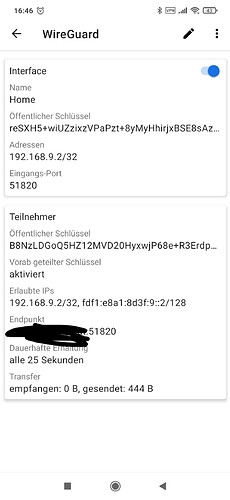
Hi,
I had OpenVPN successful running. then on upgrade to 21.02.0 r16279-5cc0535800 I bricked the device.
So I reflashed it by TFTP. Now all config is lost and I want to try wireguard server instead OpenVPN.
I used this guide:
But I can't connect to the server. The client send out the handshake but it never get returned. not from android mobile client, nor from windows client.
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2021.09.18 16:12:52 =~=~=~=~=~=~=~=~=~=~=~=
# Log and status
e]0;root@OpenWrt: /aroot@OpenWrt:/# logread -e vpn; netstat -l -n -p | grep -e "^udp\s.*\s-$"
Sat Sep 18 14:12:26 2021 daemon.notice netifd: Network device 'vpn' link is down
Sat Sep 18 14:12:26 2021 daemon.notice netifd: Interface 'vpn' is now down
Sat Sep 18 14:12:33 2021 daemon.notice netifd: Interface 'vpn' is setting up now
Sat Sep 18 14:12:39 2021 daemon.notice netifd: Interface 'vpn' is now up
Sat Sep 18 14:12:39 2021 daemon.notice netifd: Network device 'vpn' link is up
Sat Sep 18 14:12:40 2021 user.notice firewall: Reloading firewall due to ifup of vpn (vpn)
udp 0 0 0.0.0.0:51820 0.0.0.0:* -
udp 0 0 :::51820 :::* -
e]0;root@OpenWrt: /aroot@OpenWrt:/# pgrep -f -a wg; wg show; wg showconf vpn
8022 wg-crypt-vpn
e[0me[32me[1minterfacee[0m: e[32mvpne[0m
e[1mpublic keye[0m: wINoxeNhmHOC8qsty7HWU0E6EcpD2eKE9Q/J2Dm9WBw=
e[1mprivate keye[0m: (hidden)
e[1mlistening porte[0m: 51820
e[33me[1mpeere[0m: e[33mB8NzLDGoQ5HZ12MVD20HyxwjP68e+R3ErdpPG2gZpXo=e[0m
e[1mpreshared keye[0m: (hidden)
e[1mendpointe[0m: 194.x.x.103:51820
e[1mallowed ipse[0m: 192.168.9.2e[36m/e[0m32, fdf1:e8a1:8d3f:9::2e[36m/e[0m128
e[1mtransfere[0m: 0 e[36mBe[0m received, 740 e[36mBe[0m sent
e[1mpersistent keepalivee[0m: every 25 e[36msecondse[0m
[Interface]
ListenPort = 51820
PrivateKey = ePkikYBGmqI2da36g9z2ZxTyLRgTMOyhgCz/yhlJnkU=
[Peer]
PublicKey = B8NzLDGoQ5HZ12MVD20HyxwjP68e+R3ErdpPG2gZpXo=
PresharedKey = USIWiupHj+Yy+JMJG3txtCwf1G+AttdvzHXmWVoRmyk=
AllowedIPs = 192.168.9.2/32, fdf1:e8a1:8d3f:9::2/128
Endpoint = 194.x.x.103:51820
PersistentKeepalive = 25
e]0;root@OpenWrt: /aroot@OpenWrt:/# ip address show; ip route show table all
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
link/ether 6c:b0:ce:1b:95:da brd ff:ff:ff:ff:ff:ff
inet6 fe80::6eb0:ceff:fe1b:95da/64 scope link
valid_lft forever preferred_lft forever
11: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 6c:b0:ce:1b:95:da brd ff:ff:ff:ff:ff:ff
inet6 fe80::6eb0:ceff:fe1b:95da/64 scope link
valid_lft forever preferred_lft forever
15: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 6c:b0:ce:1b:95:db brd ff:ff:ff:ff:ff:ff
inet 194.x.x.103/27 brd 194.x.x.127 scope global eth0.2
valid_lft forever preferred_lft forever
inet6 fe80::6eb0:ceff:fe1b:95db/64 scope link
valid_lft forever preferred_lft forever
24: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 6c:b0:ce:1b:95:da brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fdc9:5bf2:c819::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::6eb0:ceff:fe1b:95da/64 scope link
valid_lft forever preferred_lft forever
25: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 6c:b0:ce:1b:95:da brd ff:ff:ff:ff:ff:ff
26: vpn: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 192.168.9.1/24 brd 192.168.9.255 scope global vpn
valid_lft forever preferred_lft forever
inet6 fdf1:e8a1:8d3f:9::1/64 scope global
valid_lft forever preferred_lft forever
27: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 6c:b0:ce:1b:95:dc brd ff:ff:ff:ff:ff:ff
inet6 fe80::6eb0:ceff:fe1b:95dc/64 scope link
valid_lft forever preferred_lft forever
28: wlan0-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 6e:b0:ce:1b:95:da brd ff:ff:ff:ff:ff:ff
inet6 fe80::6cb0:ceff:fe1b:95da/64 scope link
valid_lft forever preferred_lft forever
default via 194.x.x.97 dev eth0.2 src 194.x.x.103
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.9.0/24 dev vpn scope link src 192.168.9.1
192.168.9.2 dev vpn scope link
194.x.x.96/27 dev eth0.2 scope link src 194.x.x.103
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
broadcast 192.168.9.0 dev vpn table local scope link src 192.168.9.1
local 192.168.9.1 dev vpn table local scope host src 192.168.9.1
broadcast 192.168.9.255 dev vpn table local scope link src 192.168.9.1
broadcast 194.x.x.96 dev eth0.2 table local scope link src 194.x.x.103
local 194.x.x.103 dev eth0.2 table local scope host src 194.x.x.103
broadcast 194.x.x.127 dev eth0.2 table local scope link src 194.x.x.103
fdc9:5bf2:c819::/64 dev br-lan metric 1024
unreachable fdc9:5bf2:c819::/48 dev lo metric 2147483647
fdf1:e8a1:8d3f:9::2 dev vpn metric 1024
fdf1:e8a1:8d3f:9::/64 dev vpn metric 256
fe80::/64 dev eth0 metric 256
fe80::/64 dev eth0.2 metric 256
fe80::/64 dev br-lan metric 256
fe80::/64 dev wlan1 metric 256
fe80::/64 dev wlan0 metric 256
fe80::/64 dev wlan0-1 metric 256
local ::1 dev lo table local metric 0
anycast fdc9:5bf2:c819:: dev br-lan table local metric 0
local fdc9:5bf2:c819::1 dev br-lan table local metric 0
anycast fdf1:e8a1:8d3f:9:: dev vpn table local metric 0
local fdf1:e8a1:8d3f:9::1 dev vpn table local metric 0
anycast fe80:: dev eth0.2 table local metric 0
anycast fe80:: dev eth0 table local metric 0
anycast fe80:: dev br-lan table local metric 0
anycast fe80:: dev wlan1 table local metric 0
anycast fe80:: dev wlan0 table local metric 0
anycast fe80:: dev wlan0-1 table local metric 0
local fe80::6cb0:ceff:fe1b:95da dev wlan0-1 table local metric 0
local fe80::6eb0:ceff:fe1b:95da dev eth0 table local metric 0
local fe80::6eb0:ceff:fe1b:95da dev br-lan table local metric 0
local fe80::6eb0:ceff:fe1b:95da dev wlan0 table local metric 0
local fe80::6eb0:ceff:fe1b:95db dev eth0.2 table local metric 0
local fe80::6eb0:ceff:fe1b:95dc dev wlan1 table local metric 0
multicast ff00::/8 dev eth0 table local metric 256
multicast ff00::/8 dev eth0.2 table local metric 256
multicast ff00::/8 dev br-lan table local metric 256
multicast ff00::/8 dev wlan1 table local metric 256
multicast ff00::/8 dev vpn table local metric 256
multicast ff00::/8 dev wlan0 table local metric 256
multicast ff00::/8 dev wlan0-1 table local metric 256
e]0;root@OpenWrt: /aroot@OpenWrt:/# ip rule show; iptables-save -c
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
# Generated by iptables-save v1.8.7 on Sat Sep 18 14:13:05 2021
*nat
:PREROUTING ACCEPT [100:37488]
:INPUT ACCEPT [1:328]
:OUTPUT ACCEPT [49:3863]
:POSTROUTING ACCEPT [5:600]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[100:37488] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[96:37243] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i vpn -m comment --comment "!fw3" -j zone_lan_prerouting
[4:245] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[78:5277] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1:328] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o vpn -m comment --comment "!fw3" -j zone_lan_postrouting
[73:4677] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[1:328] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.7/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: WEB_443 (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.9.0/24 -d 192.168.1.7/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: WEB_443 (reflection)" -j SNAT --to-source 192.168.9.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.7/32 -p tcp -m tcp --dport 81 -m comment --comment "!fw3: WEB_80 (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.9.0/24 -d 192.168.1.7/32 -p tcp -m tcp --dport 81 -m comment --comment "!fw3: WEB_80 (reflection)" -j SNAT --to-source 192.168.9.1
[96:37243] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 194.x.x.103/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: WEB_443 (reflection)" -j DNAT --to-destination 192.168.1.7:443
[0:0] -A zone_lan_prerouting -s 192.168.9.0/24 -d 194.x.x.103/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: WEB_443 (reflection)" -j DNAT --to-destination 192.168.1.7:443
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 194.x.x.103/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: WEB_80 (reflection)" -j DNAT --to-destination 192.168.1.7:81
[0:0] -A zone_lan_prerouting -s 192.168.9.0/24 -d 194.x.x.103/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: WEB_80 (reflection)" -j DNAT --to-destination 192.168.1.7:81
[73:4677] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[73:4677] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[4:245] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 443 -m comment --comment "!fw3: WEB_443" -j DNAT --to-destination 192.168.1.7:443
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 80 -m comment --comment "!fw3: WEB_80" -j DNAT --to-destination 192.168.1.7:81
COMMIT
# Completed on Sat Sep 18 14:13:05 2021
# Generated by iptables-save v1.8.7 on Sat Sep 18 14:13:05 2021
*mangle
:PREROUTING ACCEPT [677:226343]
:INPUT ACCEPT [139:11570]
:FORWARD ACCEPT [468:179112]
:OUTPUT ACCEPT [183:27456]
:POSTROUTING ACCEPT [629:205688]
[14:688] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[11:540] -A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Sep 18 14:13:05 2021
# Generated by iptables-save v1.8.7 on Sat Sep 18 14:13:05 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[21:2485] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[120:9386] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[97:7627] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[2:80] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[1:328] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i vpn -m comment --comment "!fw3" -j zone_lan_input
[22:1431] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[468:179112] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[437:177618] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[31:1494] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i vpn -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[21:2485] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[166:26132] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[105:21901] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1:328] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o vpn -m comment --comment "!fw3" -j zone_lan_output
[60:3903] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[22:1431] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[2:80] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[1:328] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_dest_ACCEPT -o vpn -m comment --comment "!fw3" -j ACCEPT
[31:1494] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[31:1494] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[1:328] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[1:328] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[1:328] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[1:328] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[1:328] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_src_ACCEPT -i vpn -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[22:880] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[69:4517] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[22:1431] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -p udp -m udp --sport 51820 -m comment --comment "!fw3: Allow-WireGuard" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[22:1431] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[60:3903] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[60:3903] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[22:1431] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Sep 18 14:13:05 2021
e]0;root@OpenWrt: /aroot@OpenWrt:/# ip -6 rule show; ip6tables-save -c
0: from all lookup local
32766: from all lookup main
4200000001: from all iif lo lookup unspec 12
4200000015: from all iif eth0.2 lookup unspec 12
4200000024: from all iif br-lan lookup unspec 12
4200000026: from all iif vpn lookup unspec 12
# Generated by ip6tables-save v1.8.7 on Sat Sep 18 14:13:06 2021
*mangle
:PREROUTING ACCEPT [111:33705]
:INPUT ACCEPT [82:13102]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [111:20127]
:POSTROUTING ACCEPT [113:20231]
[0:0] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Sep 18 14:13:06 2021
# Generated by ip6tables-save v1.8.7 on Sat Sep 18 14:13:06 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [20:1852]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[45:9865] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[37:3237] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[22:2030] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[13:1103] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i vpn -m comment --comment "!fw3" -j zone_lan_input
[2:104] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[0:0] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i vpn -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[45:9865] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[66:10262] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[31:7142] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[11:864] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o vpn -m comment --comment "!fw3" -j zone_lan_output
[4:404] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp6-port-unreachable
[0:0] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[11:864] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_dest_ACCEPT -o vpn -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[13:1103] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[13:1103] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[11:864] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[11:864] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[13:1103] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_src_ACCEPT -i vpn -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[4:404] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 128 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 129 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 2 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 3 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 4/0 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 4/1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[2:104] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -s fc00::/6 -d fc00::/6 -p udp -m udp --dport 546 -m comment --comment "!fw3: Allow-DHCPv6" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 130/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 131/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 132/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 143/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 128 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 129 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 2 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 3 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 4/0 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 4/1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[2:104] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 133 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 135 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 134 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 136 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p udp -m udp --sport 51820 -m comment --comment "!fw3: Allow-WireGuard" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[4:404] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[4:404] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Sep 18 14:13:06 2021
e]0;root@OpenWrt: /aroot@OpenWrt:/# uci show network; uci show firewall; crontab -l
network.loopback=interface
network.loopback.device='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdc9:5bf2:c819::/48'
network.@device[0]=device
network.@device[0].name='br-lan'
network.@device[0].type='bridge'
network.@device[0].ports='eth0.1'
network.lan=interface
network.lan.device='br-lan'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.@device[1]=device
network.@device[1].name='eth0.2'
network.@device[1].macaddr='6c:b0:ce:1b:95:db'
network.wan=interface
network.wan.device='eth0.2'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.device='eth0.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='1 2 3 4 0t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='5 0t'
network.vpn=interface
network.vpn.proto='wireguard'
network.vpn.private_key='ePkikYBGmqI2da36g9z2ZxTyLRgTMOyhgCz/yhlJnkU='
network.vpn.listen_port='51820'
network.vpn.addresses='192.168.9.1/24' 'fdf1:e8a1:8d3f:9::1/64'
network.wgclient=wireguard_vpn
network.wgclient.public_key='B8NzLDGoQ5HZ12MVD20HyxwjP68e+R3ErdpPG2gZpXo='
network.wgclient.preshared_key='USIWiupHj+Yy+JMJG3txtCwf1G+AttdvzHXmWVoRmyk='
network.wgclient.allowed_ips='192.168.9.2/32' 'fdf1:e8a1:8d3f:9::2/128'
network.wgclient.endpoint_host='my.dns.at'
network.wgclient.description='Note 8'
network.wgclient.route_allowed_ips='1'
network.wgclient.endpoint_port='51820'
network.wgclient.persistent_keepalive='25'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.lan=zone
firewall.lan.name='lan'
firewall.lan.input='ACCEPT'
firewall.lan.output='ACCEPT'
firewall.lan.forward='ACCEPT'
firewall.lan.network='lan' 'vpn'
firewall.wan=zone
firewall.wan.name='wan'
firewall.wan.input='REJECT'
firewall.wan.output='ACCEPT'
firewall.wan.forward='REJECT'
firewall.wan.masq='1'
firewall.wan.mtu_fix='1'
firewall.wan.network='wan' 'wan6'
firewall.lan_wan=forwarding
firewall.lan_wan.src='lan'
firewall.lan_wan.dest='wan'
....
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].name='WEB_443'
firewall.@redirect[0].proto='tcp'
firewall.@redirect[0].src='wan'
firewall.@redirect[0].src_dport='443'
firewall.@redirect[0].dest='lan'
firewall.@redirect[0].dest_ip='192.168.1.7'
firewall.@redirect[0].dest_port='443'
firewall.@redirect[1]=redirect
firewall.@redirect[1].target='DNAT'
firewall.@redirect[1].name='WEB_80'
firewall.@redirect[1].proto='tcp'
firewall.@redirect[1].src='wan'
firewall.@redirect[1].src_dport='80'
firewall.@redirect[1].dest='lan'
firewall.@redirect[1].dest_ip='192.168.1.7'
firewall.@redirect[1].dest_port='81'
firewall.@rule[10]=rule
firewall.@rule[10].name='Allow-WireGuard'
firewall.@rule[10].proto='udp'
firewall.@rule[10].src='wan'
firewall.@rule[10].src_port='51820'
firewall.@rule[10].target='ACCEPT'
crontab: can't open 'root': No such file or directory
e]0;root@OpenWrt: /aroot@OpenWrt:/#
I do not find the reason why it can not connect to the server.
I can ping my DNS and it shows me the correct IP.
Anyone a idea?