I really don't think that's possible you don't want traffic destined for the router to be sent by the veth my advice would be to just ignore traffic destined to the router because it should be a tiny fraction of the total traffic
Intriguingly I found that:
Initially worked, but eventually resulted in loss of internet connectivity. That seemed a nice sort of 'catch all' to catch any outgoing traffic originating from router and ensure it goes through VPN.
So I have instead opted for:
14000: from all to 185.228.168.168 lookup vpn
14000: from all to 185.228.169.168 lookup vpn
Does that look OK for redirecting output DNS queries from router to VPN rather than WAN?
I'm not sure what the correct way to do any of this is. Will my router still use DNS caching?
You need to add a rule for traffic from "iif lo" to the vpnserver will use wan with higher priority.
Does setting up the VPN tunnel require a DNS query? If yes and you lose the VPN it won't be able to start up again. Make sure you use IP addresses for the VPN endpoint and then it might work better.
You might also want a hot plug rule to change the routing if the VPN goes down
Would you be able to put that another way? I can't compute.
Traffic trying to reach the VPN server can't go inside the VPN tunnel obviously (it is the tunnel) it needs to be sent out the actual wan. So you need an earlier rule that selects wan for traffic going to the VPN provider.
Right - thanks both!
How do I know whether DNS caching is being used? I have different DNS for televisions (to get round CleanBrowsing's filters for YouTube).
DNS traffic will use the same rules that you have. However if the nameservers belong to your ISP, then you must use the wan uplink to reach them, as they won't allow IPs outside their address space to use recursion.
Regarding caching, it usually is being used for as long as the TTL of the record is configured.
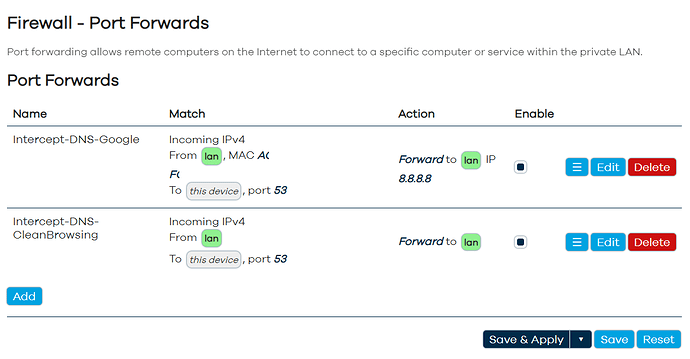
Thanks. So I have this set up in firewalls:
Will caching apply in respect of the 8.8.8.8 hijacks and also the router hijacks to the custom DNS I have set?
I am not sure what have you done there, so my answer might be wrong.
In the first redirect you are forcing dns queries pointed to the router to go to GoogleDNS? Why not advertise GoogleDNS directly to that host?
In the second redirect you hijack everything to dnsmasq, so dnsmasq will be caching the answers.
Wouldn't that then get hijacked by the router?
The context is I want to block immoral material using CleanBrowsing but allow televisions to access YouTube material without restriction.
Ah great - this is most important since the televisions are only the exception. So I'm more bothered about caching everything else.
You can add a rule to circumvent the hijack for this mac address.
I use WireGuard with source IP: 10.5.0.2. Rather than setting traffic to VPN server IP to use WAN can I instead have traffic from iif lo with source 10.5.0.2 use WAN? I tried to set this, but this gave rule:
14000: from 10.5.0.2 iif lo lookup wan
Does that seem right?
So in sum I have:
14000: from 10.5.0.2 iif lo lookup wan
15000: from all iif br-lan lookup vpn
15000: from all iif lo lookup vpn
No, that is wrong.
Although I need to say that it would be easier to setup the policy routing with pbr package
Please can you elaborate?
The tunnel IP of OpenWrt will never be used to establish the connection over the internet with the other endpoint.
But why is that not covered by:
14000: from 10.5.0.2 iif lo lookup wan
Or is that source not used to establish tunnel?
My reason for wanting to use source is what happens if the peer changes? I then need to keep changing all the entries. Whereas the source is fixed. So if it can be done that way it seems desirable.
Hope this makes sense.
How about set a rule that says anything from your lan subnet goes via the wire guard tunnel and everything else goes by the wan. Then the routers traffic itself will go on the wan.
That.
Then you need to use a matching condition that will be always true, even if the peer changes.
Not really, I still don't understand why you are trying to reinvent the wheel, when I already mentioned pbr package which does already what you are trying to do.
The PBR maintainer apparently has no interest in facilitating establishing single interface upon which to apply SQM, so for those of us who want single interface that sees both VPN and non-VPN traffic to apply SQM to combined flows it's a case of DIY'ing it. Happily because of the recent LuCi changes it's really easy anyway.
But to capture DNS queries from the router I think I need everything from router except for setting up WireGuard tunnel.
I'm just not yet sure what the rule should be without fixing it to WireGuard peers that change. Any thoughts?
With:
15000: from all iif lo lookup vpn
Won't that fail when vpn is down such that the traffic to set up tunnel goes through wan?