There are a whole lot of issues here...
You seem to have the lan and WLAN0 networks as DHCP clients, so there is no practical way to connect or route properly.
- Is this router at location 1 or location 2? [EDIT: I can assume this is location 2, based on the WG config; please correct me if I'm wrong]
- How is this router connecting to the upstream network?
- How are your clients going to connect to this device?
You may be best off making a backup (mainly for the sake of the WG config stanzas of the network file), and then resetting to defaults. But let's start with the answers to the questions I've just asked.
EDIT: Some more thoughts and explanation of the issues I'm seeing right now...
Starting with your wlan0 network...
The wlan devices should never be referenced in the network config file. You'll specify the network that a given SSID should use in the wireless config file.
If this network will be used on dual band (i.e. 2 radios, 2.4G and 5G) and/or will be used on ethernet, you'll need to create a bridge (outside the network interface stanza) to use here. If it's only being used on a single band and not being used on ethernet at all, you don't need a bridge
DNS won't do anything here, so remove both the peer dns and dns entry you've put in (where did that come from, anyway?).
If this is a network that will be used for the clients to connect, it needs an address, and it also will need a DHCP server (in the vast majority of cases).
On the lan:
same deal here -- if clients should be able to connect to your lan (via wireless and/or wired), it needs an address and a DHCP server.
Is the uplink on the wan or the lan? If the lan, your firewall needs masquerading enabled on the lan zone. And for that to work, you'd also have to split out the wlan0 network into a different zone. If it's on the wan, this is fine.
If you intend to route all traffic through the tunnel, the correct allowed_ips is 0.0.0.0/0
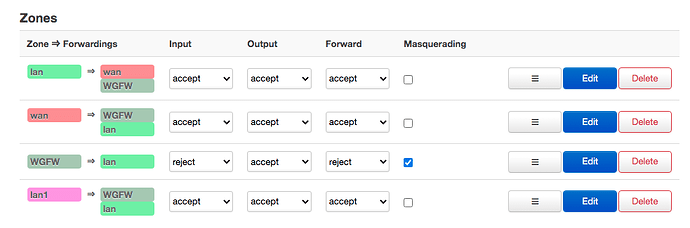
Also, your wireguard network is not associated with a firewall zone. You need to have it in a zone and then allow forwarding from the zone where the 'clients' connect to the wireguard zone.
We also haven't seen your DHCP or wireless files.
My guess is that a reset to defaults will be the best approach here... but we need to understand the questions I asked above.