I have a router SBC with OpenWrt 22.03.2 x86 bare metal.
Another computer running Proxmox 8.0.
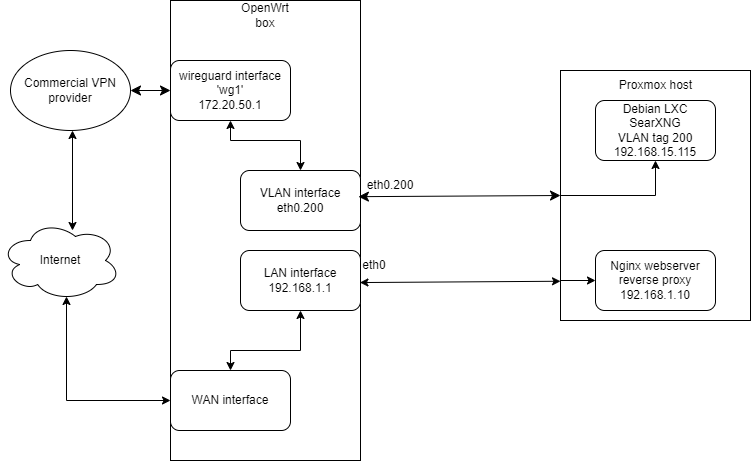
On the Proxmox host I am running two containers, one Nginx reverse proxy and one running the popular Searx meta-searchengine instance that search on numerous search engine at once (and later also other various applications). My goal is to be to be able to navigate to a domain name and reach the Searx website through HTTPS (already set up and working), and have all outbound traffic from that container instance be routed through a Wireguard interface (connected to commercial VPN provider) to the internet. I do not want the traffic that hits the search engines to originate from my WAN IP address, but instead the commercial VPN provider's IP address.
The reverse proxy though, is hosted on my network and the domain name is pointing to my ISP IP address on port 80/443.
The proxmox computer and OpenWrt box is connected through a single LAN cable. The container for the Debian system on which the Searx application runs on is set to VLAN 200 on the same vmbr0 bridge as the host and the container with the reverse proxy. The reverse proxy is not on VLAN, only the container whose outbound traffic I want to be routed through VPN is.
I created a Wireguard interace with the config file from my VPN provider, along with a firewall zone wg1.
I also created a VLAN interface on eth1 with VLAN ID 200 (named vpn1), and with its corresponding firewall zone also named vpn1.
In the Debian container console I can ping the router which means the VLAN is working fine, and the container gets a DHCP address in the 192.168.15.0/24 subnet.
The wireguard interface also connects to the VPN provider since I can ping through it:
root@OpenWrt:~# ping -I wg1 1.1.1.1
PING 1.1.1.1 (1.1.1.1): 56 data bytes
64 bytes from 1.1.1.1: seq=0 ttl=59 time=15.710 ms
I have also created an IPv4 Rule in the luci firewall menu that routes all traffic (0.0.0.0/0) on the vpn1 interface through the wg1 interface. I have tried both the main and default tables.
I enabled logging for the firewall so I could see what happens and this is the syslog when I ping 1.1.1.1 from the Debian container:
kern.warn kernel: [ 3020.837560] reject vpn1 forward: IN=eth1.200 OUT=eth0 MAC=********** SRC=192.168.15.115 DST=1.1.1.1 LEN=84 TOS=0x00 PREC=0x00 TTL=63 ID=9010 DF PROTO=ICMP TYPE=8 CODE=0 ID=51580 SEQ=3
The ping shows:
root@debian12:~# ping 1.1.1.1
PING 1.1.1.1 (1.1.1.1) 56(84) bytes of data.
From 192.168.15.1 icmp_seq=1 Destination Port Unreachable
The IPv4 rule does not apply here or maybe I am misunderstanding something. The traffic that originate from eth1.200 forwards to eth0 which is the WAN interface and not wg1.
I hope you can get a clear picture of what I am trying to achieve here.
In step number two, I also need the reverse proxy to be able to forward traffic to and from the Nginx proxy and the Searx application container. I do not understand why the traffic points to eth0 and not wg1. I have set "Route Allowed IPs" in the WG1 interface config.
I do not want to run the reverse proxy in the same container as other applications so I cannot use unix sockets instead of TCP/IP stack.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdfe:efeb:d8e3::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
list ports 'eth2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
config device
option name 'eth1'
config device
option type '8021q'
option ifname 'eth1'
option vid '500'
option name 'eth1.500'
config interface 'wg1'
option proto 'wireguard'
option private_key '*************************************'
option peerdns '0'
option force_link '1'
list addresses '172.20.50.1/32'
config wireguard_wg1
option public_key '**************************************'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option endpoint_host '***.***.***.***'
option endpoint_port '*****'
option route_allowed_ips '1'
config device
option type '8021q'
option ifname 'eth1'
option vid '200'
option name 'eth1.200'
config interface 'vpn1'
option proto 'static'
option device 'eth1.200'
list ipaddr '192.168.15.1/24'
config rule
option in 'vpn1'
option out 'wg1'
option lookup 'default'
/etc/config/firewall
config redirect
option dest 'lan'
option target 'DNAT'
option src 'wan'
option name 'Nginx HTTP'
option src_dport '80'
option dest_port '80'
option dest_ip '192.168.1.10'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Nginx HTTPS'
option src 'wan'
option src_dport '443'
option dest_port '443'
option dest_ip '192.168.1.10'
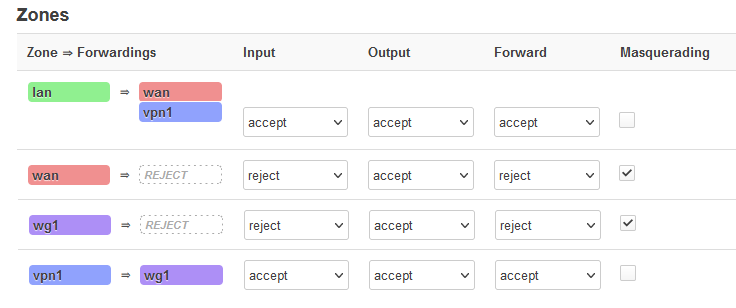
config zone
option name 'wg1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wg1'
option masq '1'
option mtu_fix '1'
option log '1'
config zone
option name 'vpn1'
option output 'ACCEPT'
list network 'vpn1'
option input 'ACCEPT'
option forward 'ACCEPT'
option log '1'
config forwarding
option src 'vpn1'
option dest 'wg1'
config forwarding
option src 'lan'
option dest 'vpn1'