Hi I'm stuck on trying to connect my Convexa B1300 router, when in my first try to connect internet I got Connection attempt failed after I press restart button on interface menu it becomes USER_REQUEST error, I suspect PADO error on my log which for some reason fails but I think I'm missing something but couldn't figure out my anybody has an idea?
Edit: deleted my previous post due to sensitive information in conf
I don't sure if could be related but in https://openwrt.org/toh/gl.inet/gl-b1300 it shows my switch interface has a WAN option but in my setup there is no WAN even I tried to setup via /etc/config/network OpenWRT says internet device is not found
my steps looks like this
-
Gpon terminal connects to router's WAN
-
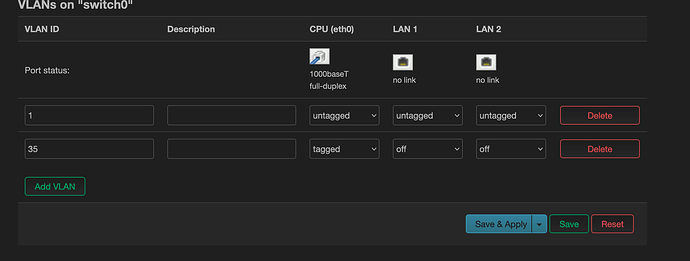
Assign VLAD ID to my WAN0 via LuCI
-
I'm entering PPPoE credentials with appropriate VLAN ID
-
got error says Connection attempt failed in WAN interface
Things I tried but didn't solve the problem
-
Override MAC
-
Reset to factory defaults
-
using original firmware to connect (which is also based open WRT) PPPoE
-
copy paste my ISP (which is Turk Telekom) configuration from https://openwrt.org/docs/guide-user/network/wan/isp-configurations
-
flash to OpenWRT 19.7.x do all steps again
My config
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd01:6f89:263c::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'pppoe'
option device 'eth0.35'
option username 'xxxx'
option password 'xxxx'
option ipv6 'auto'
option keepalive '10 1'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 3 4'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t'
option vid '35'
config device
option name 'eth0'
config device
option name 'eth0.35'
option type '8021q'
option ifname 'eth0'
option vid '35'
option mtu '1500'
My Logs Before the restart interfacace (boot time)
Tue Jan 3 00:30:27 2023 kern.info kernel: [ 378.972517] br-lan: port 2(wlan1) entered forwarding state
Tue Jan 3 00:30:27 2023 daemon.notice hostapd: wlan1: interface state HT_SCAN->ENABLED
Tue Jan 3 00:30:27 2023 daemon.notice hostapd: wlan1: AP-ENABLED
Tue Jan 3 00:30:27 2023 daemon.notice netifd: Wireless device 'radio1' is now up
Tue Jan 3 00:30:27 2023 daemon.notice netifd: Network device 'wlan1' link is up
Tue Jan 3 00:30:41 2023 daemon.info hostapd: wlan1: STA 1c:91:80:d4:34:0b IEEE 802.11: authenticated
Tue Jan 3 00:30:41 2023 daemon.info hostapd: wlan1: STA 1c:91:80:d4:34:0b IEEE 802.11: associated (aid 1)
Tue Jan 3 00:30:41 2023 daemon.notice hostapd: wlan1: AP-STA-CONNECTED 1c:91:80:d4:34:0b
Tue Jan 3 00:30:41 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 1c:91:80:d4:34:0b
Tue Jan 3 00:30:41 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 1c:91:80:d4:34:0b
Tue Jan 3 00:30:47 2023 user.info : luci: accepted login on /admin/system/flash for root from 192.168.1.220
Tue Jan 3 00:31:17 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Jan 3 00:31:17 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Tue Jan 3 00:31:17 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 1 addresses
Tue Jan 3 00:31:17 2023 daemon.info dnsmasq-dhcp[1]: read /etc/ethers - 0 addresses
Tue Jan 3 00:32:09 2023 daemon.notice netifd: wan (2106): udhcpc: received SIGTERM
Tue Jan 3 00:32:09 2023 daemon.notice netifd: wan (2106): udhcpc: unicasting a release of 10.215.168.215 to 10.98.67.50
Tue Jan 3 00:32:09 2023 daemon.notice netifd: wan (2106): udhcpc: sending release
Tue Jan 3 00:32:09 2023 daemon.notice netifd: wan (2106): udhcpc: entering released state
Tue Jan 3 00:32:09 2023 daemon.notice netifd: wan (2106): Command failed: ubus call network.interface notify_proto { "action": 0, "link-up": false, "keep": false, "interface": "wan" } (Permission denied)
Tue Jan 3 00:32:09 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:32:09 2023 daemon.notice netifd: Interface 'wan' has link connectivity loss
Tue Jan 3 00:32:09 2023 daemon.notice netifd: VLAN 'eth0.35' link is up
Tue Jan 3 00:32:09 2023 daemon.notice netifd: Interface 'wan' has link connectivity
Tue Jan 3 00:32:09 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:32:09 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:32:09 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:32:09 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:32:09 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:32:09 2023 daemon.info pppd[4166]: Plugin pppoe.so loaded.
Tue Jan 3 00:32:09 2023 daemon.info pppd[4166]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:32:09 2023 daemon.notice pppd[4166]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: exiting on receipt of SIGTERM
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: started, version 2.86 cachesize 150
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: DNS service limited to local subnets
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-cryptohash no-DNSSEC no-ID loop-detect inotify dumpfile
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: UBus support enabled: connected to system bus
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq-dhcp[1]: DHCP, IP range 192.168.1.100 -- 192.168.1.249, lease time 12h
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for test
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for onion
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for localhost
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for local
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for invalid
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for bind
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: using only locally-known addresses for lan
Tue Jan 3 00:32:11 2023 daemon.warn dnsmasq[1]: no servers found in /tmp/resolv.conf.d/resolv.conf.auto, will retry
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 1 addresses
Tue Jan 3 00:32:11 2023 daemon.info dnsmasq-dhcp[1]: read /etc/ethers - 0 addresses
Tue Jan 3 00:32:25 2023 daemon.warn pppd[4166]: Timeout waiting for PADO packets
Tue Jan 3 00:32:25 2023 daemon.err pppd[4166]: Unable to complete PPPoE Discovery
Tue Jan 3 00:32:25 2023 daemon.info pppd[4166]: Exit.
Tue Jan 3 00:32:25 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:32:25 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:32:25 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:32:25 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:32:25 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:32:25 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:32:25 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:32:25 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:32:25 2023 daemon.info pppd[4459]: Plugin pppoe.so loaded.
Tue Jan 3 00:32:25 2023 daemon.info pppd[4459]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:32:25 2023 daemon.notice pppd[4459]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:32:33 2023 authpriv.info dropbear[4534]: Child connection from 192.168.1.220:49428
Tue Jan 3 00:32:33 2023 authpriv.info dropbear[4534]: Exit before auth from <192.168.1.220:49428>: Exited normally
Tue Jan 3 00:32:40 2023 daemon.warn pppd[4459]: Timeout waiting for PADO packets
Tue Jan 3 00:32:40 2023 daemon.err pppd[4459]: Unable to complete PPPoE Discovery
Tue Jan 3 00:32:40 2023 daemon.info pppd[4459]: Exit.
Tue Jan 3 00:32:40 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:32:40 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:32:40 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:32:40 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:32:40 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:32:40 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:32:41 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:32:41 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:32:41 2023 daemon.info pppd[4587]: Plugin pppoe.so loaded.
Tue Jan 3 00:32:41 2023 daemon.info pppd[4587]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:32:41 2023 daemon.notice pppd[4587]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:32:56 2023 daemon.warn pppd[4587]: Timeout waiting for PADO packets
Tue Jan 3 00:32:56 2023 daemon.err pppd[4587]: Unable to complete PPPoE Discovery
Tue Jan 3 00:32:56 2023 daemon.info pppd[4587]: Exit.
Tue Jan 3 00:32:56 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:32:56 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:32:56 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:32:56 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:32:56 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:32:56 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:32:56 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:32:56 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:32:56 2023 daemon.info pppd[4700]: Plugin pppoe.so loaded.
Tue Jan 3 00:32:56 2023 daemon.info pppd[4700]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:32:56 2023 daemon.notice pppd[4700]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:32:59 2023 authpriv.info dropbear[4761]: Child connection from 192.168.1.220:49429
Tue Jan 3 00:33:00 2023 authpriv.notice dropbear[4761]: Auth succeeded with blank password for 'root'
My logs after the restart interface
Tue Jan 3 00:33:27 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:33:27 2023 daemon.info pppd[4938]: Plugin pppoe.so loaded.
Tue Jan 3 00:33:27 2023 daemon.info pppd[4938]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:33:28 2023 daemon.notice pppd[4938]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:33:33 2023 daemon.err pppd[4938]: select (waitForPADO): Interrupted system call
Tue Jan 3 00:33:33 2023 daemon.warn pppd[4938]: Timeout waiting for PADO packets
Tue Jan 3 00:33:33 2023 daemon.err pppd[4938]: Unable to complete PPPoE Discovery
Tue Jan 3 00:33:33 2023 daemon.info pppd[4938]: Exit.
Tue Jan 3 00:33:33 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:33:33 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:33:33 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:33:33 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:33:33 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:33:33 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:33:33 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:33:33 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:33:33 2023 daemon.info pppd[5060]: Plugin pppoe.so loaded.
Tue Jan 3 00:33:33 2023 daemon.info pppd[5060]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:33:34 2023 daemon.notice pppd[5060]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:33:49 2023 daemon.warn pppd[5060]: Timeout waiting for PADO packets
Tue Jan 3 00:33:49 2023 daemon.err pppd[5060]: Unable to complete PPPoE Discovery
Tue Jan 3 00:33:49 2023 daemon.info pppd[5060]: Exit.
Tue Jan 3 00:33:49 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:33:49 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:33:49 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:33:49 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:33:49 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:33:49 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:33:49 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:33:49 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:33:49 2023 daemon.info pppd[5175]: Plugin pppoe.so loaded.
Tue Jan 3 00:33:49 2023 daemon.info pppd[5175]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:33:49 2023 daemon.notice pppd[5175]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:34:04 2023 daemon.warn pppd[5175]: Timeout waiting for PADO packets
Tue Jan 3 00:34:04 2023 daemon.err pppd[5175]: Unable to complete PPPoE Discovery
Tue Jan 3 00:34:04 2023 daemon.info pppd[5175]: Exit.
Tue Jan 3 00:34:04 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:34:05 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:34:05 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:34:05 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:34:05 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:34:05 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:34:05 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:34:05 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:34:05 2023 daemon.info pppd[5301]: Plugin pppoe.so loaded.
Tue Jan 3 00:34:05 2023 daemon.info pppd[5301]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:34:05 2023 daemon.notice pppd[5301]: pppd 2.4.9 started by root, uid 0
Tue Jan 3 00:34:20 2023 daemon.warn pppd[5301]: Timeout waiting for PADO packets
Tue Jan 3 00:34:20 2023 daemon.err pppd[5301]: Unable to complete PPPoE Discovery
Tue Jan 3 00:34:20 2023 daemon.info pppd[5301]: Exit.
Tue Jan 3 00:34:20 2023 daemon.notice netifd: Interface 'wan' is now down
Tue Jan 3 00:34:20 2023 daemon.notice netifd: Interface 'wan' is disabled
Tue Jan 3 00:34:20 2023 daemon.notice netifd: Interface 'wan' is enabled
Tue Jan 3 00:34:20 2023 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jan 3 00:34:20 2023 daemon.err insmod: module is already loaded - slhc
Tue Jan 3 00:34:20 2023 daemon.err insmod: module is already loaded - ppp_generic
Tue Jan 3 00:34:20 2023 daemon.err insmod: module is already loaded - pppox
Tue Jan 3 00:34:20 2023 daemon.err insmod: module is already loaded - pppoe
Tue Jan 3 00:34:20 2023 daemon.info pppd[5462]: Plugin pppoe.so loaded.
Tue Jan 3 00:34:20 2023 daemon.info pppd[5462]: PPPoE plugin from pppd 2.4.9
Tue Jan 3 00:34:20 2023 daemon.notice pppd[5462]: pppd 2.4.9 started by root, uid 0
Firmware Information
OpenWRT Version: 22.03.3
Platform: ipq40xx/generic