Is the firewall on the web server configured to accept external connections?
Add section to /etc/config/firewall
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp udp'
option src_dport '7000'
option dest_ip '10.20.30.177'
option dest_port '7000'
option name 'website-TEST'
Pls. check this link, at the end of section "LAN-side public server", config rule.
I have had chance only now to check it.
Ok, understood, we have general input rules for both zones. (Thanks for the correction.)
{
"kernel": "4.14.215",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 5 (v7l)",
"model": "Raspberry Pi 2 Model B Rev 1.1",
"board_name": "raspberrypi,2-model-b",
"release": {
"distribution": "OpenWrt",
"version": "19.07.6",
"revision": "r11278-8055e38794",
"target": "brcm2708/bcm2709",
"description": "OpenWrt 19.07.6 r11278-8055e38794"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:xxxx::/48'
config interface 'wan'
option ifname 'eth0'
option proto 'dhcp'
config interface 'lan'
option proto 'static'
option ifname 'eth1'
option ipaddr '10.20.30.1'
option netmask '255.255.255.0'
option gateway '172.17.2.1'
option type 'bridge'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'eth1'
option start '100'
option limit '150'
option interface 'eth1'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option network 'wan'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp udp'
option src_dport '7000'
option dest_ip '10.20.30.177'
option dest_port '7000'
option name 'website-TEST'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Generated by iptables-save v1.8.3 on Thu Feb 11 12:30:41 2021
*nat
:PREROUTING ACCEPT [678:49744]
:INPUT ACCEPT [43:3915]
:OUTPUT ACCEPT [28:2536]
:POSTROUTING ACCEPT [1:69]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[678:49744] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[65:5378] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[613:44366] -A PREROUTING -i eth0 -m comment --comment "!fw3" -j zone_wan_prerouting
[49:3812] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[48:3743] -A POSTROUTING -o eth0 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 10.20.30.0/24 -d 10.20.30.177/32 -p tcp -m tcp --dport 7000 -m comment --comment "!fw3: website-TEST (reflection)" -j SNAT --to-source 10.20.30.1
[0:0] -A zone_lan_postrouting -s 10.20.30.0/24 -d 10.20.30.177/32 -p udp -m udp --dport 7000 -m comment --comment "!fw3: website-TEST (reflection)" -j SNAT --to-source 10.20.30.1
[65:5378] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 10.20.30.0/24 -d 172.17.2.90/32 -p tcp -m tcp --dport 7000 -m comment --comment "!fw3: website-TEST (reflection)" -j DNAT --to-destination 10.20.30.177:7000
[0:0] -A zone_lan_prerouting -s 10.20.30.0/24 -d 172.17.2.90/32 -p udp -m udp --dport 7000 -m comment --comment "!fw3: website-TEST (reflection)" -j DNAT --to-destination 10.20.30.177:7000
[48:3743] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[48:3743] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[613:44366] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 7000 -m comment --comment "!fw3: website-TEST" -j DNAT --to-destination 10.20.30.177:7000
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 7000 -m comment --comment "!fw3: website-TEST" -j DNAT --to-destination 10.20.30.177:7000
COMMIT
# Completed on Thu Feb 11 12:30:41 2021
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
inet 172.17.2.90/24 brd 172.17.2.255 scope global eth0
valid_lft forever preferred_lft forever
4: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.20.30.1/24 brd 10.20.30.255 scope global br-lan
valid_lft forever preferred_lft forever
default via 172.17.2.1 dev eth0 src 172.17.2.90
10.20.30.0/24 dev br-lan scope link src 10.20.30.1
172.17.2.0/24 dev eth0 scope link src 172.17.2.90
broadcast 10.20.30.0 dev br-lan table local scope link src 10.20.30.1
local 10.20.30.1 dev br-lan table local scope host src 10.20.30.1
broadcast 10.20.30.255 dev br-lan table local scope link src 10.20.30.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 172.17.2.0 dev eth0 table local scope link src 172.17.2.90
local 172.17.2.90 dev eth0 table local scope host src 172.17.2.90
broadcast 172.17.2.255 dev eth0 table local scope link src 172.17.2.90
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
current setting looks like this
root@OpenWrt:~# iptables-save -c -t filter | grep -e DNAT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
webserver is ubuntu se I was able to get below config
ufw status
Status: active
To Action From
-- ------ ----
Nginx HTTP ALLOW Anywhere
**7000** ALLOW Anywhere
80 ALLOW Anywhere
Nginx HTTP (v6) ALLOW Anywhere (v6)
**7000** (v6) ALLOW Anywhere (v6)
80 (v6) ALLOW Anywhere (v6)
also as I mentioned in OP,
[OK] from LAN Gateway [10.20.30.1]--> curl http://10.20.30.177:7000 Works OK
tried with no luck. see current settings here: Portforward not working to access LAN machine from WAN - #10 by vermapraveen
No hits on the firewall, nothing reached OpenWrt.
Run a tcpdump to verify if the packets indeed arrive:
opkg update; opkg install tcpdump; tcpdump -i eth0 -evn port 7000
I am trying to call OpenWrt server on port 7000 in WAN as below and expecting port forwarding will take place. Isn't this how it should be? correct me if wrong.
curl http://172.17.2.90:7000`
from
172.17.2.80 : is 1 of machine or my phone in WAN.
from WAN[172.17.2.80]: curl http://172.17.2.90:7000 Operation Timeout and not
That is correct.
Remove the gateway from the lan interface and if it doesn't fix run the tcpdump mentioned before and try it again.
root@OpenWrt:~# tcpdump -i eth0 -evn port 7000
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
13:01:08.358990 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x81f0 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488407490 ecr 0,sackOK,eol], length 0
13:01:09.351284 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x7e08 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488408490 ecr 0,sackOK,eol], length 0
13:01:10.359402 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x7a20 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488409490 ecr 0,sackOK,eol], length 0
13:01:11.353792 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x7638 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488410490 ecr 0,sackOK,eol], length 0
13:01:12.355931 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x7250 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488411490 ecr 0,sackOK,eol], length 0
13:01:13.353627 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x6e67 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488412491 ecr 0,sackOK,eol], length 0
13:01:15.356338 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x6696 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488414492 ecr 0,sackOK,eol], length 0
13:01:19.357538 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x56f6 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488418492 ecr 0,sackOK,eol], length 0
13:01:27.368257 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0x37b6 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488426492 ecr 0,sackOK,eol], length 0
13:01:43.390152 wan-client-mac > rpi-openwrt-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61751 > 172.17.2.90.7000: Flags [S], cksum 0xf935 (correct), seq 2441550657, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488442492 ecr 0,sackOK,eol], length 0
I went ahead and ran same tcpdump on eth1 also. I will admit, I don't understand tcpdump result, but I will read.
root@OpenWrt:~# tcpdump -i eth1 -evn port 7000
tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
13:05:00.669733 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x371c (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488639662 ecr 0,sackOK,eol], length 0
13:05:01.673336 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x3334 (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488640662 ecr 0,sackOK,eol], length 0
13:05:02.685141 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x2f4c (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488641662 ecr 0,sackOK,eol], length 0
13:05:03.683717 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x2b64 (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488642662 ecr 0,sackOK,eol], length 0
13:05:04.683662 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x277c (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488643662 ecr 0,sackOK,eol], length 0
13:05:05.684689 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x2394 (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488644662 ecr 0,sackOK,eol], length 0
13:05:07.683709 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x1bc4 (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488646662 ecr 0,sackOK,eol], length 0
13:05:11.691608 not-sure-whatIsThis-mac-1 > not-sure-whatIsThis-mac-2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61755 > 10.20.30.177.7000: Flags [S], cksum 0x0c23 (correct), seq 2103014646, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 488650663 ecr 0,sackOK,eol], length 0
Thanks, it is visible that now DNAT is working, and you should see hits on the firewall.
The webserver is not replying back though, so I'll ask again.
i captured 2 things on 10.20.30.177, it's ubuntu machine, and i see benefit of tcpdump
1. gateway configured
--------------------------------
route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.20.30.1 0.0.0.0 UG 20100 0 0 enp0s25
10.20.30.0 0.0.0.0 255.255.255.0 U 100 0 0 enp0s25
172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0
2. tcpdump on webserver
----------------------------------
sudo tcpdump -i enp0s25 -evn port 7000
tcpdump: listening on enp0s25, link-type EN10MB (Ethernet), capture size 262144 bytes
07:19:19.616091 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xf8ef (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489498173 ecr 0,sackOK,eol], length 0
07:19:20.618167 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xf507 (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489499173 ecr 0,sackOK,eol], length 0
07:19:21.645612 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xf11e (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489500174 ecr 0,sackOK,eol], length 0
07:19:22.613906 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xed35 (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489501175 ecr 0,sackOK,eol], length 0
07:19:23.620456 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xe94c (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489502176 ecr 0,sackOK,eol], length 0
07:19:24.619337 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xe564 (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489503176 ecr 0,sackOK,eol], length 0
07:19:26.617659 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61766 > 10.20.30.177.7000: Flags [S], cksum 0xdd93 (correct), seq 1867818880, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489505177 ecr 0,sackOK,eol], length 0
^C
7 packets captured
7 packets received by filter
0 packets dropped by kernel
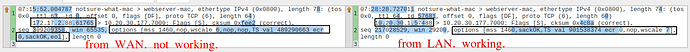
so I tried comparing tcpdump of webserver of when it's working with LAN vs when it's coming from WAN. I must say I have not fully understood, but adding it here for some expert eyes:
webserver tcpdump when it WORKS withing lan network
7:28:28.727011 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 57681, offset 0, flags [DF], proto TCP (6), length 60)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [S], cksum 0x4c8a (correct), seq 217028529, win 29200, options [mss 1460,sackOK,TS val 901538374 ecr 0,nop,wscale 7], length 0
07:28:28.727123 webserver-mac > notsure-what-mac, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.20.30.177.7000 > 10.20.30.1.57488: Flags [S.], cksum 0x5108 (incorrect -> 0xfb1d), seq 1846274689, ack 217028530, win 65160, options [mss 1460,sackOK,TS val 1488786328 ecr 901538374,nop,wscale 7], length 0
07:28:28.727900 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 57682, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [.], cksum 0x278d (correct), ack 1, win 229, options [nop,nop,TS val 901538375 ecr 1488786328], length 0
07:28:28.728002 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 147: (tos 0x0, ttl 64, id 57683, offset 0, flags [DF], proto TCP (6), length 133)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [P.], cksum 0x2fb9 (correct), seq 1:82, ack 1, win 229, options [nop,nop,TS val 901538375 ecr 1488786328], length 81
07:28:28.728055 webserver-mac > notsure-what-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 16452, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.177.7000 > 10.20.30.1.57488: Flags [.], cksum 0x5100 (incorrect -> 0x2623), ack 82, win 509, options [nop,nop,TS val 1488786329 ecr 901538375], length 0
07:28:28.732851 webserver-mac > notsure-what-mac, ethertype IPv4 (0x0800), length 2427: (tos 0x0, ttl 64, id 16453, offset 0, flags [DF], proto TCP (6), length 2413)
10.20.30.177.7000 > 10.20.30.1.57488: Flags [P.], cksum 0x5a39 (incorrect -> 0x9999), seq 1:2362, ack 82, win 509, options [nop,nop,TS val 1488786334 ecr 901538375], length 2361
07:28:28.733151 webserver-mac > notsure-what-mac, ethertype IPv4 (0x0800), length 71: (tos 0x0, ttl 64, id 16455, offset 0, flags [DF], proto TCP (6), length 57)
10.20.30.177.7000 > 10.20.30.1.57488: Flags [P.], cksum 0x5105 (incorrect -> 0xd8bc), seq 2362:2367, ack 82, win 509, options [nop,nop,TS val 1488786335 ecr 901538375], length 5
07:28:28.733779 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 57684, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [.], cksum 0x2172 (correct), ack 1449, win 251, options [nop,nop,TS val 901538381 ecr 1488786334], length 0
07:28:28.733823 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 57685, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [.], cksum 0x1dca (correct), ack 2362, win 274, options [nop,nop,TS val 901538381 ecr 1488786334], length 0
07:28:28.733835 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 57686, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [.], cksum 0x1dc4 (correct), ack 2367, win 274, options [nop,nop,TS val 901538381 ecr 1488786335], length 0
07:28:28.734897 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 57687, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [F.], cksum 0x1dc2 (correct), seq 82, ack 2367, win 274, options [nop,nop,TS val 901538382 ecr 1488786335], length 0
07:28:28.736527 webserver-mac > notsure-what-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 16456, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.177.7000 > 10.20.30.1.57488: Flags [F.], cksum 0x5100 (incorrect -> 0x1cd3), seq 2367, ack 83, win 509, options [nop,nop,TS val 1488786338 ecr 901538382], length 0
07:28:28.736995 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 57688, offset 0, flags [DF], proto TCP (6), length 52)
10.20.30.1.57488 > 10.20.30.177.7000: Flags [.], cksum 0x1dbc (correct), ack 2368, win 274, options [nop,nop,TS val 901538384 ecr 1488786338], length 0
webserver tcpdump when it DOESN'T WORKS from WAN after port forwarding
07:15:52.004787 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xfee2 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489290663 ecr 0,sackOK,eol], length 0
07:15:53.007260 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xfaf9 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489291664 ecr 0,sackOK,eol], length 0
07:15:54.006700 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xf711 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489292664 ecr 0,sackOK,eol], length 0
07:15:55.009713 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xf329 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489293664 ecr 0,sackOK,eol], length 0
07:15:56.011520 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xef41 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489294664 ecr 0,sackOK,eol], length 0
07:15:57.011657 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xeb59 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489295664 ecr 0,sackOK,eol], length 0
07:15:59.019717 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xe389 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489297664 ecr 0,sackOK,eol], length 0
07:16:03.019508 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xd3e8 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489301665 ecr 0,sackOK,eol], length 0
07:16:11.026222 notsure-what-mac > webserver-mac, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 64)
172.17.2.88.61765 > 10.20.30.177.7000: Flags [S], cksum 0xb4a7 (correct), seq 309209358, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 489309666 ecr 0,sackOK,eol], length 0
i observe, few options are missing/ not same values. Can this because of some port forwarding setting?
No, it cannot be from that, DNAT is changing the destination IP.
Check your webserver that it is not ignoring requests from IPs outside its subnet.
You can also do an SNAT to verify that:
uci add firewall nat
uci set firewall.@nat[-1].dest_port='7000'
uci set firewall.@nat[-1].src='wan'
uci set firewall.@nat[-1].name='test 7000'
uci set firewall.@nat[-1].target='SNAT'
uci set firewall.@nat[-1].dest_ip='10.20.30.177'
uci set firewall.@nat[-1].snat_ip='10.20.30.1'
uci add_list firewall.@nat[-1].proto='tcp'
uci add_list firewall.@nat[-1].proto='udp'
uci commit firewall
service firewall restart
If I understand right your point 1 (routes on Ubuntu) the traffic to 172.17/16 network will be forwarded via interface docker and not enp0s25.
First, can you remove that route?
If it will solve the issue you can check Docker later on.