is this what you want?
from the windows client, gain access to the sensor on the site A/B/C/D/E
if yes, you need to set up a routed lan and have different lan address for every site
is this what you want?
from the windows client, gain access to the sensor on the site A/B/C/D/E
if yes, you need to set up a routed lan and have different lan address for every site

If this is what they're trying to accomplish, a TAP setup will likely be required.
I'll convert your config to a non-OpenWrt config.
option and list values (just the words themselves, not the actual settings they specify)_ [underscores] to - [dashes]' [single] or " [double] quotes, however this is dependent on Debian 9
Which ones? All the firewall rules I listed have their usage specified in the rule name.
Just a general FYI, if you're editing configs on a Windows or Mac OS, ensure you convert the EOLs to LF (Windows uses CRLF, Mac uses CR)
.atom folder in the user's home directory to the home directory on another OS.Yes. This is exactly what I want. We have some photovoltaic-systems. Some locations have Internet via cable. But others have only a dial-up-connection via LTE/UMTS. The problem is, that this UMTS-connected routers could not use DYN-DNS, because the providers share the IP adresses with other users. So we need the VPN to connect to the router. Each photovoltaic-system has a Data-logger we need to connect to. So the Logger is connected to the LAN-Port (it only has one!) of the router. Also sometimes we have a switch on the only LAN-Port and need more than one Device to connect. But in basic the most important thing is, that I can have access to whatever device that is connected to the LAN-Port from my homeoffice, without port-forwarding or other barriers like that.
So if I have to switch to TAP, I think I have to reconfigurate some stuff. I bet its not enough if I simply change this value in the server.conf ?
Thank you guys for investing time and helping me.
greetz Gerd
As I read here I could accomplish what I want via a server-side, or client-side ethernet-bridge.
I think the best will be to do that client-side, as maybe in future there will be different devices, that has other subnets/IPs and it will be easier to just add a bridge in that device.
why tap ?? from wiki
TUN (namely network TUNnel) simulates a network layer device and it operates with layer 3 packets like IP packets. TAP (namely network tap) simulates a link layer device and it operates with layer 2 packets like Ethernet frames. TUN is used with routing, while TAP is used for creating a network bridge.
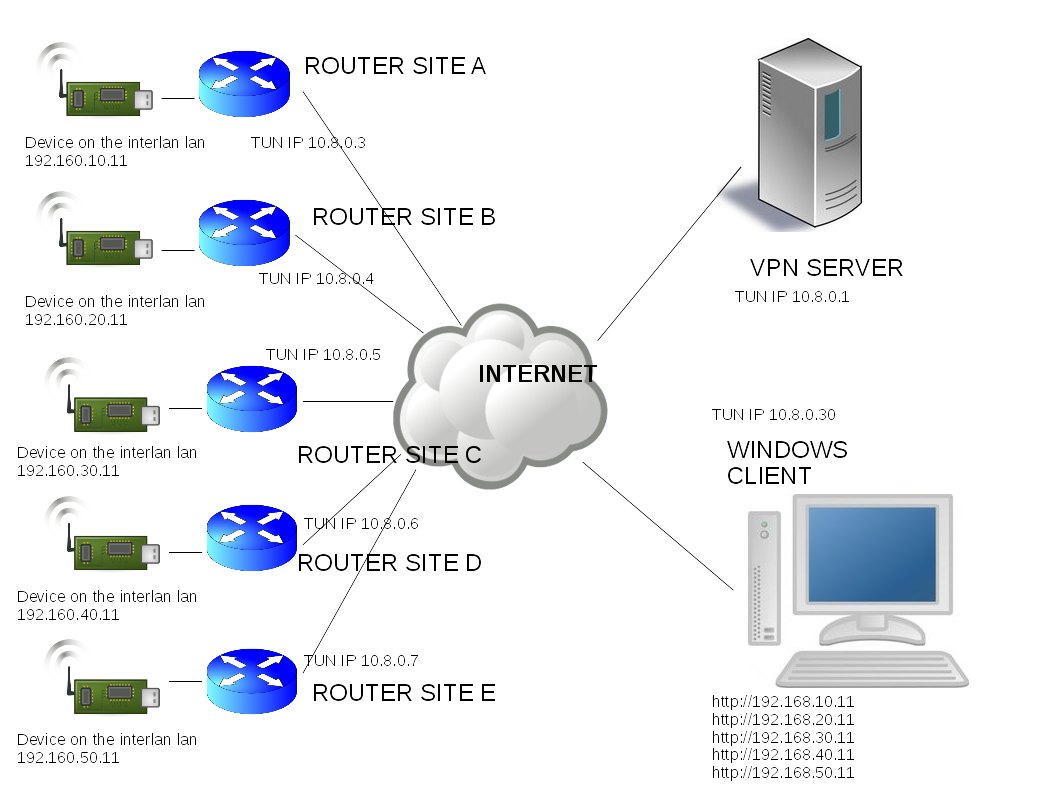
the first things you must understand is that if you need router configurations that you can't use the same network address in every location, you need a different network lan address for every sites.
as you can see in my picture i assign a different address for every site, this is the first task you must accomplish
the second task i made in my network is that for every vpn router i add in the config file on the server a line like this
push "route 192.168.10.0 255.255.255.0"
this statement need to pass the route for the network (192.168.10.0) to every router in the vpn
additional in the /ccd directory you must create a file with the same name as the certificate host name with
iroute 192.168.10.0 255.255.255.0
If multiple routers connected to the VPN will need to access each others' subnets, TAP will need to be utilized.
If those routers will ever only need access to the VPN subnet for their VPN tunnel, TUN will need to be utilized.
@revnu I didn't have time to do your config last night, but will today
The routers dont need access to each other. It is enough that I, as Administrator, can access the loggers, that are connected to the each LAN-Port, from my Homeoffice Desktop-PC.....also the Loggers need to save some data on a ftp-server that is running on the Debian-Server thats hosted online (the same Server that hosts the OpenVPN-Server).
But as I heared now I think Im going to switch to TAP anyway. As I understand it, its more futureproof for changes in our hardware-configuration. Also, If I switch to TAP, I have the option to also run one router as OpenVPNserver, if I tryout a few solutions.
I dont have the right solution for that yet. My first plan was to assign a range like 192.168.1.50-192.168.1.54 for the next router/location start with 192.168.1.55-192.168.1.59 and so on. So I can connect from my homeoffice bye simply using this local IPs.
But one more problem is, that (in some case) you have to deal with really old fashioned hardware there the logger has an fixed IP in another range (192.168.30.40 for ex.).
greetz Gerd
maybe i am wrong, but i don't agree (or i don't understand!!)
i have about 10 router with tun interface, and i can access every device everywhere in my lan
from wherever i am
i've used tun interface, then i must set up routing table in the server and in the external router (i have other subnet where i ve the server, and some smartphone access in another openvpn instance)
every router has his own network , all different , and i work on level 3 (IP)
if i use tap interface instead , i can share the same network range and work on level 2 , but the broadcast traffic cross my entire network, and with more router and more device i run out of network address very quickly in my /24 setup
last, with some UMTS and GPRS device is better to lower the broadcast traffic
am i wrong?
TUN is a point-to-point routing protocol operating at Layer 3, whereas TAP operates at Layer 2 as a virtual ethernet adapter to transparently bridge networks.
Ok, I tested some configurations last days. I switched to TAP now.
Im able to connect, and Ping the 10.8.0.3 from my Desktop-Computer. I can connect to LuCi of that Router and configurate it! Now I only have to manage the last step:
-Bridge my local subnet 192.168.1.0, so that I can connect to this IP-range from my homeoffice (The logger on that LAN will have the IP 192.168.1.30 for ex. and need access to its Web-Interface through this local IP)
Do I have to use the "server-bridge" option on client/server (both?) to manage that, or is it enough to do this in LuCi via a bridge/switch?
One more Problem:
If I change these in my /etc/config/network to switch from the cable-wan to 3g/umts, my external IP is the IP of the UMTS-provider, not the VPN-Server IP as it is then Im connected with cable:
config interface 'wan'
option proto '3g'
option device '/dev/ttyUSB2'
option service 'umts'
option apn 'mail.partner.de'
option pincode 'xxxx'
option dialnumber '*99#'
option ipv6 'auto'
config device 'wan_dev'
option name 'ttyUSB2'
So I think it is not enough to simply switch that. With cable its working fine, all trafic is passed through the VPN-Server. On 3g VPN-Client is working fine in backround. I can connect to LuCi from my homeoffice, but when I surf from a device thats connected to the routers lan-port its external IP shows me, that the lan is kinda seperated. I have to get both configurations to work, as this is my test-router. But in the end there wll be like 10 routers, some connected via cable-dsl, some via umts.
EDIT: maybe my description was a little bit confusing. What I mean is:
After that change in the /etc/config/network I can switch from cable-internet to 3g/UMTS. Then Im connected with cable-internet LAN-Devices on the router show the external IP of my debian-vpn-server. But then I switch to 3g/UMTS (usb-device) it shows the external IP of the UMTS-provider. At the same time the vpn-client is working in backround, I can connect to LuCi from my homeoffice, but it is not like it is then the router gets his internet from cable/wan-port.
I have to manage it, that UMTS works like WAN/cable,....I dont know why that is not working.
new, working config here:
server.conf:
port 1194
proto udp
dev tap
user nobody
group nogroup
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 84.200.69.80"
push "dhcp-option DNS 84.200.70.40"
push "redirect-gateway def1 bypass-dhcp"
crl-verify crl.pem
ca ca.crt
cert server_DsCVzySRePgp8eJw.crt
key server_DsCVzySRePgp8eJw.key
tls-auth tls-auth.key 0
dh dh.pem
auth SHA256
cipher AES-128-CBC
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256:TLS-ECDHE-RSA-WITH-AES-128-CBC-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA256:TLS-ECDH-RSA-WITH-AES-128-GCM-SHA256:!aNULL:!eNULL:!LOW:!3DES:!MD5:!SHA:!EXP:!PSK:!SRP:!DSS:!RC4:!kRSA
status openvpn.log
client-to-client
push 'dhcp-option NTP 212.18.3.18'
comp-lzo
verb 4
CLIENT: (pvvpn.ovpn)
client
proto udp
remote xx.xx.xx.xx xx
dev tap
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA256
auth-nocache
cipher AES-128-CBC
tls-client
tls-version-min 1.2
setenv opt block-outside-dns
verb 3
float
resolv-retry infinite
comp-lzo
<ca>
-----BEGIN CERTIFICATE-----
xxx
-----END CERTIFICATE-----
</ca>
<cert>
xxx
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
xxx
-----END PRIVATE KEY-----
</key>
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
xxx
-----END OpenVPN Static key V1-----
</tls-auth>
/etc/config/network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6b:14dc:9518::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '20:28:18:a1:5f:4e'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_dev'
option name 'eth0.2'
option macaddr '20:28:18:a1:5f:4f'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'providervpn'
option proto 'none'
option ifname 'tap0'
/etc/config/firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vpn'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'providervpn'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
This is one of the rare cases where I don't have an answer regarding OpenVPN, as I have no experience using TAP. Out of curiosity, have you searched the OpenVPN forum? If you can't find something via search, I'd recommend posting the content of your last post in a new thread on the OpenVPN forum.
Yes I read much last days. Got a little bit stuck with that problem, that it only works with cable, not with UMTS.
I think ne next thing I have to do is a server-bridge.
Just wanted to get feedback, that I SOLVED the problem now.
I switched the LAN-interface to the same subnet of the VPN-server (10.8.0.0). After that, I bridged the LAN-interface on the router with the virtuell VPN-tap-device. I have access to ALL devices on every LAN-port of the 10 routers. I deactivated DHCP on all routers and work with static IPs.
Thank you guys for helping me out
Gerd