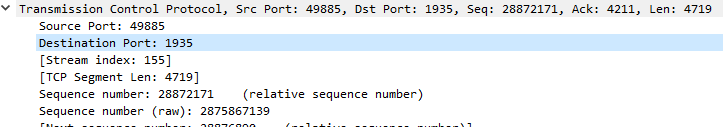
Now do the same check for the speed test.
Is it also assigned to the "Best Effort" tin? If so, then it has the same priority as the streaming.
Yes, exactly. I don't think that RTMP traffic should be in the "Best Effort" tin, right?
Right, but the higher-priority Voice tin appears to be limited to 1625Kbit.
I don't know if this limit can be changed.
I've done a little bit more researching, and found out that Tins are decided by the "diffserv" setting. Default seems to be diffserv3, I set it to diffserv8 by editing the /usr/lib/sqm/defaults.shfile and recreating the sqm interface.
Now I can see 8 tins... will test and let you know! Thanks for pointing this out to me!
Not without editing the cake kernel code and recompilation. But you can much easier change simple.qos, there the three implemented priority tiers are completely constructed/defined in /usr/lib/sqm/simple.qos.
Just make a copy of simple.qos and simple.qos.help to say my_simple.qos and my_simple.qos.help and edit both. They then will appear in the list of queue scripts....
You still can not manually set the min and max bandwidth for the tins in cake...
And there is your issue, SQM/cake default to per flow fairness (with potential per-internal-IP-fairness on top) and 4.5 Mbps simply is more than the fair share of your bandwidth. These easiest way around that is to created a modified copy of /usr/lib/sqm/simple.qos. Have a look at:
https://forum.openwrt.org/t/sqm-cake-and-being-a-twitch-streamer-upload-direction/62474/13?u=moeller0
For something similar...
Thanks for your answer!
I tried to follow the tutorial linked, but I can't make it to work.
I copied simple.qos to a new file (twitch.qos) and edited the PRIO_RATE value on the egress() function to PRIO_RATE=5000.
I have then selected the new qos from the list (keeping "cake" in the queue discipline), but it's not working at all.
Running tc -s qdisc ls dev eth0.835 returns:
qdisc cake 8052: root refcnt 2 bandwidth 6300Kbit diffserv3 triple-isolate nonat nowash no-ack-filter split-gso rtt 100.0ms noatm overhead 34
Sent 109434075 bytes 91331 pkt (dropped 846, overlimits 129150 requeues 0)
backlog 1506b 1p requeues 0
memory used: 197760b of 4Mb
capacity estimate: 6300Kbit
min/max network layer size: 28 / 1492
min/max overhead-adjusted size: 62 / 1526
average network hdr offset: 14
Bulk Best Effort Voice
thresh 393744bit 6300Kbit 1575Kbit
target 46.3ms 5.0ms 11.6ms
interval 141.3ms 100.0ms 106.6ms
pk_delay 0us 27.3ms 1.9ms
av_delay 0us 10.2ms 204us
sp_delay 0us 342us 46us
backlog 0b 1506b 0b
pkts 0 92081 99
bytes 0 110665793 10794
way_inds 0 1 0
way_miss 0 270 20
way_cols 0 0 0
drops 0 846 0
marks 0 0 0
ack_drop 0 0 0
sp_flows 0 0 2
bk_flows 0 1 0
un_flows 0 0 0
max_len 0 31626 1392
quantum 300 300 300
qdisc ingress ffff: parent ffff:fff1 ----------------
Sent 23365994 bytes 67326 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
and stream traffic does not get prioritized. I get better results by setting differv8 (still some drops as not all packets gets top priority but just some of them).
Any idea on what I'm doing wrong or missing?
Well, sorry for not mentioning that, you need to use fq_codel here, this is not set up for cake as leaf qdisc...
Still no luck... my speedtest takes over 4.5Mbps causing the stream to drop a lot of frames.
I did change the DSCP classification to 46 as per the tutorial (Note: I've also tried EF):
And set the options like this on SQM:

This is the edited part of the egress() function on twitch.qos:
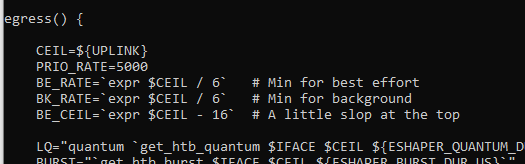
Thanks
What is the output of:
tc -s qdisc
tc -d qdisc
cat /etc/config/sqm
Also, I believe that you will need to adjust the divisors for the other classes up, so that the sum of PRIO_RATE, BE_RATE and BK_RATE stays below ceiling...
Time for packet captures ![]() try to generate some traffic that should be marked 46 or EF and take a packet capture on your router while the streaming runs. Make sue just capture for a short while or attach some additional storage to the router, as most routers are not build for storing megabytes of data. Then look at the capture file with, say, wireshark and conform that the packets are correctly dscp marked....
try to generate some traffic that should be marked 46 or EF and take a packet capture on your router while the streaming runs. Make sue just capture for a short while or attach some additional storage to the router, as most routers are not build for storing megabytes of data. Then look at the capture file with, say, wireshark and conform that the packets are correctly dscp marked....
root@Main-Router:/usr/lib/sqm# tc -s qdisc
qdisc noqueue 0: dev lo root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 0: dev eth0 root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 3047824377 bytes 3430210 pkt (dropped 0, overlimits 0 requeues 360)
backlog 0b 0p requeues 360
maxpacket 1514 drop_overlimit 0 new_flow_count 221 ecn_mark 0
new_flows_len 0 old_flows_len 0
qdisc htb 1: dev br-app root refcnt 2 r2q 10 default 0x12 direct_packets_stat 0 direct_qlen 1000
Sent 12781 bytes 124 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 120: dev br-app parent 1:12 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 1636 bytes 37 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 124 drop_overlimit 0 new_flow_count 2 ecn_mark 0
new_flows_len 0 old_flows_len 1
qdisc fq_codel 130: dev br-app parent 1:13 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 0 drop_overlimit 0 new_flow_count 0 ecn_mark 0
new_flows_len 0 old_flows_len 0
qdisc fq_codel 110: dev br-app parent 1:11 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 11145 bytes 87 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 135 drop_overlimit 0 new_flow_count 67 ecn_mark 0
new_flows_len 1 old_flows_len 0
qdisc ingress ffff: dev br-app parent ffff:fff1 ----------------
Sent 10669 bytes 169 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev eth0.2 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev br-lan root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev eth0.1 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc htb 1: dev eth0.835 root refcnt 2 r2q 10 default 0x12 direct_packets_stat 68 direct_qlen 1000
Sent 833876889 bytes 675446 pkt (dropped 2925, overlimits 1020588 requeues 0)
backlog 4532b 2p requeues 0
qdisc fq_codel 120: dev eth0.835 parent 1:12 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 833433333 bytes 674168 pkt (dropped 2925, overlimits 0 requeues 0)
backlog 4532b 2p requeues 0
maxpacket 34936 drop_overlimit 0 new_flow_count 26703 ecn_mark 0 memory_used 7392
new_flows_len 0 old_flows_len 1
qdisc fq_codel 130: dev eth0.835 parent 1:13 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 0 drop_overlimit 0 new_flow_count 0 ecn_mark 0
new_flows_len 0 old_flows_len 0
qdisc fq_codel 110: dev eth0.835 parent 1:11 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 156220 bytes 1050 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 1426 drop_overlimit 0 new_flow_count 723 ecn_mark 0
new_flows_len 1 old_flows_len 7
qdisc ingress ffff: dev eth0.835 parent ffff:fff1 ----------------
Sent 95147180 bytes 461160 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev wlan1 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev wlan0 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 0: dev tun0 root refcnt 2 limit 10240p flows 1024 quantum 1500 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 105505 bytes 1254 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 0 drop_overlimit 0 new_flow_count 0 ecn_mark 0
new_flows_len 0 old_flows_len 0
qdisc fq_codel 0: dev tap0 root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 2635747 bytes 16536 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 0 drop_overlimit 0 new_flow_count 0 ecn_mark 0
new_flows_len 0 old_flows_len 0
qdisc noqueue 0: dev wlan1-1 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc htb 1: dev ifb4eth0.835 root refcnt 2 r2q 10 default 0x10 direct_packets_stat 0 direct_qlen 32
Sent 117242820 bytes 461134 pkt (dropped 26, overlimits 74680 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 110: dev ifb4eth0.835 parent 1:10 limit 1001p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 117242820 bytes 461134 pkt (dropped 26, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 1540 drop_overlimit 0 new_flow_count 32290 ecn_mark 0
new_flows_len 0 old_flows_len 1
qdisc htb 1: dev ifb4br-app root refcnt 2 r2q 10 default 0x10 direct_packets_stat 0 direct_qlen 32
Sent 13035 bytes 169 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 110: dev ifb4br-app parent 1:10 limit 1001p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
Sent 13035 bytes 169 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
maxpacket 130 drop_overlimit 0 new_flow_count 160 ecn_mark 0
new_flows_len 1 old_flows_len 0
root@Main-Router:/usr/lib/sqm# tc -d qdisc
qdisc noqueue 0: dev lo root refcnt 2
qdisc fq_codel 0: dev eth0 root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc htb 1: dev br-app root refcnt 2 r2q 10 default 0x12 direct_packets_stat 0 ver 3.17 direct_qlen 1000
qdisc fq_codel 120: dev br-app parent 1:12 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc fq_codel 130: dev br-app parent 1:13 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc fq_codel 110: dev br-app parent 1:11 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc ingress ffff: dev br-app parent ffff:fff1 ----------------
qdisc noqueue 0: dev eth0.2 root refcnt 2
qdisc noqueue 0: dev br-lan root refcnt 2
qdisc noqueue 0: dev eth0.1 root refcnt 2
qdisc htb 1: dev eth0.835 root refcnt 2 r2q 10 default 0x12 direct_packets_stat 68 ver 3.17 direct_qlen 1000
linklayer ethernet overhead 34
qdisc fq_codel 120: dev eth0.835 parent 1:12 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc fq_codel 130: dev eth0.835 parent 1:13 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc fq_codel 110: dev eth0.835 parent 1:11 limit 1001p flows 1024 quantum 300 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc ingress ffff: dev eth0.835 parent ffff:fff1 ----------------
qdisc noqueue 0: dev wlan1 root refcnt 2
qdisc noqueue 0: dev wlan0 root refcnt 2
qdisc fq_codel 0: dev tun0 root refcnt 2 limit 10240p flows 1024 quantum 1500 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc fq_codel 0: dev tap0 root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc noqueue 0: dev wlan1-1 root refcnt 2
qdisc htb 1: dev ifb4eth0.835 root refcnt 2 r2q 10 default 0x10 direct_packets_stat 0 ver 3.17 direct_qlen 32
linklayer ethernet overhead 34
qdisc fq_codel 110: dev ifb4eth0.835 parent 1:10 limit 1001p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
qdisc htb 1: dev ifb4br-app root refcnt 2 r2q 10 default 0x10 direct_packets_stat 0 ver 3.17 direct_qlen 32
qdisc fq_codel 110: dev ifb4br-app parent 1:10 limit 1001p flows 1024 quantum 1514 target 5.0ms interval 100.0ms memory_limit 4Mb ecn
root@Main-Router:/usr/lib/sqm# cat /etc/config/sqm
config queue 'eth1'
option qdisc 'fq_codel'
option script 'simple.qos'
option qdisc_advanced '0'
option linklayer 'none'
option interface 'br-app'
option download '3400'
option upload '8200'
option debug_logging '0'
option verbosity '5'
option enabled '1'
config queue
option debug_logging '0'
option verbosity '5'
option enabled '1'
option interface 'eth0.835'
option download '26000'
option qdisc_advanced '0'
option linklayer 'ethernet'
option overhead '34'
option upload '6000'
option qdisc 'fq_codel'
option script 'twitch.qos'
I've installed tcpdump-mini on the router, and trying to do what you asked.
I found this command online, but no packet gets captured.
tcpdump -nni br-lan -v 'ip[1] & 0xfc == 46'
By listening normally with tcpdump -n -i br-lan
I get these packets:
16:50:12.190771 IP 192.168.12.110.60999 > 52.223.200.13.1935: Flags [.], seq 493344:494796, ack 17, win 64108, length 1452
16:50:12.190951 IP 192.168.12.110.60999 > 52.223.200.13.1935: Flags [P.], seq 494796:496600, ack 17, win 64108, length 1804
Not sure how to check if the DSCP flag is set.
Thanks for your patience
Ok, found a way to export to file, analyzed it with Wireshark and... nope. DSCP Value is AF43 for those packets, and not EF
I tried everything... seems that all my settings to get DSCP tagging are ignored
Well, are the marked packets directed to the marked port? Maybe you could try to set the dscps on your twitch streaming machine first.
It seems so
I did tried to set up dscp on my machine, but seems it's not working either... I've used this command on a superuser powershell:
New-NetQosPolicy -Name "twitch" -AppPathNameMatchCondition "obs64.exe" -PolicyStore ActiveStore -NetworkProfile All -DSCPAction 46
If you run wireshark on the windows machine to capture obs64's egress traffic what does it show?
Is the iptables rule executed at all? Can you check its counters?
iptables-save | grep dscp does not return anythins, so i'm not totally sure that the Traffic Rule is created:
The full output of iptables-save is:
root@Main-Router:~# iptables-save
# Generated by iptables-save v1.8.3 on Thu Jul 2 10:59:27 2020
*nat
:PREROUTING ACCEPT [5613:874625]
:INPUT ACCEPT [1609:109433]
:OUTPUT ACCEPT [796:53669]
:POSTROUTING ACCEPT [9:1215]
:postrouting_app_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_vpn_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_app_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_vpn_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_app_postrouting - [0:0]
:zone_app_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_vpn_postrouting - [0:0]
:zone_vpn_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i br-app -m comment --comment "!fw3" -j zone_app_prerouting
-A PREROUTING -i eth0.835 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i tun0 -m comment --comment "!fw3" -j zone_vpn_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o br-app -m comment --comment "!fw3" -j zone_app_postrouting
-A POSTROUTING -o eth0.835 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o tun0 -m comment --comment "!fw3" -j zone_vpn_postrouting
-A zone_app_postrouting -m comment --comment "!fw3: Custom app postrouting rule chain" -j postrouting_app_rule
-A zone_app_prerouting -m comment --comment "!fw3: Custom app prerouting rule chain" -j prerouting_app_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_postrouting -s 192.168.12.0/24 -d 192.168.12.1/32 -p tcp -m tcp --dport 12225 -m comment --comment "!fw3: HomeVPN (reflection)" -j SNAT --to-source 192.168.12.1
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_lan_prerouting -s 192.168.12.0/24 -d 192.168.10.2/32 -p tcp -m tcp --dport 12225 -m comment --comment "!fw3: HomeVPN (reflection)" -j DNAT --to-destination 192.168.12.1:12225
-A zone_vpn_postrouting -m comment --comment "!fw3: Custom vpn postrouting rule chain" -j postrouting_vpn_rule
-A zone_vpn_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_vpn_prerouting -m comment --comment "!fw3: Custom vpn prerouting rule chain" -j prerouting_vpn_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
-A zone_wan_prerouting -p tcp -m tcp --dport 12225 -m comment --comment "!fw3: HomeVPN" -j DNAT --to-destination 192.168.12.1:12225
COMMIT
# Completed on Thu Jul 2 10:59:27 2020
# Generated by iptables-save v1.8.3 on Thu Jul 2 10:59:27 2020
*raw
:PREROUTING ACCEPT [141974:103002838]
:OUTPUT ACCEPT [5425:1134825]
:zone_app_helper - [0:0]
:zone_lan_helper - [0:0]
-A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
-A PREROUTING -i br-app -m comment --comment "!fw3: app CT helper assignment" -j zone_app_helper
COMMIT
# Completed on Thu Jul 2 10:59:27 2020
# Generated by iptables-save v1.8.3 on Thu Jul 2 10:59:27 2020
*mangle
:PREROUTING ACCEPT [141981:103003118]
:INPUT ACCEPT [6061:545676]
:FORWARD ACCEPT [133546:101998069]
:OUTPUT ACCEPT [5436:1136721]
:POSTROUTING ACCEPT [138626:103119326]
-A FORWARD -o eth0.835 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone vpn MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Thu Jul 2 10:59:27 2020
# Generated by iptables-save v1.8.3 on Thu Jul 2 10:59:27 2020
*filter
:INPUT ACCEPT [1:40]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_app_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_vpn_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_app_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_vpn_rule - [0:0]
:input_wan_rule - [0:0]
:output_app_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_vpn_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_app_dest_ACCEPT - [0:0]
:zone_app_dest_REJECT - [0:0]
:zone_app_forward - [0:0]
:zone_app_input - [0:0]
:zone_app_output - [0:0]
:zone_app_src_ACCEPT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_REJECT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_vpn_dest_ACCEPT - [0:0]
:zone_vpn_dest_REJECT - [0:0]
:zone_vpn_forward - [0:0]
:zone_vpn_input - [0:0]
:zone_vpn_output - [0:0]
:zone_vpn_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i br-app -m comment --comment "!fw3" -j zone_app_input
-A INPUT -i eth0.835 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i tun0 -m comment --comment "!fw3" -j zone_vpn_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i br-app -m comment --comment "!fw3" -j zone_app_forward
-A FORWARD -i eth0.835 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_vpn_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o br-app -m comment --comment "!fw3" -j zone_app_output
-A OUTPUT -o eth0.835 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_vpn_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_app_dest_ACCEPT -o br-app -m comment --comment "!fw3" -j ACCEPT
-A zone_app_dest_REJECT -o br-app -m comment --comment "!fw3" -j reject
-A zone_app_forward -m comment --comment "!fw3: Custom app forwarding rule chain" -j forwarding_app_rule
-A zone_app_forward -m comment --comment "!fw3: Zone app to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_app_forward -m comment --comment "!fw3: Zone app to vpn forwarding policy" -j zone_vpn_dest_ACCEPT
-A zone_app_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_app_forward -m comment --comment "!fw3" -j zone_app_dest_REJECT
-A zone_app_input -m comment --comment "!fw3: Custom app input rule chain" -j input_app_rule
-A zone_app_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_app_input -m comment --comment "!fw3" -j zone_app_src_ACCEPT
-A zone_app_output -m comment --comment "!fw3: Custom app output rule chain" -j output_app_rule
-A zone_app_output -m comment --comment "!fw3" -j zone_app_dest_ACCEPT
-A zone_app_src_ACCEPT -i br-app -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_REJECT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_vpn_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_vpn_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
-A zone_vpn_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
-A zone_vpn_forward -m comment --comment "!fw3: Custom vpn forwarding rule chain" -j forwarding_vpn_rule
-A zone_vpn_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_vpn_forward -m comment --comment "!fw3" -j zone_vpn_dest_REJECT
-A zone_vpn_input -m comment --comment "!fw3: Custom vpn input rule chain" -j input_vpn_rule
-A zone_vpn_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_vpn_input -m comment --comment "!fw3" -j zone_vpn_src_REJECT
-A zone_vpn_output -m comment --comment "!fw3: Custom vpn output rule chain" -j output_vpn_rule
-A zone_vpn_output -m comment --comment "!fw3" -j zone_vpn_dest_ACCEPT
-A zone_vpn_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
-A zone_wan_dest_ACCEPT -o eth0.835 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o eth0.835 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o eth0.835 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m limit --limit 5/sec -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i eth0.835 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Thu Jul 2 10:59:27 2020
I'm trying to create a command manually, but not sure how to do that (found different examples online but none of them seems to work)