I'd like you to try a simple configuration change.
Look for the MAC address of the ISP router...it should be on a printed label on the device.
It will be in a format that looks like "6A:1B:CD:E4:55:6F"
Copy that address down.
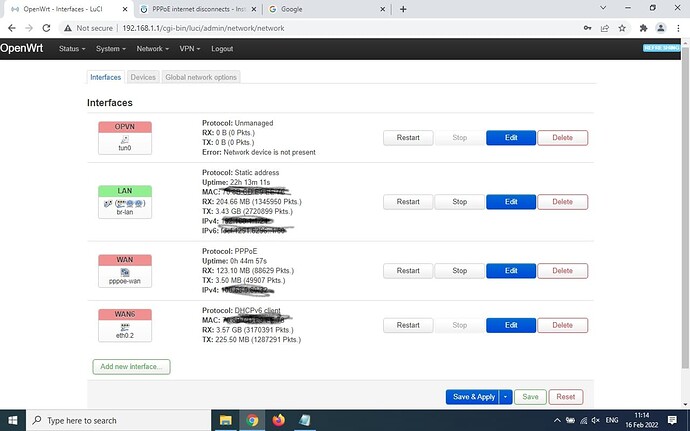
In LuCI, navigate to Network > Interfaces.
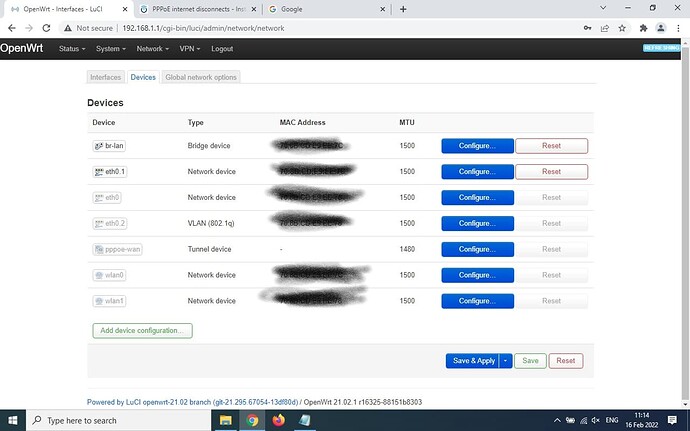
Click on the Devices tab.
Look for the device name in the list that matches what the WAN is using on the Interfaces page. (eth0.2 for example).
When you find it on the Devices page, click on the blue Configure button.
On the General Device Options page, look for the box labeled MAC address.
Enter the MAC address from the ISP device that you copied, in that box.
Double check that it's correct.
Then, click the green Save button.
Then, when your back at the Devices page, scroll down and click the blue Save and Apply button.
That's it.
Reboot the router and see if it makes a difference.
If not, you can always remove the MAC address by doing the same steps.
This is called "cloning" the MAC address.
There are cases when ISPs expect to see "their device" on their network, and when they don't, weird things can happen.
It's possible that it had been configured in the stock firmware at some point, but was not included in the backup of the stock configurations.
Or, nothing may change.
But it's simple and quick enough to try and undo if it doesn't do anything.