Hi,
I'm trying to design first and make them a config the meet the following requirements. I know, I'm network noob and you are going to read stupid thing, please forgive me.
I have a VPS, named V, with a public IP that I would like to use to expose a couple of services installed of those on a x86 machine M in my lan network.
Now, I've connected the machine M with V via a wireguard tunnel: everything works but I'm questioning what happen if they force my VPS and try to access to other services on M (actually there are not filters or other rules to avoid this) or, worst, other machines of my lan.
I thoght to use my openWrt router in some way, but I have several scenario, some unknown, and really need advices and helps to evaluate the best solution, looking also at performance (router is a R7800 with 19.07, I have a gigabit line, that is whay I made the tunnel VPS to M):
- leave the tunnel V - M and setting some iptables rules on M itself, to drop packages for ports the V must not reach, ping or whatever. This means that even if flood of packages come from VPS, the router itself may be flooded;
- connect R - V, via wireguard 10.0.0.0/32 and allow V to send directly packets to M internal lan address, f.e. 192.16.10.10, using the allowedIP parameter and some rules for iptables like the following (just an example) as describe in several site-2-site scenarios, but this means write real lan ip:port into the reverse proxy I have on the VPS (would not like):
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
- connect V - R via wireguard and do some forwarding to M in a different way of point 1, if exists (natting? port mapping?)
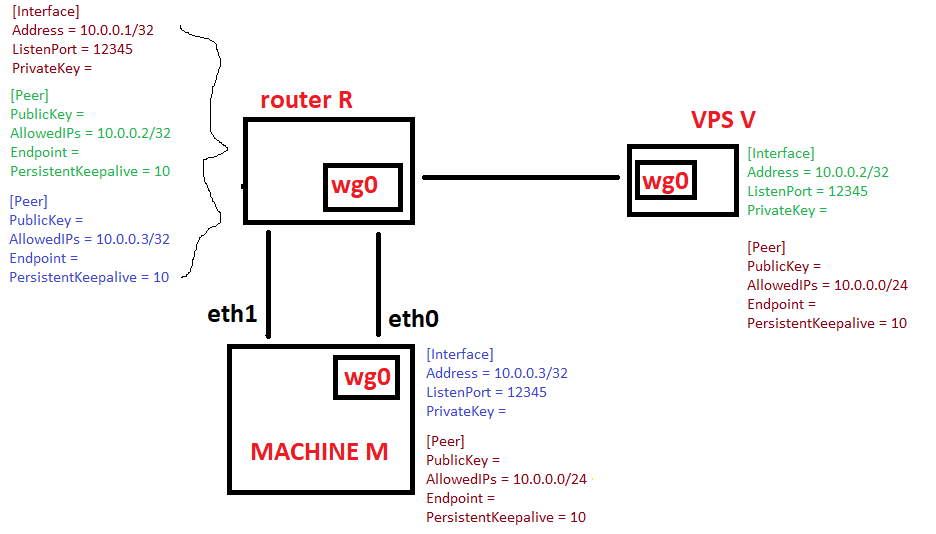
- connect all hosts, V - R - M via wireguard, on the same 10.0.0.0/24 subnet, using R a central node to automatic forward packages (need to do something special on the router?), as shown in the figure. This approach could be worst from a performance point of view because the router should take packages from the R - V tunnel, decrypt them and re-encrypt them for the R - M tunnel... I may accept it;
- using some never-used advanced (for me, but hey I would learn!) feature, creating a zone and making other configs to be sure that packages arriving from the V-R tunnel for port x, y and z and only for port x,y and z will be routed to M: others, dropped. This is not different from the previous, maybe more elegant (and give me the opportunity to learn).
Note the M has to NICs eth0 and eth1 (actually only one used) and I maybe connect both to the router and using one for a VLAN (?) for wireguard and the one for the lan access to M.
Thanks for any advice and support!!!