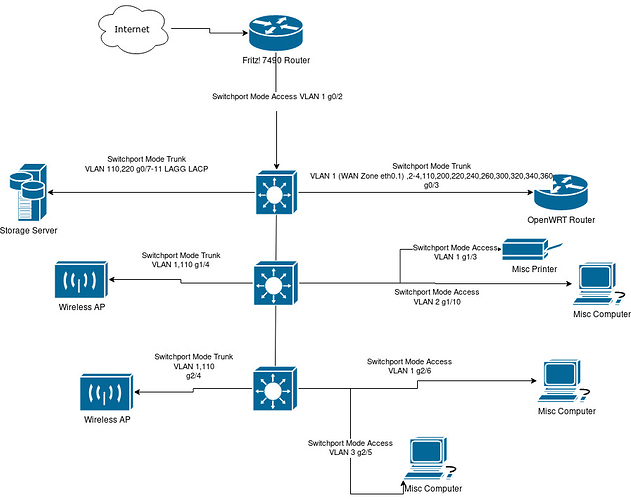
Ahoy friends.
So what did i try? I have set the OpenWRT router's lan port to access mode, using VLAN 2.
Then i set my PC's lan port also to VLAN 2, but no ip is being assigned by the DHCP. Talking about OpenWRT default settings. When using OpenWRT attached to the computer without network, it works.
So it must be something with the network, but any clue what?
Unfortunately the PPPoE way is not that easy, because i also have to use the device as DECT base, because of my phones.
My Coreswitch's config:
config-file-header
CRSW-K-01
v1.4.11.5 / R800_NIK_1_4_220_026
CLI v1.0
set system mode switch
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
spanning-tree loopback-guard
spanning-tree priority 4096
vlan database
vlan 2-4,110,200,220,240,260,300,320,340,360
exit
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
loopback-detection enable
errdisable recovery interval 6000
errdisable recovery cause loopback-detection
errdisable recovery cause stp-bpdu-guard
errdisable recovery cause stp-loopback-guard
hostname CRSW-K-01
no passwords complexity enable
passwords aging 0
username admin password encrypted 2bdd1322fd78e4df8d37249a406cd6e8b5359741 privilege 15
username cisco password encrypted 2bdd1322fd78e4df8d37249a406cd6e8b5359741 privilege 15
ip ssh server
snmp-server server
snmp-server location KELLER
snmp-server contact HOLZ
snmp-server community holz ro view Default
clock timezone DFL +1
clock summer-time web recurring eu
sntp server 134.130.4.17
sntp source-interface vlan 110
!
interface vlan 110
name MGMNT
ip address 172.20.32.100 255.255.224.0
no ip address dhcp
!
interface gigabitethernet1
switchport mode access
switchport access vlan 110
!
interface gigabitethernet2
switchport mode access
switchport access vlan 110
!
interface gigabitethernet3
switchport mode access
switchport access vlan 110
!
interface gigabitethernet4
switchport mode access
switchport access vlan 110
!
interface gigabitethernet5
switchport mode access
switchport access vlan 110
!
interface gigabitethernet6
switchport mode access
switchport access vlan 110
!
interface gigabitethernet14
switchport mode access
switchport access vlan 110
!
interface gigabitethernet15
switchport mode access
switchport access vlan 110
!
interface gigabitethernet16
switchport mode access
switchport access vlan 110
!
interface gigabitethernet17
switchport mode access
switchport access vlan 110
!
interface gigabitethernet18
switchport mode access
switchport access vlan 110
!
interface gigabitethernet23
channel-group 2 mode auto
!
interface gigabitethernet24
channel-group 2 mode auto
!
interface gigabitethernet25
channel-group 2 mode auto
!
interface gigabitethernet26
channel-group 2 mode auto
!
interface gigabitethernet27
channel-group 1 mode auto
!
interface gigabitethernet28
channel-group 1 mode auto
!
interface Port-channel1
flowcontrol auto
loopback-detection enable
switchport trunk allowed vlan add 2-4,110,200,220,240,260,300,320
switchport trunk allowed vlan add 340,360
!
interface Port-channel2
loopback-detection enable
description Core-PoE
switchport trunk allowed vlan add 2-4,110,200,220,240,260,300,320
switchport trunk allowed vlan add 340,360
!
exit
ip default-gateway 172.20.32.1
encrypted ip ssh-client key rsa key-pair
The switch below the coreswitch, which is connected to the AP in the mid of the diagram.
According to Wireshark listening on the VLAN 2 interface, there is no DHCPOFFER from the router. Only DHCPDISCOVER from the client.
Now i got some news. Quite annoying.
According to Wireshark there is an ICMPv6 router advertisement.
So i've activated IPv6 on my client for now. It seems to receive something, because according to Gnome NetworkManager my device is "connected" successfully.
But i want to let it work with IPv4, how to do so?
EDIT: Some news. Now receiving an IPv4 lease, after disabling all the IPv6 stuff on the OpenWRT interface, and after disabling bridge multicast filtering on the Cisco Switch. Now i'll try with VLANs.
Things work fine when using DHCP on the eth0 interface not the dotted ones, like eth0.2.
Do i have to create the VLANs with bridged interfaces, or directly assing the dotted one?
config-file-header
PSW-K-01
v1.4.11.5 / R800_NIK_1_4_220_026
CLI v1.0
set system mode switch queues-mode 4
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
spanning-tree loopback-guard
spanning-tree priority 12288
bridge multicast filtering
vlan database
vlan 2-4,110,200,220,240,260,300,320,340,360
exit
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
loopback-detection enable
errdisable recovery interval 6000
errdisable recovery cause loopback-detection
errdisable recovery cause stp-bpdu-guard
errdisable recovery cause stp-loopback-guard
no boot host auto-config
no boot host auto-update
no bonjour enable
hostname PSW-K-01
no passwords complexity enable
passwords aging 0
username admin password encrypted 2bdd1322fd78e4df8d37249a406cd6e8b5359741 privilege 15
username cisco password encrypted 2bdd1322fd78e4df8d37249a406cd6e8b5359741 privilege 15
ip ssh server
snmp-server server
snmp-server location KELLER
snmp-server contact HOLZ
snmp-server community holz ro view Default
clock timezone DFL +1
clock summer-time web recurring eu
sntp server 134.130.4.17
sntp source-interface vlan 110
!
interface vlan 110
name MGMNT
ip address 172.20.32.231 255.255.224.0
no ip address dhcp
!
interface gigabitethernet1/1/1
switchport mode access
switchport access vlan 110
!
interface gigabitethernet1/1/12
channel-group 2 mode auto
!
interface gigabitethernet1/1/24
channel-group 2 mode auto
!
interface gigabitethernet1/1/25
channel-group 2 mode auto
!
interface gigabitethernet1/1/26
channel-group 2 mode auto
!
interface Port-channel2
loopback-detection enable
switchport trunk allowed vlan add 2-4,110,200,220,240,260,300,320
switchport trunk allowed vlan add 340,360
!
exit
ip default-gateway 172.20.32.1
encrypted ip ssh-client key rsa key-pair
And the last switch on the bottom
config-file-header
PSW-D-01
v1.4.11.5 / R800_NIK_1_4_220_026
CLI v1.0
set system mode switch
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
spanning-tree loopback-guard
spanning-tree priority 12288
bridge multicast filtering
vlan database
vlan 2-4,110,200,220,240,260,300,320,340,360
exit
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
loopback-detection enable
errdisable recovery interval 6000
errdisable recovery cause loopback-detection
errdisable recovery cause stp-bpdu-guard
errdisable recovery cause stp-loopback-guard
no boot host auto-config
no boot host auto-update
no bonjour enable
hostname PSW-D-01
no passwords complexity enable
passwords aging 0
username admin password encrypted 2bdd1322fd78e4df8d37249a406cd6e8b5359741 privilege 15
username cisco password encrypted 2bdd1322fd78e4df8d37249a406cd6e8b5359741 privilege 15
ip ssh server
snmp-server server
snmp-server location KELLER
snmp-server contact HOLZ
snmp-server community holz ro view Default
clock timezone DFL +1
clock summer-time web recurring eu
sntp server 134.130.4.17
sntp source-interface vlan 110
!
interface vlan 110
name MGMNT
ip address 172.20.32.232 255.255.224.0
no ip address dhcp
!
interface gigabitethernet1
loopback-detection enable
spanning-tree portfast
switchport mode access
switchport access vlan 110
!
interface gigabitethernet10
loopback-detection enable
spanning-tree portfast
!
interface gigabitethernet21
switchport trunk allowed vlan add 110
!
interface gigabitethernet27
channel-group 1 mode auto
!
interface gigabitethernet28
channel-group 1 mode auto
!
interface Port-channel1
loopback-detection enable
switchport trunk allowed vlan add 2-4,110,200,220,240,260,300,320
switchport trunk allowed vlan add 340,360
!
exit
encrypted ip ssh-client key rsa key-pair