MIRC0
January 6, 2021, 7:09pm
1
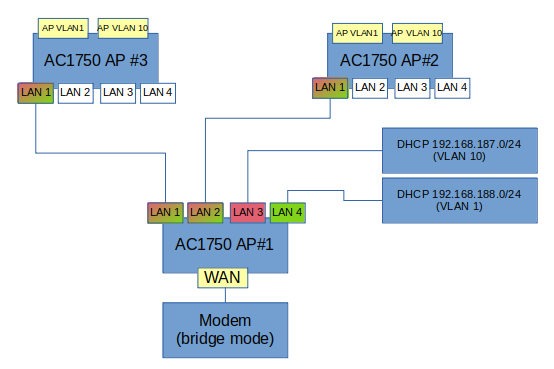
Hi there, since there are some experienced people reading here I'd like to take my chance #1 to also act as dhcp server. here is a drawing#2 / #3 to act as ap without dhcpd (there should be only one).#1 , did not work.
is it a good idea to set my iot net up like this?
how would I manage to share ap#1 dhcp for 192.168.187.0/24 with the other ap?
Thank you,
MIRC0
January 7, 2021, 7:26am
3
OK great, so the only difference would be that my existing DHCP server would serve two networks. Thought this would only be possible when this server had two interfaces which is not the case. Or should I simply add a second raspberry pi and add it to the network serving 192.168.187.0/24?
trendy
January 7, 2021, 10:21am
4
A vlan subinterface is still a separate interface.
1 Like
MIRC0
January 7, 2021, 6:32pm
5
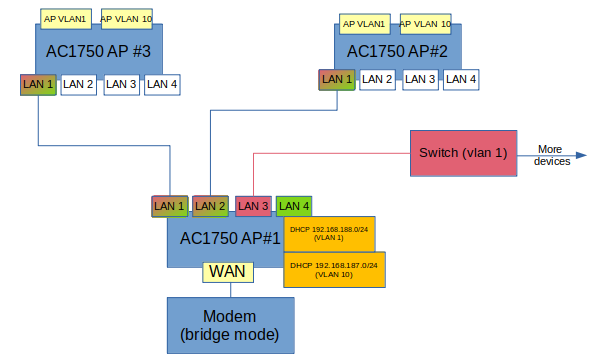
thank you very much. Is this the right way to set it up?
trendy
January 7, 2021, 9:14pm
6
It is correct, however you don't need the DHCP servers as separate devices. You can run them on AP1.
1 Like
MIRC0
January 8, 2021, 8:16am
7
Is there documentation for unmanaged interfaces being available? I could not find any, but have some problems understanding the concept behind this.#1 having a DHCP server connected to an interface which clings to the same vlan ID?
trendy
January 8, 2021, 9:53am
8
Unmanaged interface doesn't have IP/mask/gw. It is an alternative protocol compared to static or dhcp.
You don't pass it via 188.0, it is a different vlan and the port lan1 of AP1 and AP3 are trunk, tagging both vlans 1 and 10.
MIRC0
January 8, 2021, 10:34am
9
interfaces not having those usual network setting simply transport all traffic? it's just arbitrary traffic being tagged and therefore being manageable via vlan tag? never met those kind of interface protocols, sry for asking.
yes, read this already. tricky thing when doing this the first time
trendy
January 8, 2021, 11:08am
10
With unmanaged protocol you omit the IP settings. You can still assign the interface to a firewall zone though to control the traffic.
MIRC0:
so, there is a device connecting to AP#2 via wireless device being connected to an unmanaged interface which is bound on LAN1 being tagged on vlan id 10. on AP#1 there then is a managed interface (static address though) running a dhcp server being bound on LAN3 which is untagged for vlan id 10. correct?
Create a new interface called "test", unmanaged protocol, and physical interface enter eth0.10 at the bottom field manually (press enter for confirmation). Create an SSID "test" with the settings you wish and assign it to test interface. Then in switch configuration create vlan 10, assign it to CPU tagged, port lan1 tagged and off everywhere else.
MIRC0
January 9, 2021, 11:55am
11
I have this 3 ap setup running with 2 vlans (id 1 and id 10). those are supposed to be separated so that vlan id 10 may not access internet or vlan id 1 devices. I want to be able to use firewall traffic rules to enable specific access from 10 to 1. However, right now, my devices from vlan 10 may access everything. I dont see why.
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdf4:54f0:9a05::/48'
network.lan=interface
network.lan.proto='static'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.ifname='eth0.1'
network.lan.type='bridge'
network.lan.ipaddr='192.168.188.1'
network.wan=interface
network.wan.ifname='eth0.2'
network.wan.proto='dhcp'
network.wan_eth0_2_dev=device
network.wan_eth0_2_dev.name='eth0.2'
network.wan_eth0_2_dev.macaddr='3c:84:6a:aa:48:f4'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0t 2 3 4t 5t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].vid='2'
network.@switch_vlan[1].ports='0t 1'
network.WAN6=interface
network.WAN6.ifname='eth0.2'
network.WAN6.proto='dhcpv6'
network.WAN6.reqaddress='try'
network.WAN6.reqprefix='auto'
network.iot=interface
network.iot.proto='static'
network.iot.ifname='eth0.10'
network.iot.ipaddr='192.168.187.1'
network.iot.netmask='255.255.255.0'
network.@switch_vlan[2]=switch_vlan
network.@switch_vlan[2].device='switch0'
network.@switch_vlan[2].vlan='3'
network.@switch_vlan[2].vid='10'
network.@switch_vlan[2].ports='0t 4t 5t'
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].forward='ACCEPT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].masq='1'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[1].network='wan'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@rule[9]=rule
firewall.@rule[9].src='lan'
firewall.@rule[9].name='lan2wan'
firewall.@rule[9].dest='wan'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[9].proto='all'
firewall.@zone[2]=zone
firewall.@zone[2].name='iot'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].network='iot'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].masq='1'
firewall.@zone[3]=zone
firewall.@zone[3].name='lan2iot'
firewall.@zone[3].input='ACCEPT'
firewall.@zone[3].forward='REJECT'
firewall.@zone[3].masq='1'
firewall.@zone[3].output='ACCEPT'
firewall.@rule[10]=rule
firewall.@rule[10].src='iot'
firewall.@rule[10].name='Iot ping'
firewall.@rule[10].target='ACCEPT'
firewall.@rule[10].proto='icmp'
firewall.@rule[10].enabled='0'
firewall.@rule[11]=rule
firewall.@rule[11].src='lan'
firewall.@rule[11].name='LAN2IOT - ICMP'
firewall.@rule[11].dest='iot'
firewall.@rule[11].target='ACCEPT'
firewall.@rule[11].proto='icmp'
firewall.@rule[12]=rule
firewall.@rule[12].src_port='80'
firewall.@rule[12].src='iot'
firewall.@rule[12].name='IN - IOTSERVER'
firewall.@rule[12].dest='lan'
firewall.@rule[12].dest_ip='192.168.188.3'
firewall.@rule[12].target='ACCEPT'
firewall.@rule[12].dest_port='80'
firewall.@rule[12].enabled='0'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.channel='36'
wireless.radio0.hwmode='11a'
wireless.radio0.path='pci0000:00/0000:00:00.0'
wireless.radio0.htmode='VHT80'
wireless.default_radio0=wifi-iface
wireless.default_radio0.device='radio0'
wireless.default_radio0.mode='ap'
wireless.default_radio0.network='lan'
wireless.default_radio0.key='XXXXXXX'
wireless.default_radio0.encryption='psk2'
wireless.default_radio0.ssid='MiTiAir5'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.channel='11'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/ahb/18100000.wmac'
wireless.radio1.htmode='HT20'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.mode='ap'
wireless.default_radio1.key='XXXXXXX'
wireless.default_radio1.ssid='MiTiAirIoT'
wireless.default_radio1.encryption='psk2'
wireless.wifinet2=wifi-iface
wireless.wifinet2.ssid='MiTiAir'
wireless.wifinet2.encryption='psk2'
wireless.wifinet2.device='radio1'
wireless.wifinet2.mode='ap'
wireless.wifinet2.network='lan'
wireless.wifinet2.key='XXXXX'
AP#2
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fda8:bb03:043e::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ip6assign='60'
network.lan.gateway='192.168.188.1'
network.lan.dns='192.168.188.2'
network.lan.ipaddr='192.168.188.12/24'
network.wan_eth0_2_dev=device
network.wan_eth0_2_dev.name='eth0.2'
network.wan_eth0_2_dev.macaddr='1c:3b:f3:4f:dc:78'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0t 2t 3 4'
network.iot=interface
network.iot.type='bridge'
network.iot.ifname='eth0.10'
network.iot.proto='none'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].vid='10'
network.@switch_vlan[1].ports='0t 2t'
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].forward='ACCEPT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[0].masq='1'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[1]=zone
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].name='iot'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].network='iot'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11a'
wireless.radio0.path='pci0000:00/0000:00:00.0'
wireless.radio0.htmode='VHT80'
wireless.radio0.channel='48'
wireless.radio0.country='DE'
wireless.radio0.txpower='23'
wireless.default_radio0=wifi-iface
wireless.default_radio0.device='radio0'
wireless.default_radio0.network='lan'
wireless.default_radio0.mode='ap'
wireless.default_radio0.key='XXXXX'
wireless.default_radio0.encryption='psk2'
wireless.default_radio0.ssid='MiTiAir5'
wireless.default_radio0.ifname='wlan5'
wireless.default_radio0.wmm='0'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/ahb/18100000.wmac'
wireless.radio1.htmode='HT20'
wireless.radio1.country='DE'
wireless.radio1.txpower='20'
wireless.radio1.channel='7'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.network='lan'
wireless.default_radio1.mode='ap'
wireless.default_radio1.key='XXXXXX'
wireless.default_radio1.encryption='psk2'
wireless.default_radio1.ssid='MiTiAir'
wireless.default_radio1.ifname='wlan24'
wireless.default_radio1.wmm='0'
wireless.iot=wifi-iface
wireless.iot.device='radio1'
wireless.iot.mode='ap'
wireless.iot.network='iot'
wireless.iot.ssid='MiTiAirIoT'
wireless.iot.encryption='psk2'
wireless.iot.key='XXXXXX'
Thank you very very much for throwing a hint
trendy
January 9, 2021, 2:18pm
12
On AP2 iot firewall zone has no point. Also remove masquerade from lan zone.
Don't use device, assign to network instead.
MIRC0
January 10, 2021, 6:54pm
13
Thank you trendy, most of this was left overs from playing around. I corrected all but still my iot net has access to the internet. There is no DNS server being provided in that net, so, half way done. But still I can get trough icmp packages e.g. to 8.8.8.8.I steamed it all down down AP#1. first time my fault was, that I did not set any gw for my iot net (vid 10), so the router set my WAN IP as default. I simply set in something wrong but still, iot traffic makes its way through.
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdf4:54f0:9a05::/48'
network.lan=interface
network.lan.proto='static'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.ifname='eth0.1'
network.lan.type='bridge'
network.lan.ipaddr='192.168.188.1'
network.wan=interface
network.wan.ifname='eth0.2'
network.wan.proto='dhcp'
network.wan_eth0_2_dev=device
network.wan_eth0_2_dev.name='eth0.2'
network.wan_eth0_2_dev.macaddr='3c:84:6a:aa:48:f4'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0t 2 3 4t 5t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].vid='2'
network.@switch_vlan[1].ports='0t 1'
network.WAN6=interface
network.WAN6.ifname='eth0.2'
network.WAN6.proto='dhcpv6'
network.WAN6.reqaddress='try'
network.WAN6.reqprefix='auto'
network.iot=interface
network.iot.proto='static'
network.iot.ifname='eth0.10'
network.iot.ipaddr='192.168.187.1'
network.iot.netmask='255.255.255.0'
network.iot.type='bridge'
network.iot.gateway='192.168.187.0'
network.@switch_vlan[2]=switch_vlan
network.@switch_vlan[2].device='switch0'
network.@switch_vlan[2].vlan='3'
network.@switch_vlan[2].vid='10'
network.@switch_vlan[2].ports='0t 4t 5t'
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].forward='ACCEPT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].network='wan'
firewall.@zone[1].forward='REJECT'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[1].enabled='0'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[5].enabled='0'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].name='iot'
firewall.@zone[2].network='iot'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].src='iot'
firewall.@rule[9].name='Iot ping'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[9].proto='icmp'
firewall.@rule[9].enabled='0'
firewall.@rule[10]=rule
firewall.@rule[10].src='lan'
firewall.@rule[10].name='LAN2IOT - ICMP'
firewall.@rule[10].dest='iot'
firewall.@rule[10].target='ACCEPT'
firewall.@rule[10].proto='icmp'
firewall.@rule[11]=rule
firewall.@rule[11].src_port='80'
firewall.@rule[11].src='iot'
firewall.@rule[11].name='IN - IOTSERVER'
firewall.@rule[11].dest_ip='192.168.188.3'
firewall.@rule[11].target='ACCEPT'
firewall.@rule[11].enabled='0'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.channel='36'
wireless.radio0.hwmode='11a'
wireless.radio0.path='pci0000:00/0000:00:00.0'
wireless.radio0.htmode='VHT80'
wireless.default_radio0=wifi-iface
wireless.default_radio0.device='radio0'
wireless.default_radio0.mode='ap'
wireless.default_radio0.network='lan'
wireless.default_radio0.key='XXXX!'
wireless.default_radio0.encryption='psk2'
wireless.default_radio0.ssid='MiTiAir5'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.channel='11'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/ahb/18100000.wmac'
wireless.radio1.htmode='HT20'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.mode='ap'
wireless.default_radio1.key='XXXX'
wireless.default_radio1.ssid='MiTiAirIoT'
wireless.default_radio1.encryption='psk2'
wireless.default_radio1.network='iot'
wireless.wifinet2=wifi-iface
wireless.wifinet2.ssid='MiTiAir'
wireless.wifinet2.encryption='psk2'
wireless.wifinet2.device='radio1'
wireless.wifinet2.mode='ap'
wireless.wifinet2.network='lan'
wireless.wifinet2.key='XXXX'
Any other idea what might be missing here? For sure, I used correct WiFi and got a correct ip address from 187.0 net.
Btw I do not know what you mean with
wireless.default_radio0.device='radio0' and using network instead. Radio1 is a device, I cannot change that with a network, cant I? However, there is a network connected... lan and iot.
Thank you,
trendy
January 10, 2021, 8:25pm
14
Ignore that, my mistake.iptables-save -c to check the firewall.
MIRC0
January 10, 2021, 9:12pm
15
# Generated by iptables-save v1.8.3 on Sun Jan 10 21:11:33 2021
*nat
:PREROUTING ACCEPT [21991:2967431]
:INPUT ACCEPT [2622:204619]
:OUTPUT ACCEPT [11450:720469]
:POSTROUTING ACCEPT [3007:200779]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_iot_postrouting - [0:0]
:zone_iot_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[21991:2967431] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[20050:2823268] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[1678:122121] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[263:22042] -A PREROUTING -i br-iot -m comment --comment "!fw3" -j zone_iot_prerouting
[16250:1081061] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[139:14920] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[13243:880282] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o br-iot -m comment --comment "!fw3" -j zone_iot_postrouting
[139:14920] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[20050:2823268] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[13243:880282] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[13243:880282] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[1678:122121] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sun Jan 10 21:11:33 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 21:11:33 2021
*mangle
:PREROUTING ACCEPT [4918910:4377726081]
:INPUT ACCEPT [1762568:1618507934]
:FORWARD ACCEPT [3141773:2756815927]
:OUTPUT ACCEPT [1475139:1490131952]
:POSTROUTING ACCEPT [4616706:4246938931]
[1734:104292] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[1694:100632] -A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sun Jan 10 21:11:33 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 21:11:33 2021
*filter
:INPUT ACCEPT [1176:47961]
:FORWARD ACCEPT [2106:360285]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_iot_dest_ACCEPT - [0:0]
:zone_iot_forward - [0:0]
:zone_iot_input - [0:0]
:zone_iot_output - [0:0]
:zone_iot_src_ACCEPT - [0:0]
:zone_lan2iot_forward - [0:0]
:zone_lan2iot_input - [0:0]
:zone_lan2iot_output - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_ACCEPT - [0:0]
[17611:1655099] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[1744964:1616853199] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[1740593:1616553085] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1617:69496] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[1489:123256] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[2854:170082] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[28:6776] -A INPUT -i br-iot -m comment --comment "!fw3" -j zone_iot_input
[3141773:2756815927] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[3133642:2755889864] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[6025:565778] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[2106:360285] -A FORWARD -i br-iot -m comment --comment "!fw3" -j zone_iot_forward
[17611:1655099] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[1457535:1488478257] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[1448160:1487858777] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[629:82274] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[8746:537206] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o br-iot -m comment --comment "!fw3" -j zone_iot_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[1617:69496] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_iot_dest_ACCEPT -o br-iot -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_iot_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[2106:360285] -A zone_iot_forward -m comment --comment "!fw3" -j zone_iot_dest_ACCEPT
[0:0] -A zone_iot_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[28:6776] -A zone_iot_input -m comment --comment "!fw3" -j zone_iot_src_ACCEPT
[0:0] -A zone_iot_output -m comment --comment "!fw3" -j zone_iot_dest_ACCEPT
[28:6776] -A zone_iot_src_ACCEPT -i br-iot -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[629:82274] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[6025:565778] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[0:0] -A zone_lan_forward -p icmp -m comment --comment "!fw3: LAN2IOT - ICMP" -j zone_iot_dest_ACCEPT
[6025:565778] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[1489:123256] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[1489:123256] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[629:82274] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[629:82274] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[1489:123256] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[212:10934] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[14559:1092050] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[2854:170082] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2854:170082] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_ACCEPT
[8746:537206] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[8746:537206] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[1678:122121] -A zone_wan_src_ACCEPT -i eth0.2 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
COMMIT
I am not used to this, cannot read it from scratch. Anything in particular you are looking for? Would like to understand
trendy
January 11, 2021, 9:04am
16
First of all remove the gateway from iot interface.
iot zone is only allowed to forward to itself
which has the exact number of hits. So change the default policies to reject the input and forward, so the zone configuration will define what will be allowed.
1 Like
MIRC0
January 11, 2021, 12:10pm
17
removing the defaults ACCEPT lead to iot net not having internet access at all. great.
afaik I do have to activate Masquerading on my lan when I want to access from iot to lan. earlier I was recommended to deactivate this. how do I activate Masquerading for traffic from iot to lan only?
and: How do I remove a gw? If not setting a gw, luci automaticalle sets the wan ip as gw. this is why I set 192.168.187.0 as gw /which is not a gw but a dirty workaround (I thought)
trendy
January 11, 2021, 12:53pm
18
That is not the purpose of masquerade and it's not needed.
MIRC0:
How do I remove a gw?
Delete the value and hit Save/Apply.
Which is correct, the upstream router towards the internet is on wan interface.
MIRC0
January 11, 2021, 2:53pm
19
well, iot has different IP net than lan, so masq does the trick translating from one net to another... at least how I understood, not correct? so, forwarding from particular servers from iot to lan and vice versa means I have to deal with to nets.
MIRC0
January 11, 2021, 2:56pm
20
thank you trendy, it all works now. I can manage per server/port/net what traffic goes where. good feeling
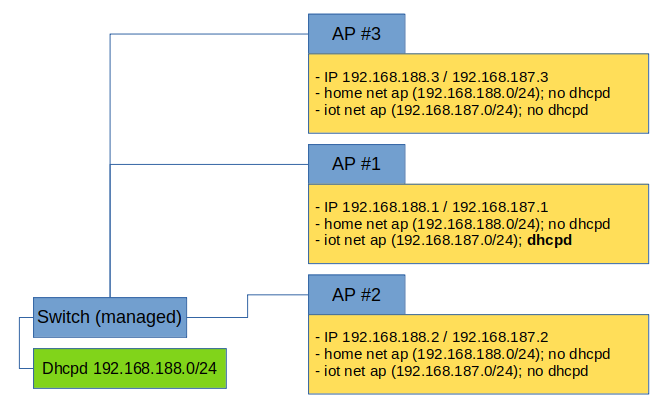
 I recently setup up three wifi ap (tp-link ac1750 each). I want to isolate my iot devices from my regular home net. with one ap, no problem. Before, I already had a raspberry acting as my home net dhcp server, to keep things simple I wanted to take advantage from the dhcp abilities of openwrt and defined that iot interface on ap #1 to also act as dhcp server. here is a drawing
I recently setup up three wifi ap (tp-link ac1750 each). I want to isolate my iot devices from my regular home net. with one ap, no problem. Before, I already had a raspberry acting as my home net dhcp server, to keep things simple I wanted to take advantage from the dhcp abilities of openwrt and defined that iot interface on ap #1 to also act as dhcp server. here is a drawing