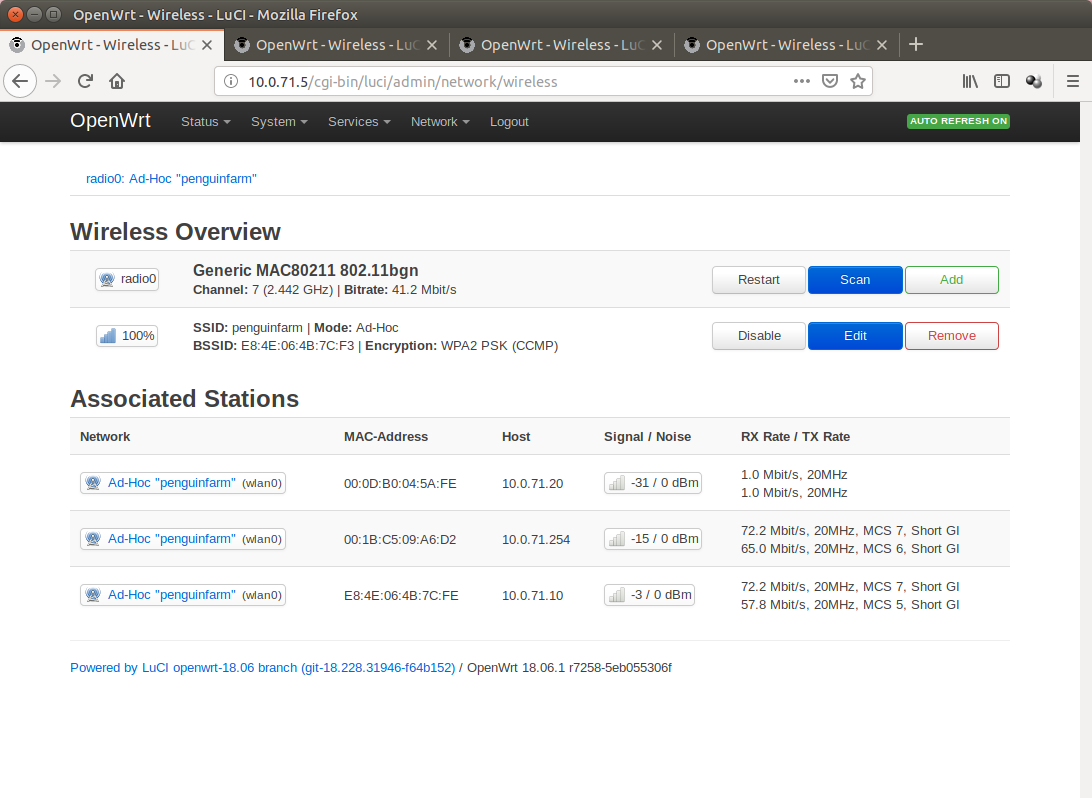
Device
10.0.71.10
FriendlyARM NanoPi NEO (256mb Ram, 2 Gb sdcard, quad-core arm, 100Mbps Lan)
RT3070 USB Wifi Dongle
Only Mesh
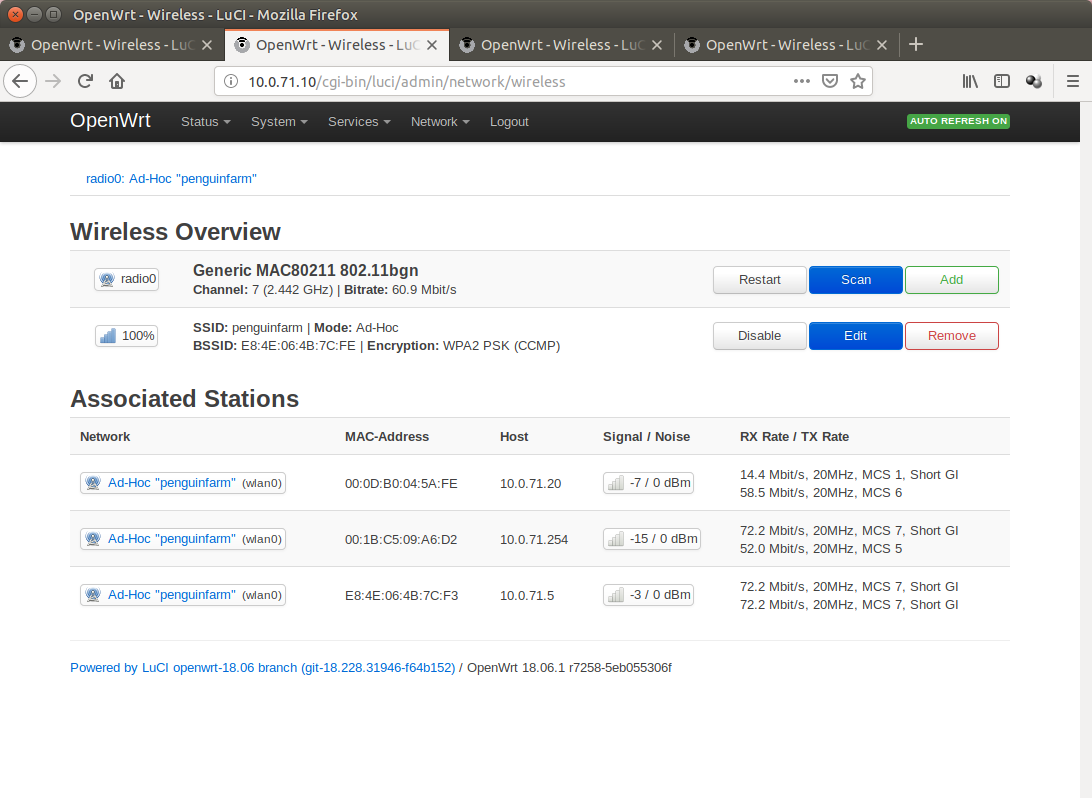
Device
10.0.71.20
FriendlyARM NanoPi NEO2 (1024mb Ram, 8gb sdcard, quad-core arm, 1Gbit Lan)
RT3070 USB Wifi Dongle
Only Mesh
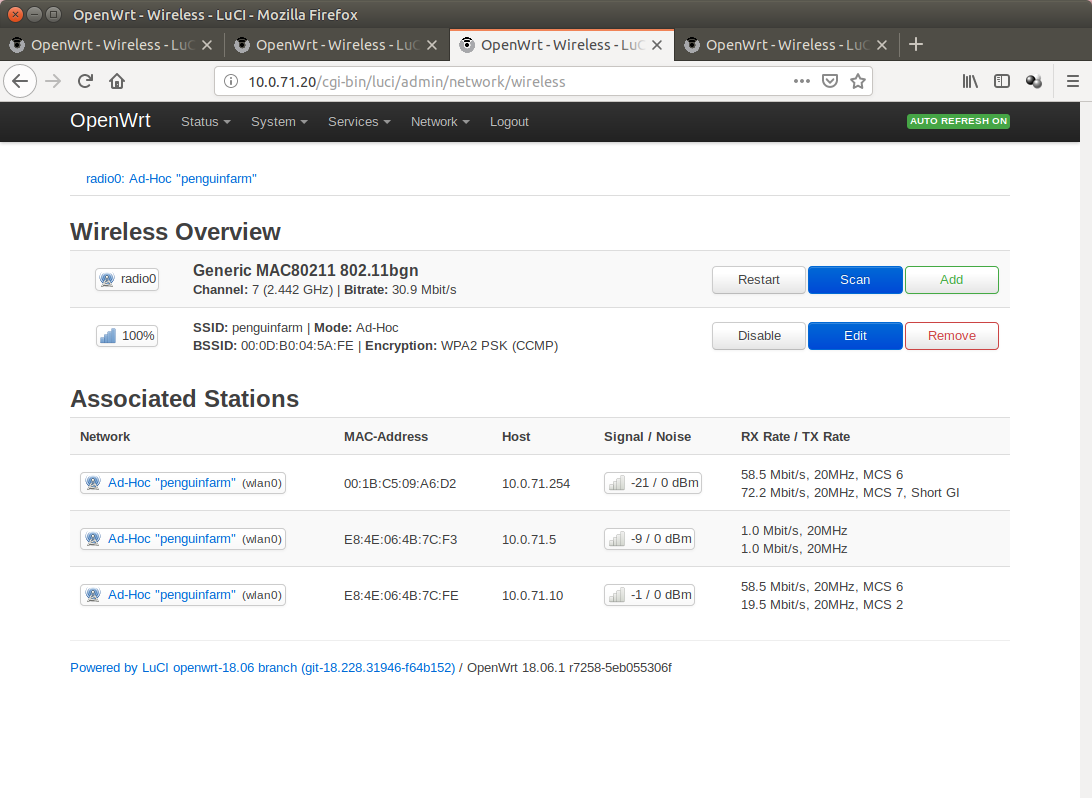
Device
10.0.71.254 (Gateway)
Model GL-iNet 6416A v1 (64mb Ram, 16mb flash, Atheros AR9330 rev 1, single core)
Access Point and Mesh same time
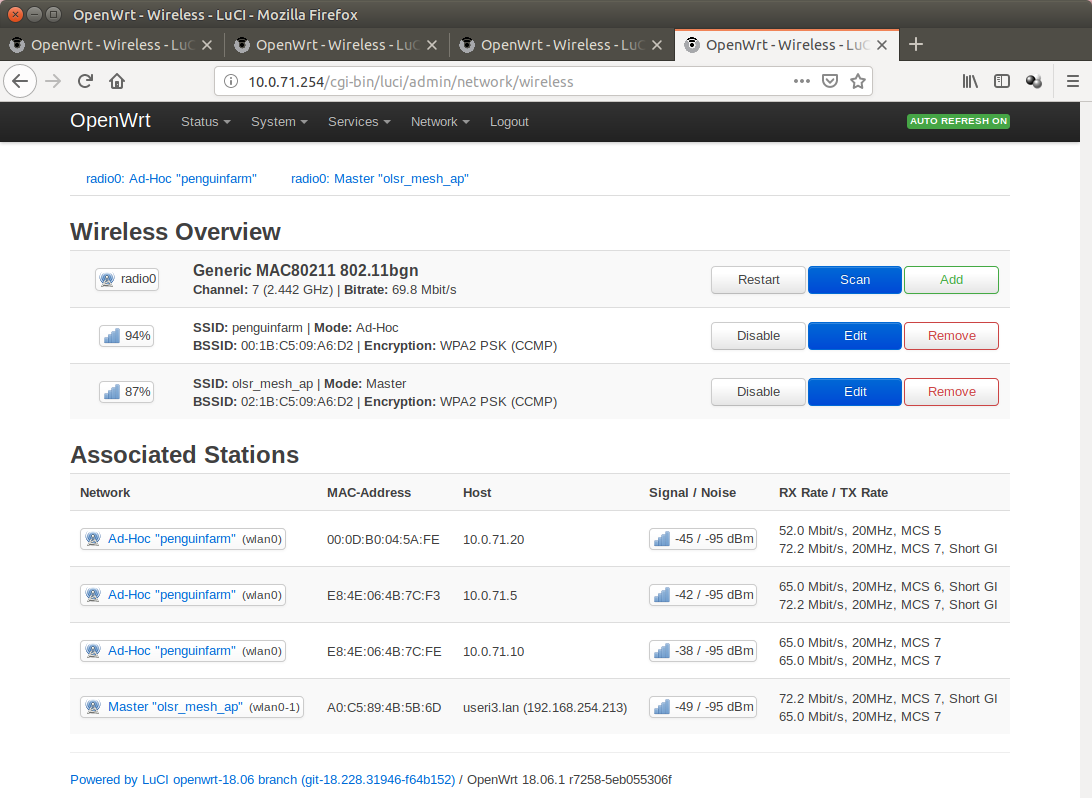
OLSR Viz
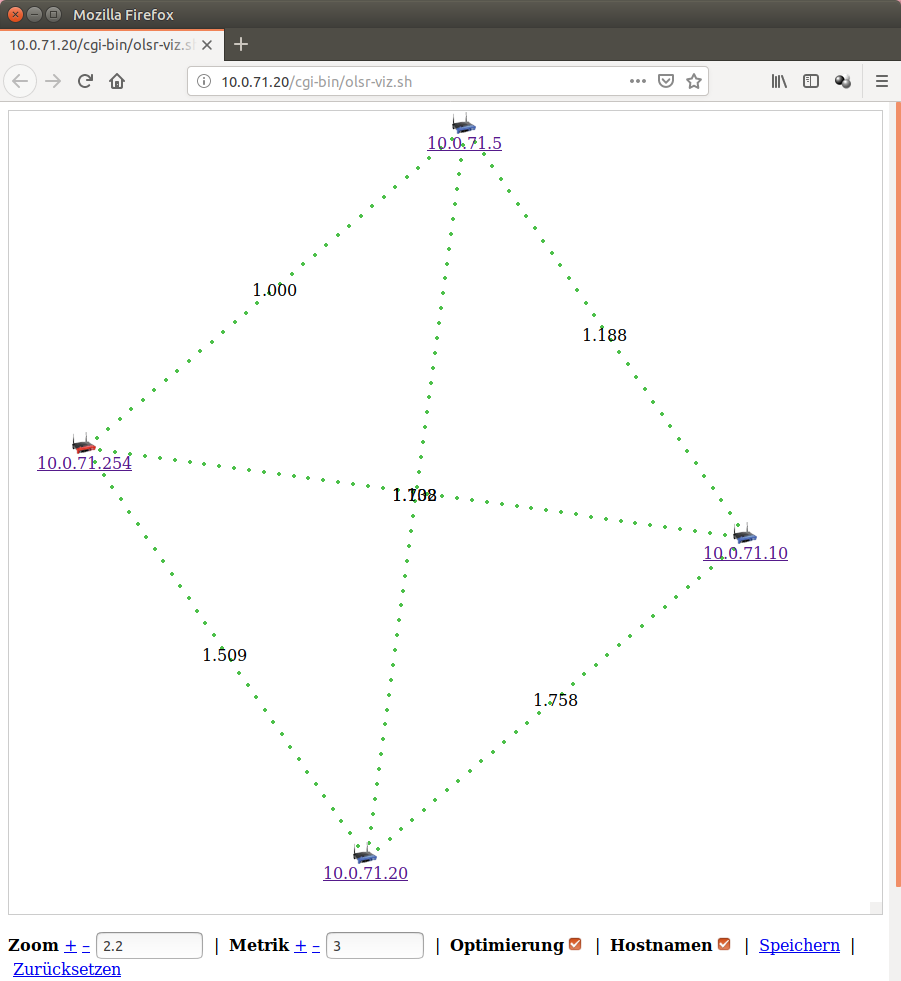
The Mesh is in fact encrypted with WPA-PSK2 (CCMP)
config wifi-iface
option device 'radio0'
option key 'thepassword'
option ssid 'penguinfarm'
option mode 'adhoc'
option network 'mesh'
option encryption 'psk2'
iw list on my ZBT WE1226s shows
[...]
Supported interface modes:
* IBSS
* managed
* AP
* AP/VLAN
* monitor
* mesh point
[...]
valid interface combinations:
* #{ IBSS } <= 1, #{ managed, AP, mesh point } <= 4,
total <= 4, #channels <= 1, STA/AP BI must match
So it should be possible to have both AP and mesh. The combination does come up, but without encryption on the mesh. It's when I try to encrypt it that the combination fails.
Yes, now i remember.
True what you saying.
I wanted a encrypted mesh and password for my wifi AP
I also tried the Onion Omaga 2 and LinkIt Smart 7688 for Mesh, which use that same MediaTek 7688 but they both had lots of issues when I last tried them
Hello! I come to tell you that I tried this configuration and it worked.
/etc/config/wireless
config wifi-iface
option device 'radio0'
option ifname 'mesh0'
option network 'lan'
option mode 'mesh'
option mesh_id 'meshdeprueba'
option mesh_fwding '1'
option encryption 'psk2+ccmp'
option key 'meshdeprueba'
option sae_password 'meshdeprueba'
And looking for the network available with another router with OpenWRT the following appears:
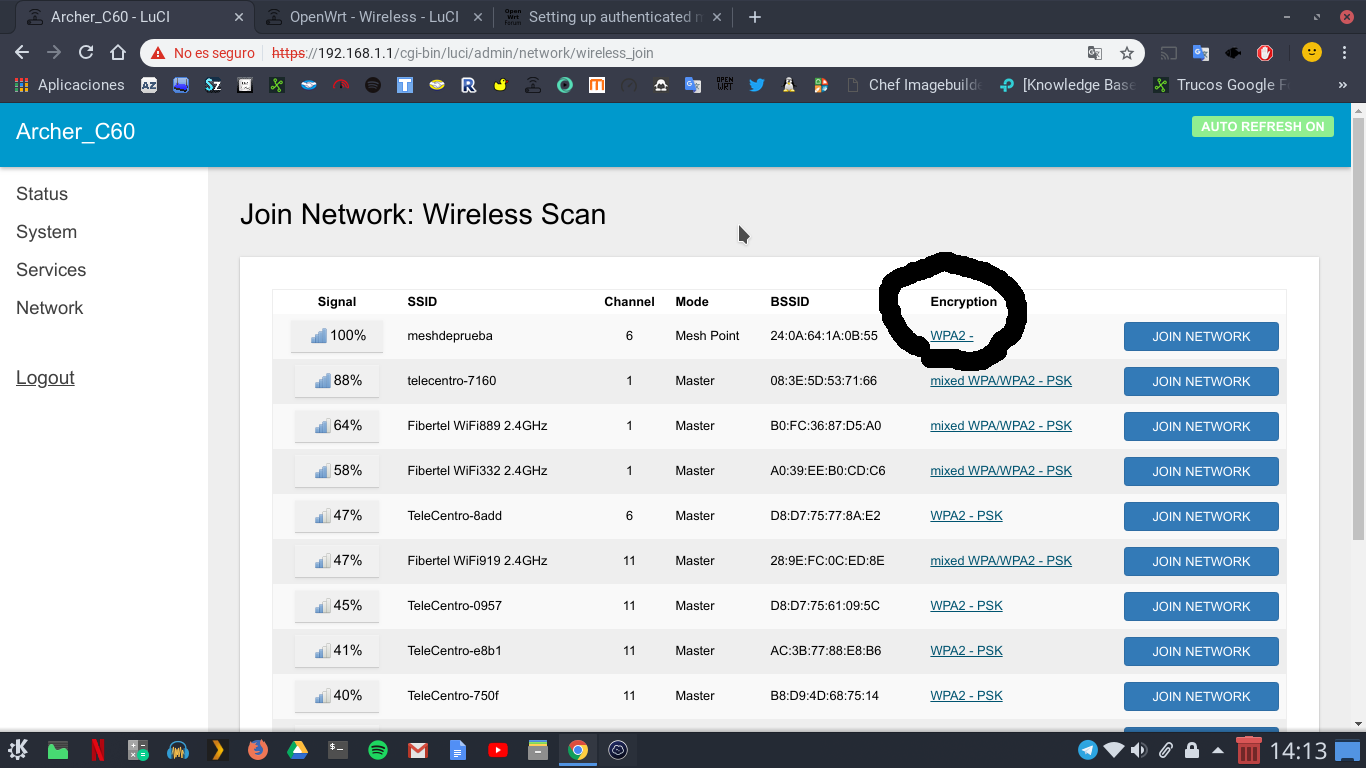
Before it appeared without encryption.
How many mesh nodes you have ?
I have a netbook and a CPE210. With the same Wireless configuration, they connect. It's just for tests and see if I could connect them with code.
You rock, Castillo!