@amteza I reread the helpful posts you wrote about concerning me trying qosify. As a reminder, I have this setup:
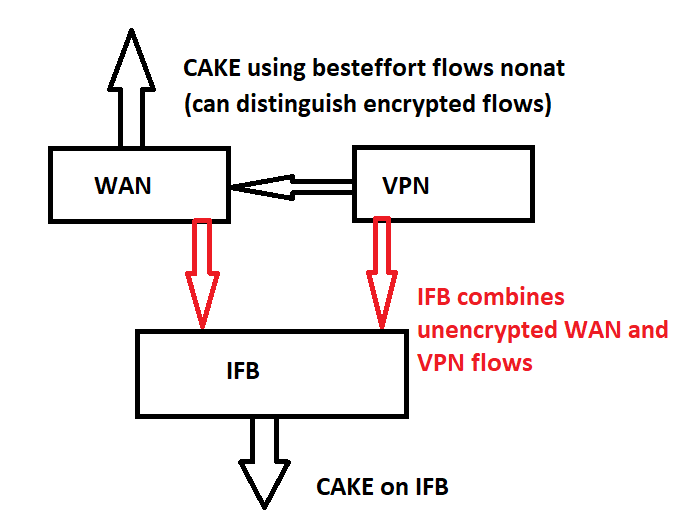
I understand that using 'flows nonat' CAKE can still differentiate encrypted flows but that this only works for upload (@moeller0?) and hence for download I set up my IFB using this script in which unencrypted packets from both WAN and VPN are combined (taking care to skip over the encrypted packets on WAN to avoid duplicates).
In any case, I think you demonstrated above how with my setup I could get qosify to effectively DSCP mark in respect of download. That is, CAKE on IFB will work with the DSCP markings applied by qosify.
But how would I get this to work in respect of upload then, mindful that the WAN interface has a mixture of encrypted and unencrypted flows?
I looked into this solution here about preserving DSCP marking across WireGuard:
This example shows how to use BPF to preserve DSCP values across an encapsulating interface such as Wireguard. It relies on the encapsulation layer preserving the skb->hash value across the encapsulation, which is commonly the case on kernel encapsulation protocols (including Wireguard).
I'm hazy on what qosify would do here. I mean if qosify DSCP marks flows for upload and I apply 'diffserv4' will CAKE correctly see DSCP markings notwithstanding mixture of encapsulated and unencrypted flows? @moeller0 any clue about this?
So already I was surprised that qosify will allow DSCP marking to work in respect of the IFB - that is good. Now I am wondering if it will also allow DSCP marking to work in respect of WAN whilst relying on skb->hash preservation for CAKE to differentiate encrypted WireGuard encapsulated flows.
Also the preserve-dscp tool above gives the following warning:
- As mentioned above, doing this in the first place LEAKS DATA! I.e., it makes it possible for an outside observer to distinguish between different types of traffic inside the tunnel. This is generally a bad idea, especially if the traffic goes across the public internet.
Would this issue also apply if I use qosify in the way I am asking about (that is assuming it is even possible)?
I hope this all makes sense. There may be an easier way to tackle mixture of encrypted and unencrypted flows and make use of DSCP markings at the same time. If you have any suggestions please let me know.
@dlakelan suggested at one point putting WAN and VPN in a different namespace and then having a sort of 'fake wan' in the global namespace (with veth interconnecting the namespaces), but whilst I really like this idea I think setting that up looks really tricky  .
.