Please correct me if I'm wrong... but I believe that this is actually what you want (at least long term) -- the Pi itself should not be possible to reach on VLAN 101 -- by this, I mean that you will not be able to administer the Pi on this VLAN. Internet will still route though the Pi, even if you are unable to ping the Pi (or use ssh or LuCI).
Management of the Pi happens on VLAN 1 with 192.168.100.13.
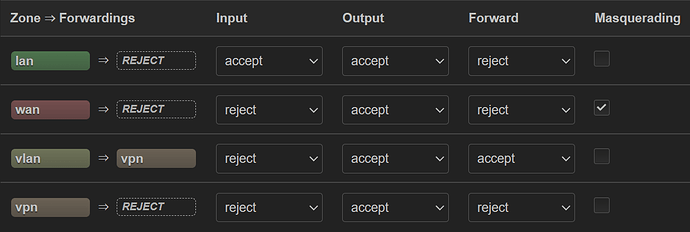
You can verify this by connecting your computer to port 1 and manually assigning the IP address info as you had done previously. You should be unable to reach the Pi itself, but you should be able to reach the internet with no issue (assuming you have the firewall forwarding setup to allow lan > wan forwarding and that the WG connection is disabled (for now).
Then, set your computer to DHCP and plug into port 2 -- you should be able to access the pi (192.168.100.13) for administrative purposes (ping, ssh, LuCI). Your internet traffic will go through the USG and probably via WAN1.
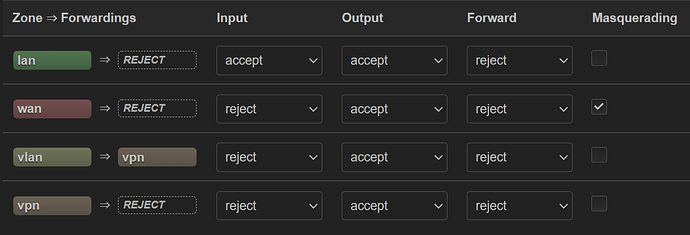
This is expected behavior. This was intended to get internet connectivity (bypassing the WG VPN which may not be working properly), to prove that your VLANs are configured properly and that your Pi is routing in general. The forwarding has nothing to do with the 192.168.101.0/24 network's ability to access the Pi (it is the zone "input" rule which controls this aspect).
Yes, entirely expected. You don't need to be able to "see" the Pi in order to route through it (I know, it seems strange). VLAN 101's connection to the USG is via the USG's WAN2. Because of this, the USG treats the network as untrusted... so the fact that you can't "see" it is fine... as long as it can ping out to the internet, it doesn't matter if the USG can be "seen" from your computer (or the Pi) and it doesn't matter if it can "see" the pi from its own interface.
I am pretty sure you want to have input=drop or reject in the long term. But if it makes it easier for you to troubleshoot for now, you can set that vlan zone input rule to accept. Once everything is actually working, you'll see that you can change it to drop/reject and the internet will still work as expected.
Back to WG -- I think your WG connection is not working properly. Since you now know that allowing forwarding from vlan > wan allows normal internet connectivity via the Pi, the remaining question is about the WG connection. So... setup WG on your phone or computer with the parameters from the Pi. Make sure the Pi's WG interface is stopped, and then connect using your phone/computer and see if you get proper connectivity. If you don't, that would likely explain the earlier problems.