Sorry about the text formatting. I'm not good at writing MarkDown text.
Version: OpenWrt 18.06.4 r7808-ef686b7292, installed from official combined-ext4 image.
Hardware: Hyper-V Gen 1 VM, i3 8100, 512MiB RAM, 4GiB vhdx, running on top of Windows Server 2019
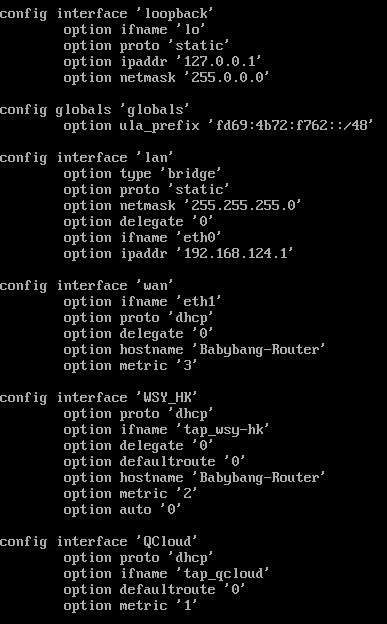
Network Adapter: 1 for WAN and 1 for LAN
Software: SoftEther VPN Server v4.22 Build 9634, Compiled 2016/11/27 14:33:59(ipk file downloaded from official OpenWrt opkg repository)
Step1. I successfully configured NAT between LAN(192.168.200.0/24) and WAN.
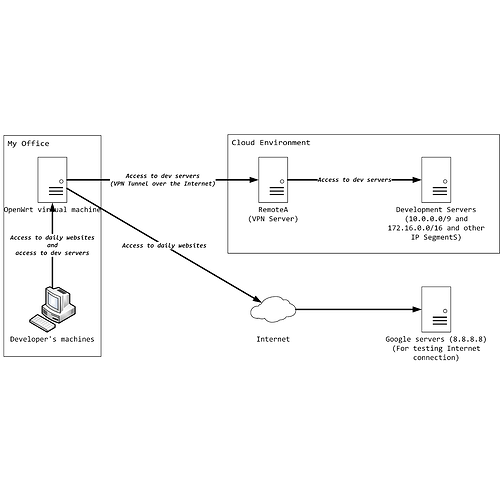
Step2. I created a virtual hub inside SoftEther VPN Server called HubA. HubA has a cascade connection to a remote server called RemoteA. RemoteA is running in NAT mode, with client DHCP range configured to 192.168.222.0/24.
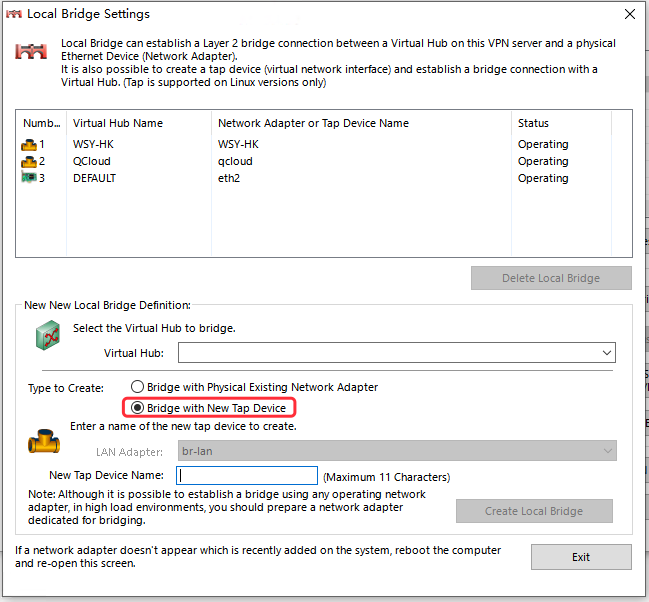
Step3. In SoftEther VPN Server, I created a bridge from HubA to tap_hub_a.
Step4. In LuCI, I configured an interface for tun_hub_a named InterfaceA. InterfaceA successfully got IP address 192.168.222.11/24 with gateway 192.168.222.1.
Step5. I configured some static routes, routing 192.168.222.0/24 and 10.0.0.0/9(reachable by RemoteA) to InterfaceA and 0.0.0.0/0 to WAN.
So far, everything works fine. From LAN side, if I ping 8.8.8.8(I just randomly picked a famous public IP address for testing Internet connectivity), my traffic goes through WAN and I got 0% packet loss. If I ping 192.168.222.1, my traffic goes through tap_hub_a and soft ether forwarded my data to RemoteA, and I also got 0% packet loss. BELOW IS WHERE THE BUG BEGINS.
Step6. I configured another static route entry, routing 172.16.0.0/16(Reachable by RemoteA) to InterfaceA. (No other configuration was changed) Then I ping 192.168.222.1, my traffic still goes through tap_hub_a to RemoteA, but I got regularly packet loss: Exactly ten successful response from RemoteA and then I got about 30 to 40 lost packets. Then another cycle: Exactly 10 successful response and it's again followed by 30 to 40 lost packets.
In each cycle, I got exactly 10 continuously successful responses and then some continuous packet loss (About 30 ~ 40 packets). However, whether I configured 172.16.0.0/16 static route entry or not, I got no problem ping 8.8.8.8 through WAN from LAN side.
Analysis:
Possibility1: Too many static route rules? Without 172.16.0.0/16 CIDR in the rules, I configured more than 10 static route rules and no bug occurred. I tried to configure 172.16.0.0/16 as the only static route rule, and still, I got regularly packet loss.
Possibility2: Is this a bug with Linux TAP device? I tried to install another virtual machine running Ubuntu 19.04 and installed SoftEther VPN Server there, and I used a Hyper-V virtual switch to connect InterfaceA to HubA, and still, I got packet loss with 192.168.222.1 and no packet loss with 8.8.8.8.
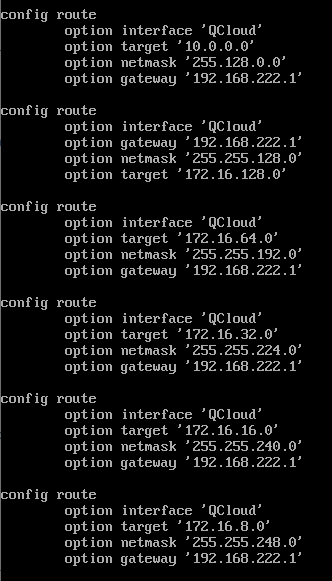
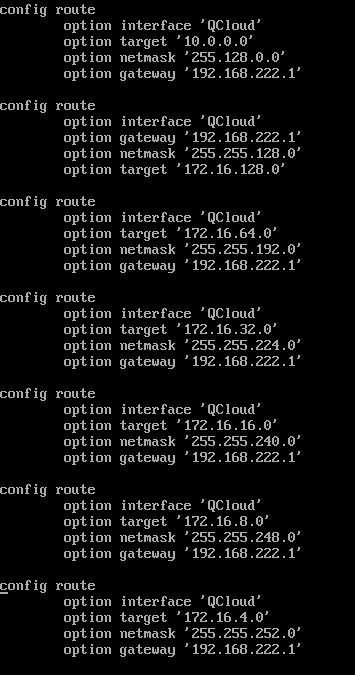
Another Attempt: I tear apart the 172.16.0.0/16 subnet into 172.16.128.0/17 + 172.16.64.0/18 + 172.16.32.0/19 + ...... + 172.16.2.0/23 + 172.16.1.0/24 + 172.16.0.0/24.
If I configure 172.16.128.0/17 into static route rules, I got no packet loss to remoteA.
If I configure 172.16.128.0/17 and 172.16.64.0/18 and all the way to 172.16.8.0/21 (5 entries), I got no packet loss to remoteA.
If I configure from 172.16.128.0/17 to 172.16.1.0/24 (8 entries), I got packet loss to remoteA.
I tried to google this problem, and I found one thread saying someone named Lintel has already fixed a regularly-packet-loss bug in hardware driver about three years ago.(That thread is in a Chinese forum)
Now, I think the bug still exists and I believe it's related to 172.16.0.0/16 CIDR.