This Youtube description of the firewall settings in LuCI is very helpful; it helps to understand the zone logic of the GUI.
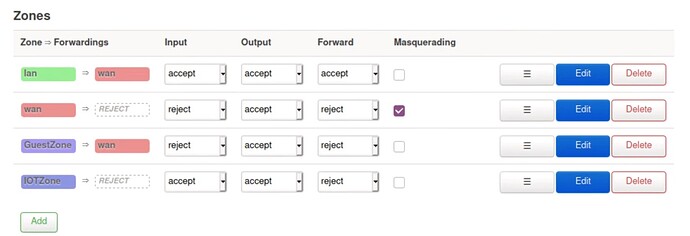
However, the author's explanation of the "forward" parameter did not convince me. For him, in LuCI, it doesn't matter if "forward" is set to "accept" or "reject/drop", because it only opens or closes traffic between vlans gathered under the same zone, but does not necessarily block traffic between vlans in different zones.
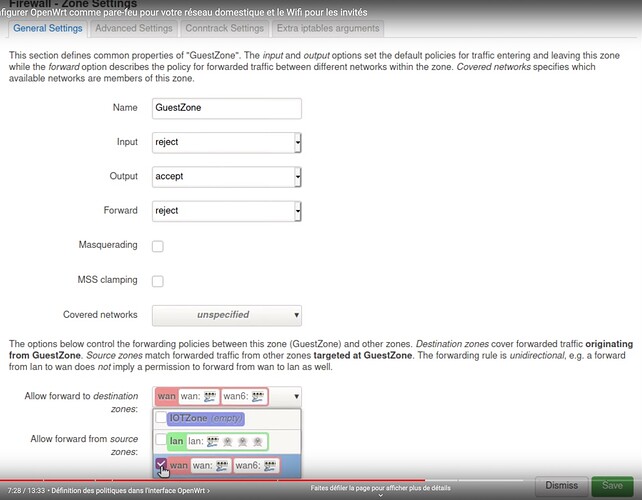
So for example, according to the screens he shows, for his "guest" vlan he leaves "forward" on "reject", even though he wants "guest" to be able to exit to the "wan" internet. And he says it works.
It seems counter-intuitive, and on a similar configuration, with LuCI 21.252, I couldn't reproduce this operation: on the contrary, in my case, as soon as "forward" is set to "reject", the vlan is isolated, even though in the left part of the screen you would have correctly defined the name of the other vlan(s) to which the forwarding would be desired.
Each of the links to the video has a different timecode.
Is he trying to explain a subtlety I'm missing, or is it a mistake in his presentation?
The search engine that suggests discussions similar to the content of the post being written is very effective. This post seems to answer my question. I'll have to test it again to make me convinced that I'm getting the same result.
In practice, if we have several machines in the DMZ, each in its vlan, and we want to prohibit dialogue between them, there is no need to create a different zone for each vlan, it is enough to apply the same zone to all the interfaces attached to these vlans, and to select "forward" "reject" ?