Dear all,
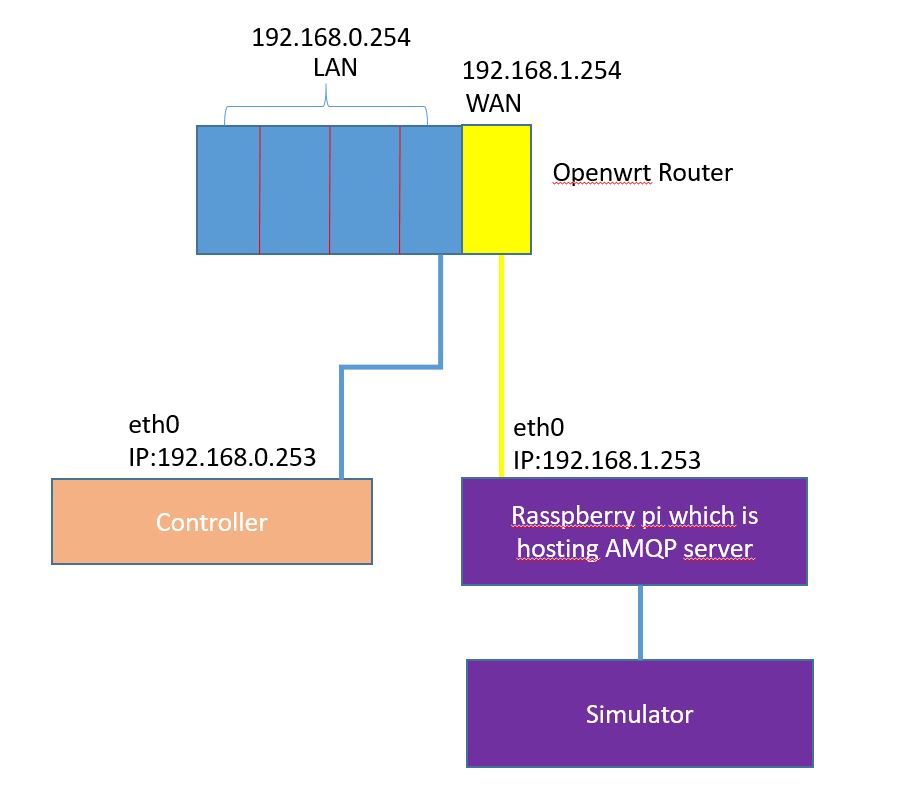
I want to connect Rasberry pi which is hosting server to WAN port as below. The use of OpenWrt router is to make a command signal delay with netem network emulator.
what I have done
- set a proper static IP address for routing.
problem
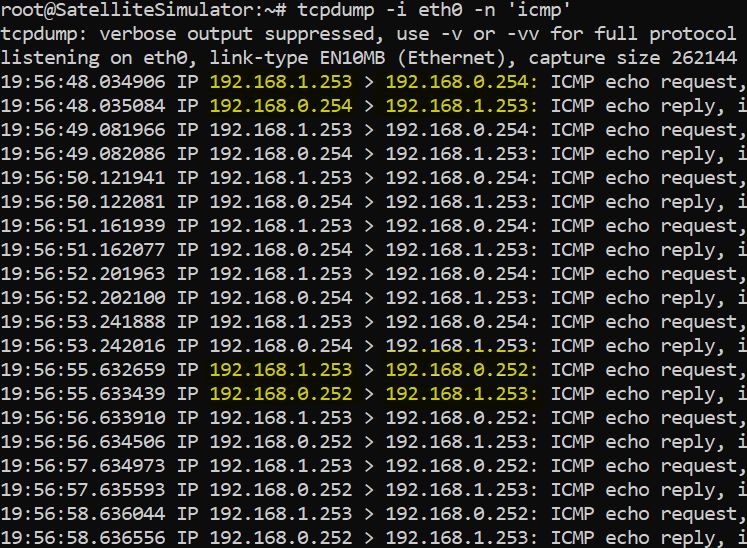
I can ping both controller(192.168.0.253) and raspberry pi(192.168.1.253) from OpenWrt router. From the raspberry pi, I can ping to controller. It means that there is no problem for routing from WAN TO LAN
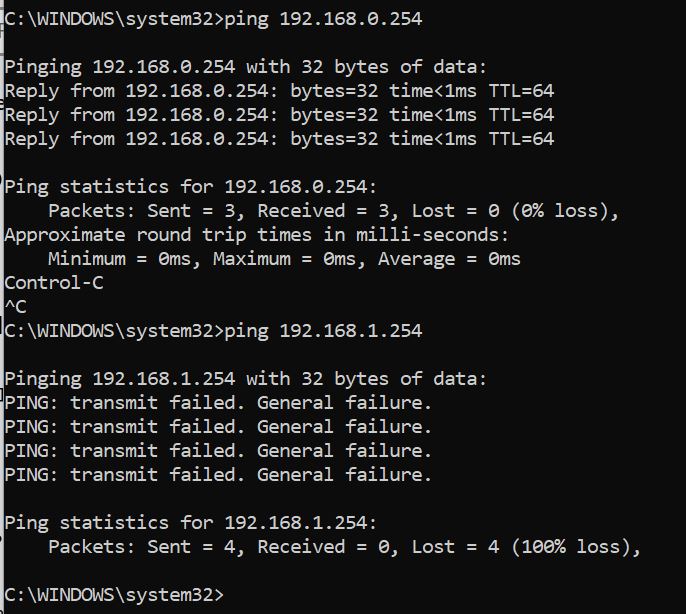
However, WAN port(192.168.1.154) is not reachable from controller.
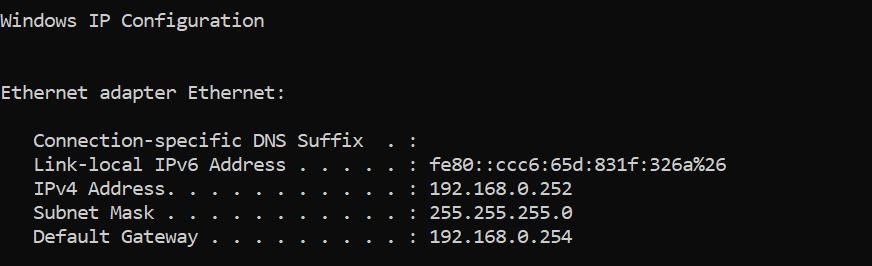
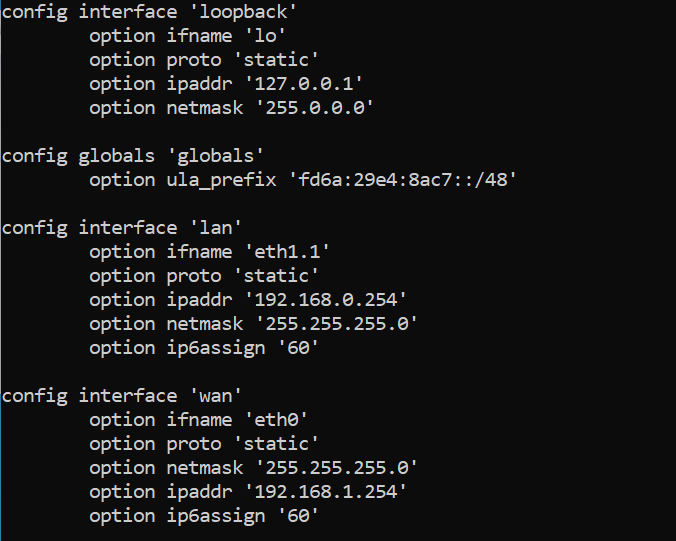
Current ip configuration of router.
Current route-configuration
Current firewall setting
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone option name wan
list network 'wan'
list network 'wan6'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
Allow DHCPv6 replies
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
I need your advice on this problem
please let me know if you need further config information.
Best regards
Byeon Seongsu

 )
)