To avoid locking yourself out, connect over WiFi while you are working on the switch config.
Add a WiFi SSID connected to your management interface if necessary.
This means you likely want to set all VLANs as tagged on the WAN port (except VLAN 2 perhaps, which is the ISP uplink on your main router).
Please don't try to set up the WAN connector as a dedicated maintenance port and as a multi-VLAN uplink at the same time.
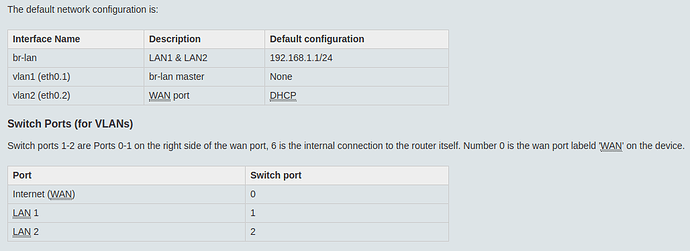
Let me try to explain the relationship between the IP address and the physical ethernet socket:
- The IP address is assigned to a "logical" interface as set up in LuCI. This logical (OpenWrt) interface is connected to a VLAN by specifying a Linux interface name like
eth0.1 in "Physical Settings".
- The external ethernet connectors (ports) are also connected to VLANs, this time in the switch config.
Despite the identical name, the logical WAN interface in LuCI is completely different from the WAN connector on the device enclosure and in the switch config.
You should do the following on the AP:
- Decide on a VLAN ID as your maintenance VLAN, which is separate from all VLANs used by ordinary clients.
- Dedicate a logical interface for maintenance, and assign to it a static IP address from a separate subnet. This could be the default LAN interface or a new interface created by you. However, It must not be used by ordinary clients. The default WAN interface is unsuitable for maintenance access unless you also adjust the firewall.
- Connect the interface to the VLAN by specifying the "physical interface" as eth0.1, or whatever your chosen VLAN ID is.
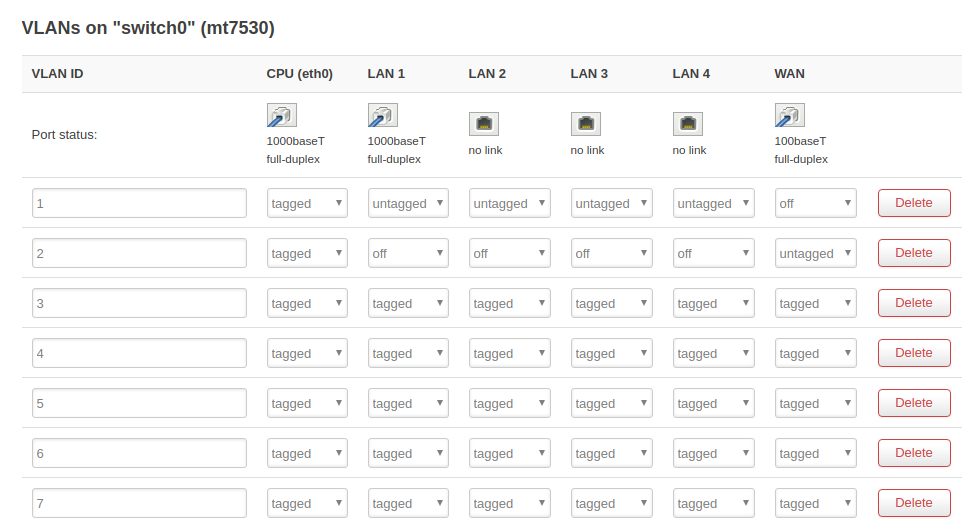
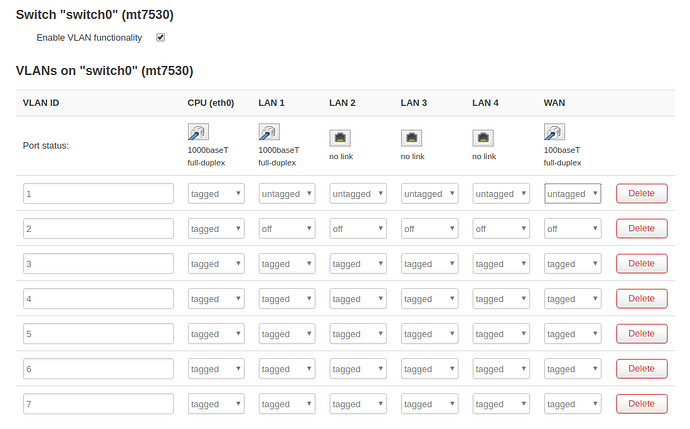
- In the switch config, set the VLAN as "tagged" on the WAN ethernet connector. This allows your admin PC to be connected to the main router and still be able to manage the AP. A matching config on the main router and the switch is needed to make this work.
To enable access to this maintenance VLAN and interface from your admin PC, do one or more of the following:
- In the AP's switch config, set one of the LANx ports to carry the maintenance VLAN untagged, and no other VLAN. You can plug your admin PC into this port for AP maintenance.
- Do the same, but on your main router.
Also make sure it knows about the tagged maintenance VLAN on the other port which is connected to the AP. The same applies to the managed switch in between.
- Create a WiFi SSID and specify your maintenance interface as the network.
Be sure to use tagged VLANs on all the links between router, switch and access point.
User-facing ports should be untagged.
A port can carry either a single untagged VLAN, or multiple tagged VLANs.
Although some devices can mix tagged and untagged VLANs on a port, don't try this here,
it might even be the cause of the problems we are discussing.
As I learnt in a previous thread, VLAN 2 is the ISP uplink on your main router. Don't use it anywhere else; choose a different ID for the maintenance VLAN. Since you are using VLAN tagging between devices, each VLAN ID has a single purpose across all the devices involved and must not be reused for something else.
By the way, please don't start a new thread if your question still fits the topic of an existing thread,
because newcomers will miss out on the information given previously. At least, link to the previous discussion. For a new topic, opening a new thread is fine (and recommended).
If the discussion stalls, wait a couple of days and check carefully if you answered all the questions that you were asked.