Overview... Why can't I route data between VLAN2 and VLAN5 it used to talk to a WAN port. I'm so confused.
Ok, here's the scenario I've been battling the last few days and it's gonna be something really simple I've missed.
My Main router HomeHub5a (HH5a) running 17.01.4, r3560-79f57e422d used to be connected directly to an ADSL line, all my vlans routed perfectly everything was awesome.
Recently, I've changed ISP, I'm not able to use my router directly with the ADSL line anymore. However, I would like to continue to use my old HH5a, as it i like the adblock and other functionality I've configured. I want to leave the ISP router standard but have my HH5a route to it.
The new ISP router IP address range is 192.168.0.1/24
On the HH5a I have configured the physical LAN Port 4 to have a vlan id of 2. connected this port to the new ISP router and set a static IP address of 192.168.0.3. 192.168.0.3 is also reserved on the ISP router.
On the HH5a I have configured the physical LAN port 3 to have a vlan id of 5. This VLAN has a static IP address of 192.168.5.1/24. for DHCP on this VLAN is configured to be Default gateway 192.168.5.1.

From devices on the ISP router (192.168.0.1/24) i can successfully ping 192.168.0.1 (default gateway) and 192.168.0.3 (HH5a Port4). Therefore the route between the ISP router HH5a is working. However, I am unable to ping 192.168.5.1.
From a device on vlan id 5 of the HH5a (192.168.5.2), I can ping 192.168.5.1 and 192.168.0.3. but not 192.168.0.1 or anything on the internet.
if i do this locally on the HH5a...
ping -I br-LAN5 192.168.5.2 #I can ping this device on VLAN5
ping -I br-LAN5 192.168.0.3 #This fails
This is my network config
cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd46:0ba0:8372::/48'
config atm-bridge 'atm'
option encaps 'llc'
option payload 'bridged'
option vci '38'
option vpi '0'
config dsl 'dsl'
option xfer_mode 'ptm'
option annex 'b'
option tone 'a'
option line_mode 'vdsl'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '40:f2:01:47:99:9e'
config interface 'wan'
option _orig_ifname 'ptm0'
option _orig_bridge 'false'
option type 'bridge'
option ifname 'ptm0'
option proto 'none'
config device 'wan_dev'
option name 'ptm0'
option macaddr '40:f2:01:47:99:9f'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '5'
option ports '0 2 4 5t 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '1 6t'
config interface 'vpnserver'
option proto 'none'
option auto '1'
option delegate '0'
option _orig_ifname 'ovpns0'
option _orig_bridge 'true'
option ifname 'ovpns0'
config interface 'LAN2'
option _orig_ifname 'eth0.2'
option _orig_bridge 'true'
option ifname 'eth0.2'
option proto 'static'
option ipaddr '192.168.0.3'
option netmask '255.255.255.0'
option gateway '192.168.0.1'
option broadcast '192.168.0.255'
option dns '1.1.1.1'
config interface 'LAN5'
option proto 'static'
option ipaddr '192.168.5.1'
option netmask '255.255.255.0'
option dns '192.168.5.3'
option type 'bridge'
option _orig_ifname 'eth0.5'
option _orig_bridge 'true'
option ifname 'eth0.5'
option broadcast '192.168.5.255'
option gateway '192.168.0.1'
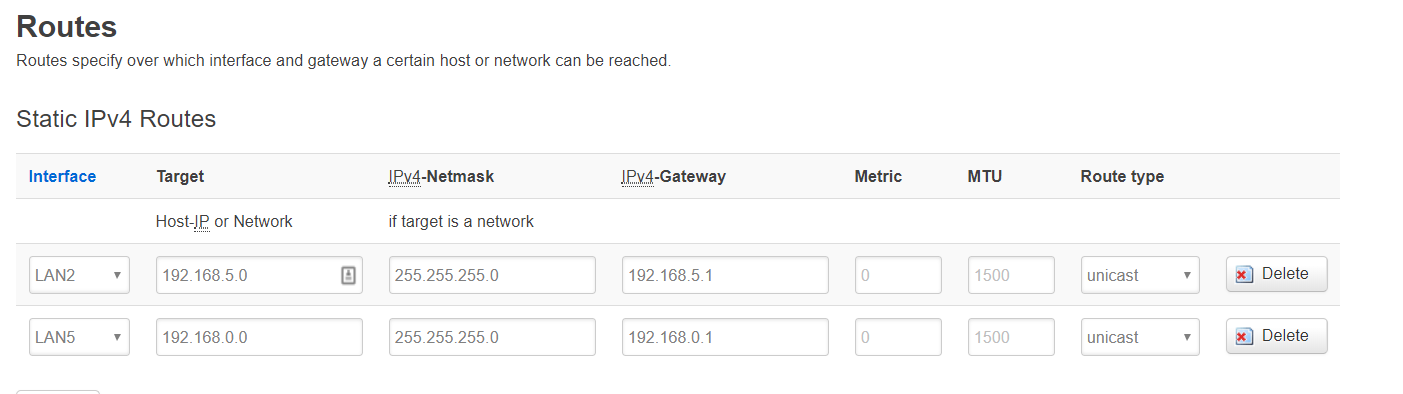
config route 'Route_Lan2'
option interface 'LAN2'
option target '192.168.5.0'
option gateway '192.168.5.1'
option netmask '255.255.255.0'
config route 'Route_Lan5'
option interface 'LAN5'
option target '192.168.0.0'
option gateway '192.168.0.1'
option netmask '255.255.255.0'
config interface 'lan'
option proto 'static'
option ifname 'eth0'
This is my firewall config... (I've tried to open everything up to test this...)
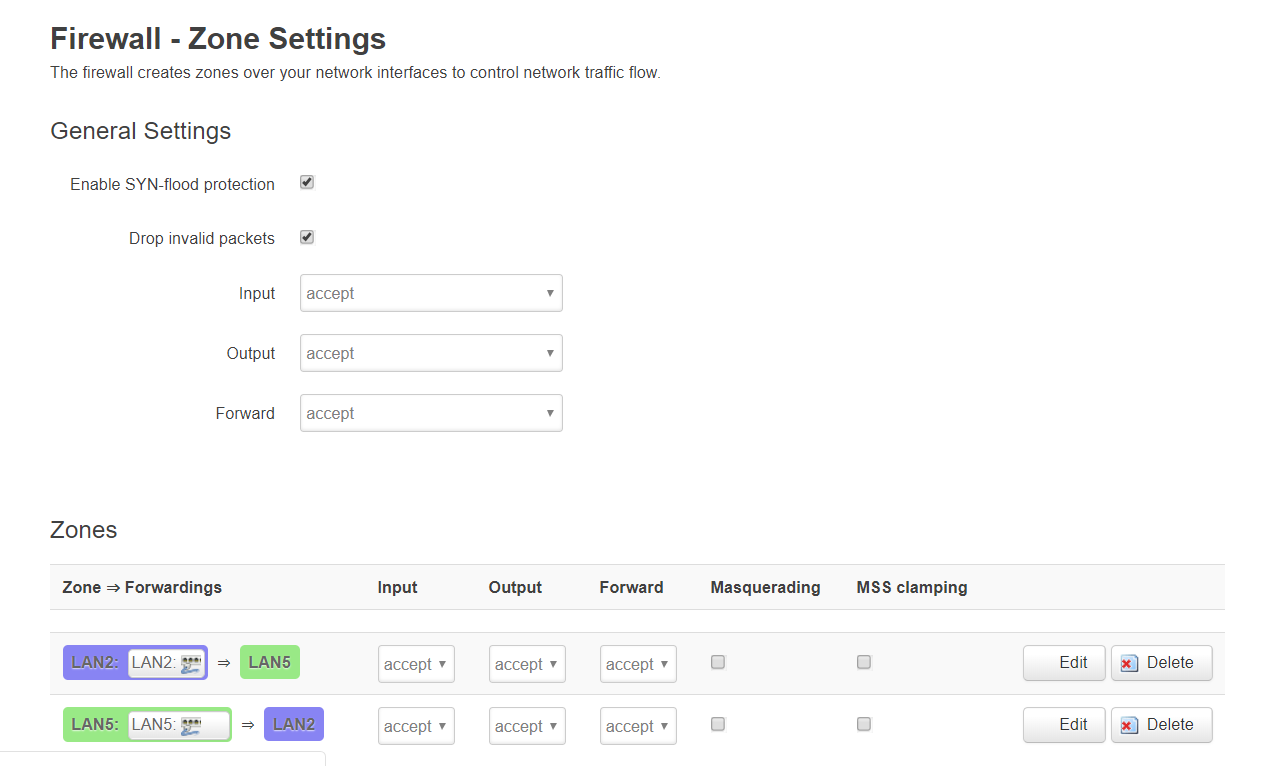
cat /etc/config/firewall
config defaults
option syn_flood '1'
option drop_invalid '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'LAN2'
option forward 'ACCEPT'
option network 'LAN2'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'LAN5'
option forward 'ACCEPT'
option network 'LAN5'
config forwarding
option src 'VLAN2'
option dest 'VLAN5'
config forwarding
option src 'VLAN5'
option dest 'VLAN2'
config forwarding
option dest 'LAN5'
option src 'LAN2'
config forwarding
option dest 'LAN2'
option src 'LAN5'
config rule
option target 'ACCEPT'
option name 'Test'
option src '*'
option dest '*'
config redirect
option target 'DNAT'
option src 'LAN2'
option dest 'LAN5'
option proto 'tcp udp'
option name 'external'
config redirect
option target 'DNAT'
option src 'LAN5'
option dest 'LAN2'
option proto 'tcp udp'
option name 'internal'
This is the output of my route config.
PIEFIE:~$ route -e
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
default 192.168.0.1 0.0.0.0 UG 0 0 0 eth0.2
192.168.0.0 * 255.255.255.0 U 0 0 0 eth0.2
192.168.5.0 * 255.255.255.0 U 0 0 0 br-LAN5
192.168.200.0 * 255.255.255.0 U 0 0 0 ovpns0
PIEFIE:~$ ip route show
default via 192.168.0.1 dev eth0.2
192.168.0.0/24 dev eth0.2 src 192.168.0.3
192.168.5.0/24 dev br-LAN5 src 192.168.5.1
192.168.200.0/24 dev ovpns0 src 192.168.200.1
PIEFIE:~$ cat /etc/iproute2/rt_tables
#
# reserved values
#
128 prelocal
255 local
254 main
253 default
10 InternetOut
0 unspec
#
# local
#
#1 inr.ruhep
Please help 