Up until now, I was behind a CGNAT connection (which unintentionally protected me) but I will be getting a public IP tomorrow for port forwarding purposes.
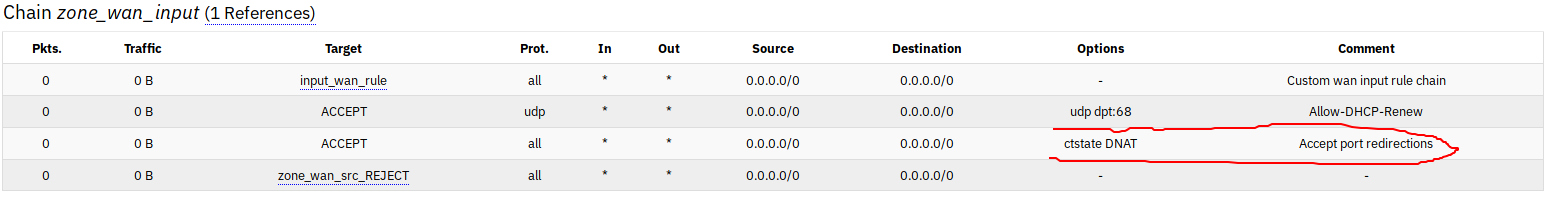
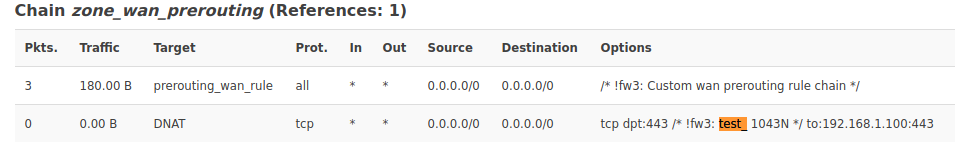
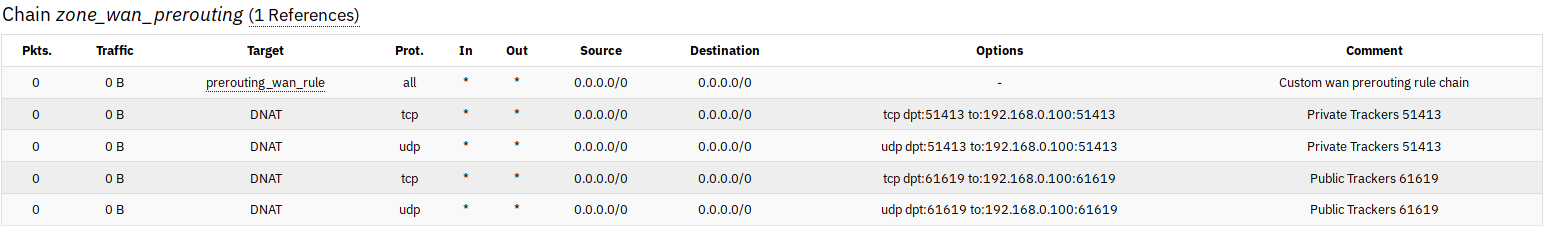
I realize that this might be a crude question but since I'm a beginner, I would like to know whether the default OpenWRT firewall configuration is "good enough" when I'm exposed to the Internet on a public IP? I'm not running uhttpd or dropbear or any other services on WAN. I'm on the latest snapshot build on a TP-Link 1043N. I'm also willing to follow relevant documentation if I'm exposed to it.
This is the output of netstat -tulpen
root@OpenWrt:~# netstat -tulpen
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.0.1:80 0.0.0.0:* LISTEN 1300/uhttpd
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1547/dnsmasq
tcp 0 0 192.168.0.1:53 0.0.0.0:* LISTEN 1547/dnsmasq
tcp 0 0 100.73.252.66:53 0.0.0.0:* LISTEN 1547/dnsmasq
tcp 0 0 192.168.0.1:22 0.0.0.0:* LISTEN 1297/dropbear
tcp 0 0 ::1:53 :::* LISTEN 1547/dnsmasq
tcp 0 0 fe80::724f:57ff:feae:f516:53 :::* LISTEN 1547/dnsmasq
udp 0 0 127.0.0.1:53 0.0.0.0:* 1547/dnsmasq
udp 0 0 192.168.0.1:53 0.0.0.0:* 1547/dnsmasq
udp 0 0 100.73.252.66:53 0.0.0.0:* 1547/dnsmasq
udp 0 0 0.0.0.0:67 0.0.0.0:* 1547/dnsmasq
udp 0 0 ::1:53 :::* 1547/dnsmasq
udp 0 0 fe80::724f:57ff:feae:f516:53 :::* 1547/dnsmasq